
Secure Socket Layer (SSL)/ TLS (Transport Layer Security) Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
Secure Socket Layer (SSL) / TLS (Transport Layer Security) Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
SSL/TLS By far,SSL/TLS is the dominant security technology on the web Provide transport layer security -Any TCP/IP application can be protected by using SSL.For example, FTP communication or Telnet or HTTP communication can be protected by using SSL. -HTTPS is HTTP over SSL Responsible for the emergence of e-commerce,other security sensitive services on the web Beneficiary of several years of public scrutiny 2
2 SSL/TLS By far, SSL/TLS is the dominant security technology on the web Provide transport layer security ─ Any TCP/IP application can be protected by using SSL. For example, FTP communication or Telnet or HTTP communication can be protected by using SSL. ─ HTTPS is HTTP over SSL Responsible for the emergence of e-commerce, other security sensitive services on the web Beneficiary of several years of public scrutiny
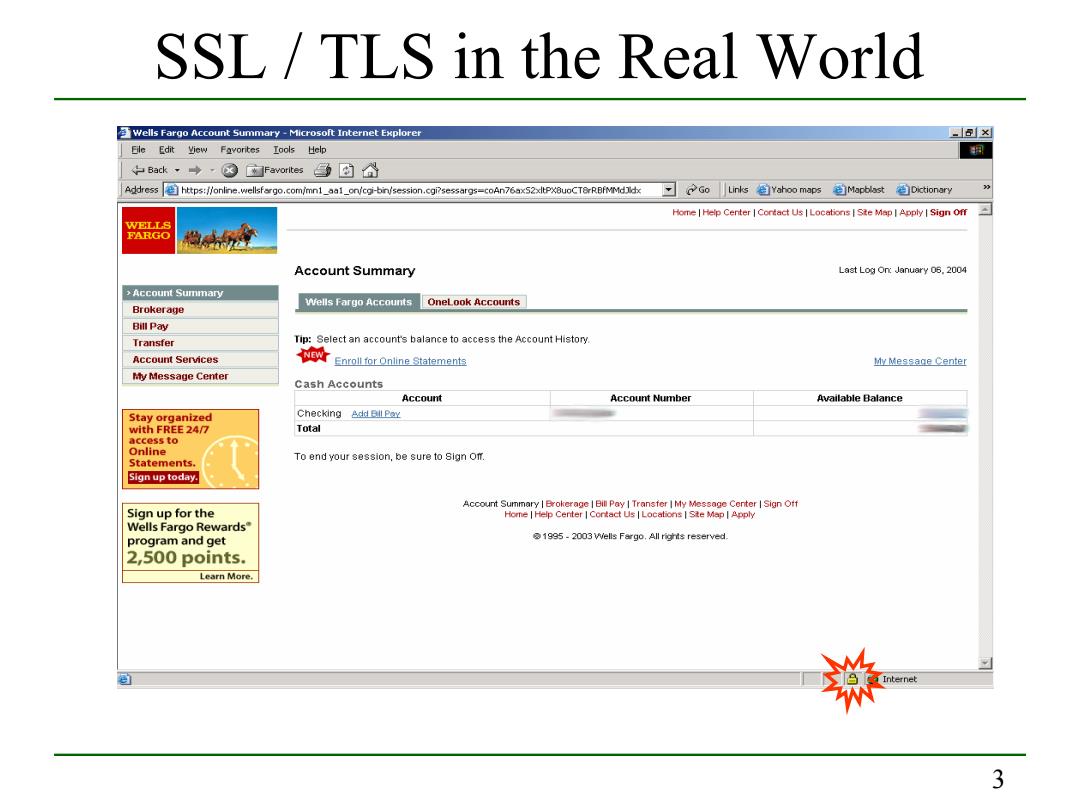
SSL/TLS in the Real World Wells Fargo Account Summary -Microsoft Internet Explorer ×☒ Eile Edit Yiew Favorites Iools Help 中Back·→,⑧Favorites固} Address https://online.wellsfargo.com/mn1__on/cgi-bin/session.cgi7sessargs-coAn76ax52xitPxBuoCTrRBfMMdidxGo LinksYahoo mapsMapblastDictionary Home Help Center|Cortact Us Locations I Ste Map I Apply I Sign off T写 FARGO 物 Account Summary Last Log On:January 06,2004 >Account Summary Brokerage Wells Fargo Accounts OneLook Accounts Bill Pay Transfer Tip:Select an account's balance to access the Account History. Account Services 前roS鱼 My Message Center My Message Center Cash Accounts Account Account Number Available Balance Stay organized Checking色d Bll Pey with FREE 24/7 Total access to Online To end your session,be sure to Sign Om. Statements. Sign up today. Account Summary Brokerage Bill Pay Transfer I My Message Center Sign Otf Sign up for the Home Help Center Cortact Us Locations I Ste Map Apply Wells Fargo Rewards" program and get 1995-2003 Wells Fargo.All rights reserved. 2,500 points. Learn More. 3
3 SSL / TLS in the Real World

History of the Protocol ■SSL1.0 -Internal Netscape design.Never deployed. The idea was proposed in Thomas Y.C.Woo,Raghuram Bindignavle,Shaowen Su, and Simon S.Lam,"SNP:An Interface for Secure Network Programming," USENIX 1994. ■SSL2.0 Published by Netscape,November 1994 Several weaknesses Microsoft improved upon SSL v2,and call it PCT(Private Communication Technology). ■SSL3.0 Designed by Netscape and Paul Kocher,November 1996 SSL v3 is deployed in nearly every Web browser. TLS(Transport Layer Security)1.0 by IETF. Internet standard based on SSL 3.0,January 1999 -Not interoperable with SSL 3.0 4
4 History of the Protocol SSL 1.0 ─ Internal Netscape design. Never deployed. ─ The idea was proposed in Thomas Y. C. Woo, Raghuram Bindignavle, Shaowen Su, and Simon S. Lam, "SNP: An Interface for Secure Network Programming," USENIX 1994. SSL 2.0 ─ Published by Netscape, November 1994 ─ Several weaknesses Microsoft improved upon SSL v2, and call it PCT (Private Communication Technology). SSL 3.0 ─ Designed by Netscape and Paul Kocher, November 1996 ─ SSL v3 is deployed in nearly every Web browser. TLS (Transport Layer Security) 1.0 by IETF. ─ Internet standard based on SSL 3.0, January 1999 ─ Not interoperable with SSL 3.0
RFC:Request for Comments Network protocols are usually disseminated in the form of an RFC TLS version 1.0 is described in RFC 2246 Intended to be a self-contained definition of the protocol -Describes the protocol in sufficient detail for readers who will be implementing it and those who will be doing protocol analysis -Mixture of informal prose and pseudo-code 5
5 RFC: “Request for Comments” Network protocols are usually disseminated in the form of an RFC TLS version 1.0 is described in RFC 2246 Intended to be a self-contained definition of the protocol ─ Describes the protocol in sufficient detail for readers who will be implementing it and those who will be doing protocol analysis ─ Mixture of informal prose and pseudo-code