
Hashes and Message Digests Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
Hashes and Message Digests Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
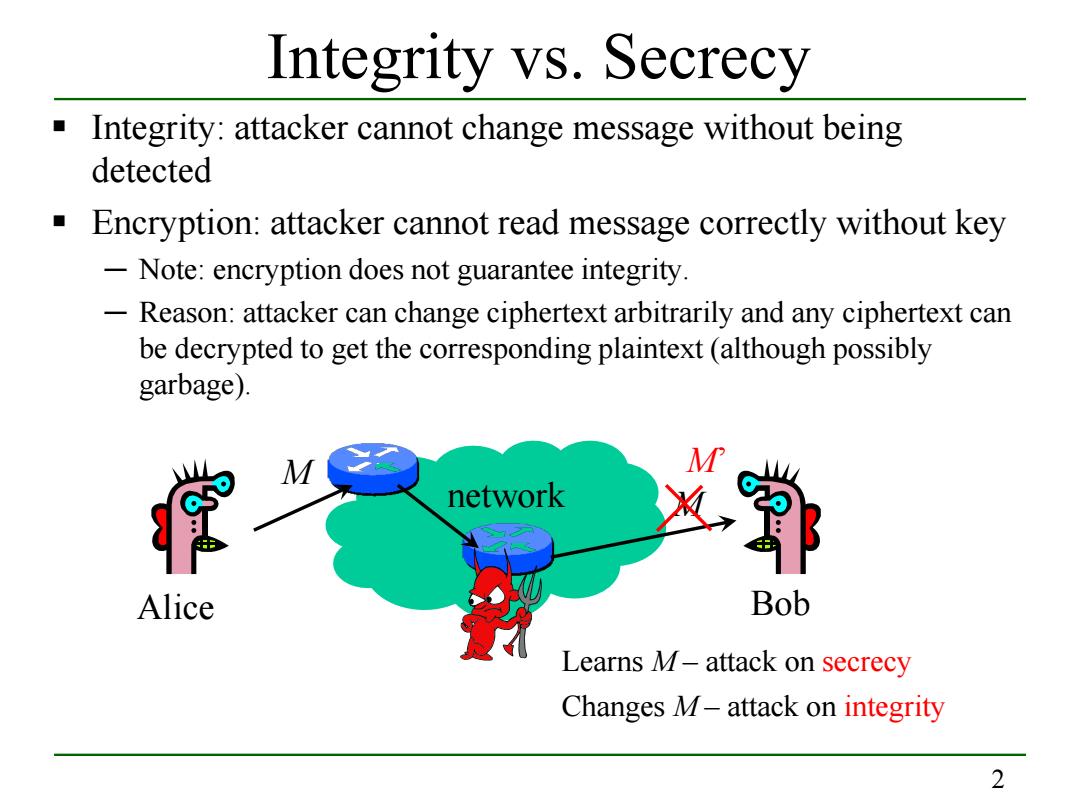
Integrity vs.Secrecy Integrity:attacker cannot change message without being detected Encryption:attacker cannot read message correctly without key -Note:encryption does not guarantee integrity. Reason:attacker can change ciphertext arbitrarily and any ciphertext can be decrypted to get the corresponding plaintext(although possibly garbage). M network Alice Bob Learns M-attack on secrecy Changes M-attack on integrity 2
2 Integrity vs. Secrecy Integrity: attacker cannot change message without being detected Encryption: attacker cannot read message correctly without key ─ Note: encryption does not guarantee integrity. ─ Reason: attacker can change ciphertext arbitrarily and any ciphertext can be decrypted to get the corresponding plaintext (although possibly garbage). network Learns M – attack on secrecy Alice Bob M M Changes M – attack on integrity M’
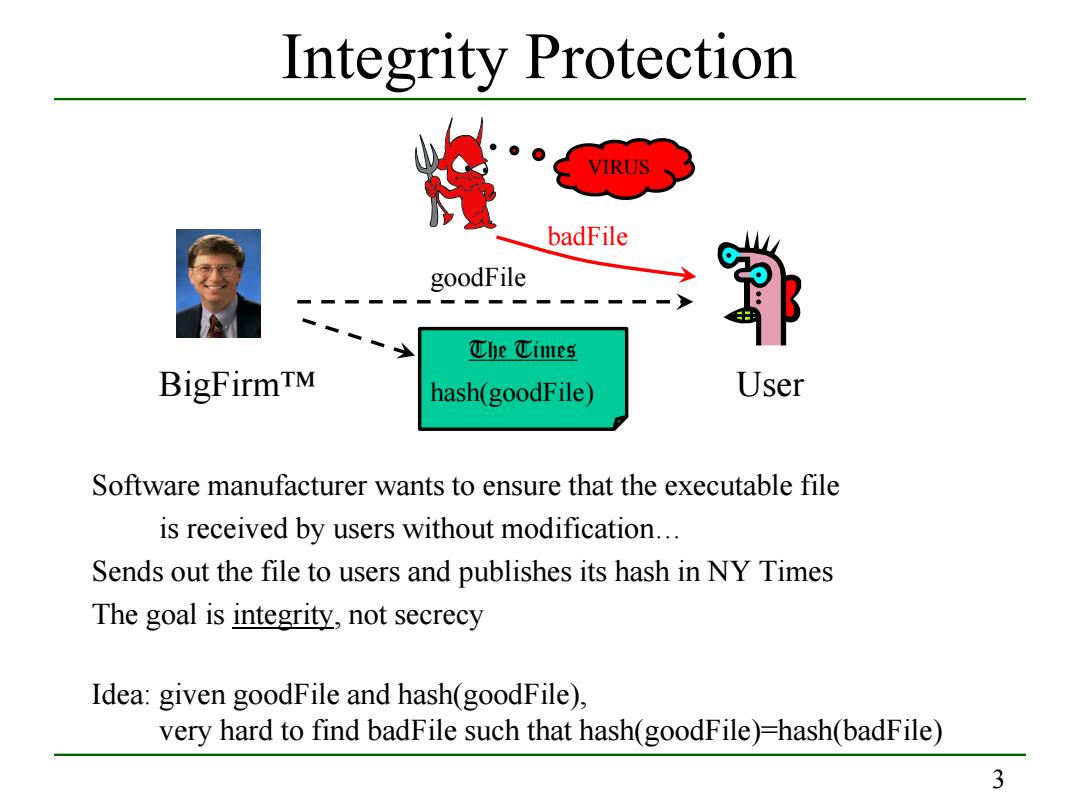
Integrity Protection VIRUS badFile goodFile ①小e①ites BigFirmTM hash(goodFile) User Software manufacturer wants to ensure that the executable file is received by users without modification... Sends out the file to users and publishes its hash in NY Times The goal is integrity,not secrecy Idea:given goodFile and hash(goodFile), very hard to find badFile such that hash(goodFile)-hash(badFile) 3
3 Integrity Protection Software manufacturer wants to ensure that the executable file is received by users without modification… Sends out the file to users and publishes its hash in NY Times The goal is integrity, not secrecy Idea: given goodFile and hash(goodFile), very hard to find badFile such that hash(goodFile)=hash(badFile) goodFile BigFirm™ User VIRUS badFile The Times hash(goodFile)
Authentication Authenticity is identification and assurance of origin of information -We'll see many specific examples in different scenarios network 第 4
4 Authentication Authenticity is identification and assurance of origin of information ─ We’ll see many specific examples in different scenarios network

Authentication with Shared Secrets SECRET SECRET msg,H(SECRET,msg) Alice Bob Alice wants to ensure that nobody modifies message in transit (both integrity and authentication) Idea:given msg, very hard to compute H(SECRET,msg)without SECRET; easy with SECRET 5
5 Authentication with Shared Secrets Alice wants to ensure that nobody modifies message in transit (both integrity and authentication) Idea: given msg, very hard to compute H(SECRET, msg) without SECRET; easy with SECRET msg, H( SECRET, msg ) Alice Bob SECRET SECRET