
Kerberos Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
Kerberos Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
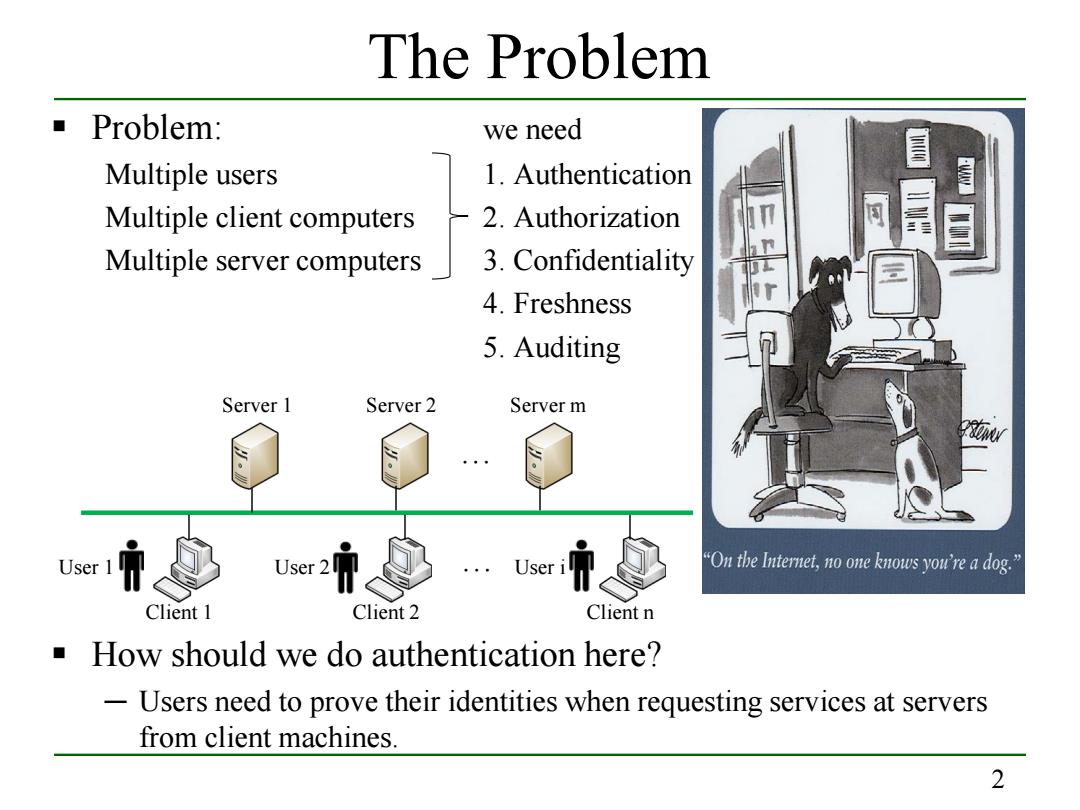
The Problem Problem: we need Multiple users 1.Authentication Multiple client computers -2.Authorization Multiple server computers 3.Confidentiality 4.Freshness 5.Auditing Server 1 Server 2 Server m "On the Internet,no one knows you're a dog." Client 1 Client 2 Client n How should we do authentication here? Users need to prove their identities when requesting services at servers from client machines. 2
2 The Problem Problem: we need Multiple users 1. Authentication Multiple client computers 2. Authorization Multiple server computers 3. Confidentiality 4. Freshness 5. Auditing How should we do authentication here? ─ Users need to prove their identities when requesting services at servers from client machines. Server 1 Server 2 Server m … Client 1 Client 2 Client n User 1 User 2 … User i

Kerberos Kerberos is an authentication and authorization protocol ■ Kerberos uses a trusted third party authentication service that enables clients and servers to establish authenticated and secure communication. ■ Kerberos provides single sign-on capability using a centralized repository of accounts. ■ Relies entirely on symmetric cryptography Kerberos provides an audit trail of usage. -How?You should be able to answer after this lecture Developed at MIT:two versions,Version 4 and Version 5 (specified as RFC1510) http://web.mit.edu/kerberos/www Used in many systems,e.g.,Windows 2000 and later as default authentication protocol In Greek mythology,Kerberos means a many headed dog, commonly three,perhaps with a serpent's tail,the guardian of the entrance of Hades." -the modern Kerberos was intended to have three components to guard a network's gate:authentication,accounting,and audit. 3
3 Kerberos Kerberos is an authentication and authorization protocol Kerberos uses a trusted third party authentication service that enables clients and servers to establish authenticated and secure communication. Kerberos provides single sign-on capability using a centralized repository of accounts. Relies entirely on symmetric cryptography Kerberos provides an audit trail of usage. ─ How? You should be able to answer after this lecture. Developed at MIT: two versions, Version 4 and Version 5 (specified as RFC1510) http://web.mit.edu/kerberos/www Used in many systems, e.g., Windows 2000 and later as default authentication protocol In Greek mythology, Kerberos means a many headed dog, commonly three, perhaps with a serpent's tail, the guardian of the entrance of Hades." ─ the modern Kerberos was intended to have three components to guard a network's gate: authentication, accounting, and audit
Requirements Security -A network eavesdropper should not be able to obtain the necessary information to impersonate a user. Transparency -Users shouldn't notice authentication taking place beyond the requirement to enter a password. Scalability -The system should be capable of supporting large numbers of clients and servers. Reliability -For all services that rely on Kerberos for access control,lack of availability of the Kerberos service means lack of availability of the supported services. 4
4 Requirements Security ─ A network eavesdropper should not be able to obtain the necessary information to impersonate a user. Transparency ─ Users shouldn’t notice authentication taking place beyond the requirement to enter a password. Scalability ─ The system should be capable of supporting large numbers of clients and servers. Reliability ─ For all services that rely on Kerberos for access control, lack of availability of the Kerberos service means lack of availability of the supported services
Threat Model User impersonation -A user may gain access to a particular workstation and pretend to be another user operating from that workstation. Network address impersonation -A user may alter the network address of a workstation so that the requests sent from the altered workstation appear to come from the impersonated workstation. Eavesdropping,tampering and replay -A user may eavesdrop on exchanges and use a replay attack to gain entrance to a server or to disrupt operations. 5
5 Threat Model User impersonation ─ A user may gain access to a particular workstation and pretend to be another user operating from that workstation. Network address impersonation ─ A user may alter the network address of a workstation so that the requests sent from the altered workstation appear to come from the impersonated workstation. Eavesdropping, tampering and replay ─ A user may eavesdrop on exchanges and use a replay attack to gain entrance to a server or to disrupt operations