
Firewall Design Methods Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
Firewall Design Methods Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University

Security Guard for Private Buildings 5G0 2
2 Security Guard for Private Buildings
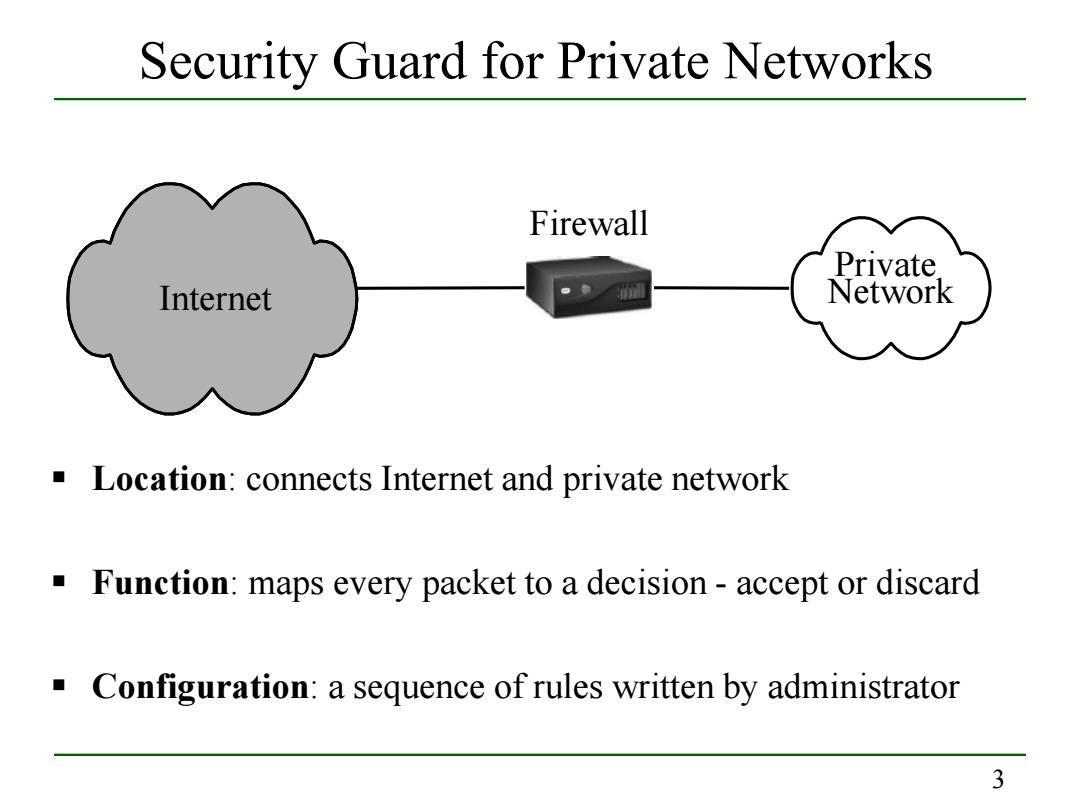
Security Guard for Private Networks Firewall Private. Internet Network Location:connects Internet and private network Function:maps every packet to a decision-accept or discard Configuration:a sequence of rules written by administrator 3
3 Security Guard for Private Networks Location: connects Internet and private network Function: maps every packet to a decision - accept or discard Configuration: a sequence of rules written by administrator Internet Private Network Firewall
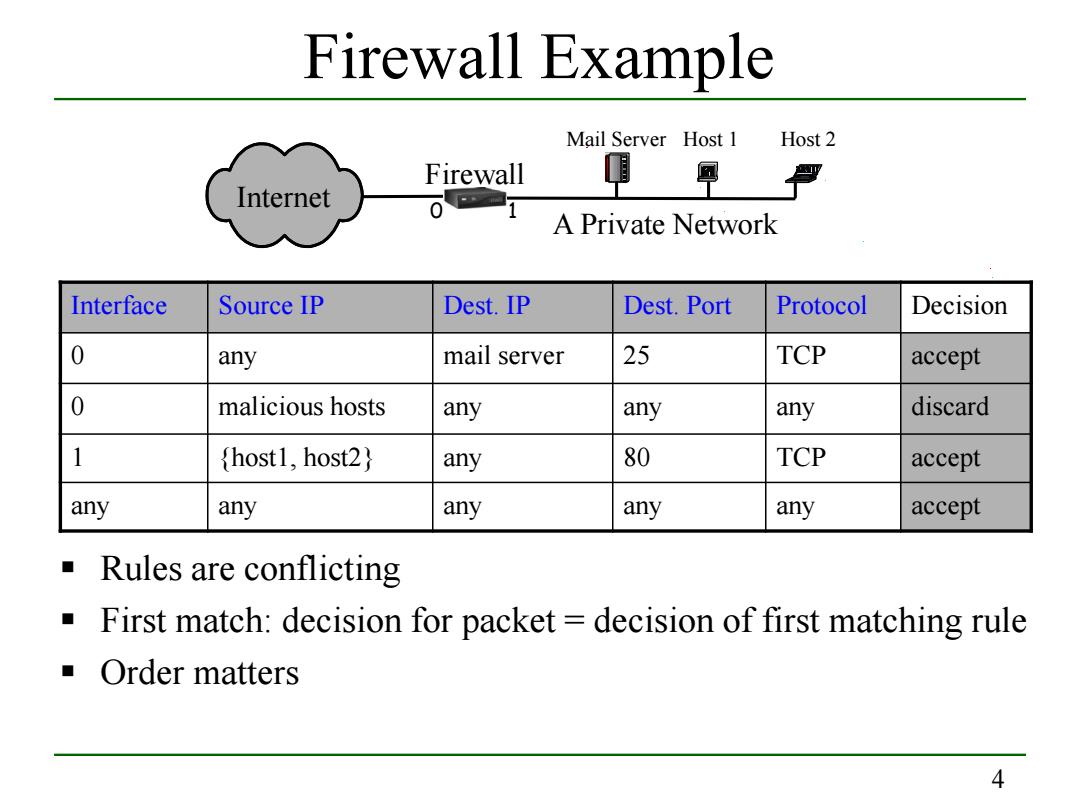
Firewall Example Mail Server Host 1 Host 2 Firewall Internet A Private Network Interface Source IP Dest.IP Dest.Port Protocol Decision 0 any mail server 25 TCP accept 0 malicious hosts any any any discard host1,host2) any 80 TCP accept any any any any any accept Rules are conflicting First match:decision for packet=decision of first matching rule ■Order matters 4
4 Firewall Example Interface Source IP Dest. IP Dest. Port Protocol Decision 0 any mail server 25 TCP accept 0 malicious hosts any any any discard 1 {host1, host2} any 80 TCP accept any any any any any accept Internet Firewall 0 1 Mail Server Host 1 Host 2 A Private Network Rules are conflicting First match: decision for packet = decision of first matching rule Order matters

Real-life Firewalls are Complex 523:conduit pernit tep host 100.77.28.87 eq 8100 any 524:conduit pernit tcp host 100.77.28.87 eq 8110 any Number of rules can be large 525:conduit pernit tcp host 100.77.28.84 eq ftp host 207.115.175.244 526:conduit pernit tcp host 100.77.28.84 eq telnet host 198.215.163.20 