
Public-Key Infrastructure Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
Public-Key Infrastructure Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University

Public Key Infrastructure In public key cryptography,we have assumed that everyone knows everyone else's public key.However,this is not easy to achieve. -How does Alice know that the public key she received is really Bob's public key? A public key infrastructure (PKD)consists of all necessary components to securely distribute public keys. Basic idea:use certificate to distribute public keys.We need -Entities for creating certificates -Methods for evaluating certificates -Methods for revoking certificates CSE825 2
2 Public Key Infrastructure In public key cryptography, we have assumed that everyone knows everyone else’s public key. However, this is not easy to achieve. ─ How does Alice know that the public key she received is really Bob’s public key? A public key infrastructure (PKI) consists of all necessary components to securely distribute public keys. Basic idea: use certificate to distribute public keys. We need ─ Entities for creating certificates ─ Methods for evaluating certificates ─ Methods for revoking certificates CSE825

Distribution of Public Keys Original paper on public-key cryptography proposed the use of a Public File:Public-key white pages Public-key certificate -Signed statement specifying the key and identity ·“Bob”,PKB,Sigauthority(MD(Bob”,PKB) Basic idea:Authenticity of many public keys is reduced to the authenticity of one key (the public key of the authority). Who is the authority that you trust? 3
3 Distribution of Public Keys Original paper on public-key cryptography proposed the use of a Public File: Public-key white pages Public-key certificate ─ Signed statement specifying the key and identity ● “Bob”, PKB, sigauthority( MD(“Bob”, PKB) ) Basic idea: Authenticity of many public keys is reduced to the authenticity of one key (the public key of the authority). Who is the authority that you trust?

PKI Trust Models 1:Monopoly Model The world has only one CA trusted by everyone in the world. -The public key of this CA is embedded in all software and hardware as the PKI trust anchor. Loren Kohnfelder BS MIT thesis in 1978 -Offline CA signs(name key)to bind the two in a certificate -Online directory distributes certificates OSI proposed in X.500 a global directory run by monopoly telecommunication companies -Hierarchical database(or data organization,or both) -Path through the directory/database to keys is defined by a series of Relative Distinguished Names(RDNs) -Collection of RDNs form a Distinguished Name(DN) -Data being looked up is found at the end of the RDN path CSE825 4
4 PKI Trust Models 1: Monopoly Model The world has only one CA trusted by everyone in the world. ─ The public key of this CA is embedded in all software and hardware as the PKI trust anchor. Loren Kohnfelder BS MIT thesis in 1978 ─ Offline CA signs (name + key) to bind the two in a certificate ─ Online directory distributes certificates OSI proposed in X.500 a global directory run by monopoly telecommunication companies ─ Hierarchical database (or data organization, or both) ─ Path through the directory/database to keys is defined by a series of Relative Distinguished Names (RDNs) ─ Collection of RDNs form a Distinguished Name (DN) ─ Data being looked up is found at the end of the RDN path CSE825
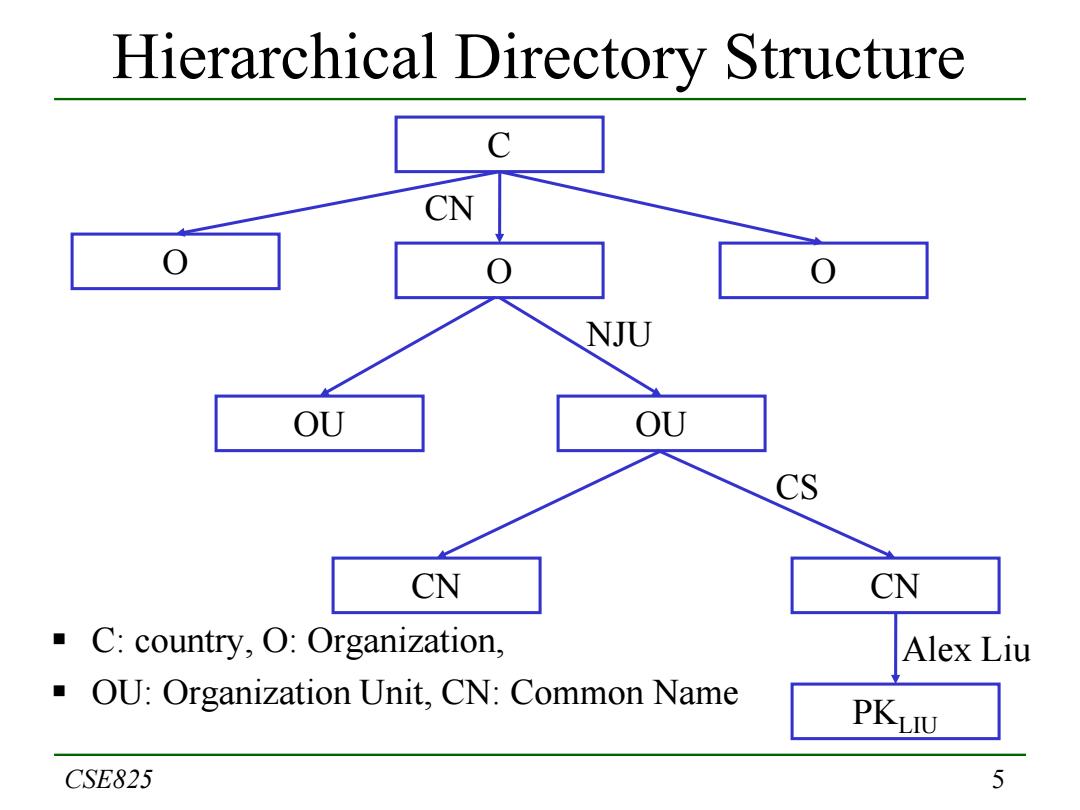
Hierarchical Directory Structure CN NJU OU OU CS CN CN ( C:country,O:Organization, Alex Liu OU:Organization Unit,CN:Common Name PKLIU CSE825 5
5 Hierarchical Directory Structure C: country, O: Organization, OU: Organization Unit, CN: Common Name CSE825 C O O O OU CN OU CN CN NJU CS PKLIU Alex Liu