527:conduit pernit tep host 100.77.28.84 eq ftp host 198.215.163.20 Legacy rules 528:conduit pernit tep host 100.77.28.84 eq telnet host 198.215.163.21 529:conduit permit tep host 100.77.28.84 eq ftp host 198.215.163.21 530:conduit pernit tcp host 100.77.28.87 eq www host 207.115.175.244 Cascade impact of change 531:conduit pernit tcp host 100.77.28.87 eq telnet host 207.115.175.244 532:conduit pernit tcp ho3t100.77.28.87eq443ho3t207.115.175.244 533:conduit pernit tep host 100.77.28.87 eq ftp host 207.115.175.244 534:conduit pernit tep host 100.77.28.87 eq www host 205.170.235.0 535:conduit pernit tcp host 100.77.28.87 eq 443 host 205.170.235.0 536:conduit pernit tep host 100.77.28.87 eq ftp host 198.215.163.20 537:conduit permit tcp host 100.77.28.87 eq ftp host 198.215.163.21 538:conduit pernit tcp host 100.77.28.88 eq telnet 12.20.51.0 255.255.255.0 539:conduit permit tcp host100.77.28.88 eq ftp12.20.51.0255.255.255.0 540:conduit pernit tcp host100.77.28.88 eq www12.20.51.0255.255.255.0 541:conduit pernit tcp hos3t100.77.28.88eg1329212.20.51.0255.255.255.0 542:conduit pernit tcp host100.77.28.88eq44312.20.51.0255.255.255.0 543:conduit pernit tcp host 100.77.28.84 eq telnet 12.20.51.0 255.255.255.0 544:conduit permit tep host100.77.28.84 eq ftp12.20.51.0255.255.255.0 545:conduit pernit tcp ho3t100.77.28.85 eq wwnw12.20.51.0255.255.255.0 546:conduit permit tcp host 100.77.28.85 eq telnet 12.20.51.0 255.255.255.0 547:conduit pernit tcp host100.77.28.85eq44312.20.51.0255.255.255.0 548:conduit pernit tcp host100.77.28.85 eq ftp12.20.51.0255.255.255.0 549:conduit permit tcp host100.77.28.87eqnw12.20.51.0255.255.255.0 550:conduit pernit tcp host 100.77.28.87 eq telnet 12.20.51.0 255.255.255.0 5E1.i+++100 77 29 97443 19 90 E1 0 255255 O55 n 5
5 Real-life Firewalls are Complex Number of rules can be large Legacy rules Cascade impact of change