
Authentication Using Symmetric Keys Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
Authentication Using Symmetric Keys Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
Authentication Using Symmetric Keys Assumption -Without Trusted Third Party:each pair of parties share a secret key K -With Trusted Third Party:each party shares a secret key K with the 3rd party Threat model: -Message injection Inject a new message into a channel -Message modification Modify a message in a channel Message loss Delete a message in a channel -Message replay ●Replay an old message 2
2 Authentication Using Symmetric Keys Assumption ─ Without Trusted Third Party: each pair of parties share a secret key K ─ With Trusted Third Party: each party shares a secret key K with the 3rd party Threat model: ─ Message injection ● Inject a new message into a channel ─ Message modification ● Modify a message in a channel ─ Message loss ● Delete a message in a channel ─ Message replay ● Replay an old message

Without Trusted Third Party-Version 1 Alice Bob A,n,(nKAB Question:What is wrong with this authentication protocol? -Answer:vulnerable to replay attack. -How to fix this problem? 3
3 Without Trusted Third Party – Version 1 Question: What is wrong with this authentication protocol? ─ Answer: vulnerable to replay attack. ─ How to fix this problem? Alice Bob A, n, {n}KAB
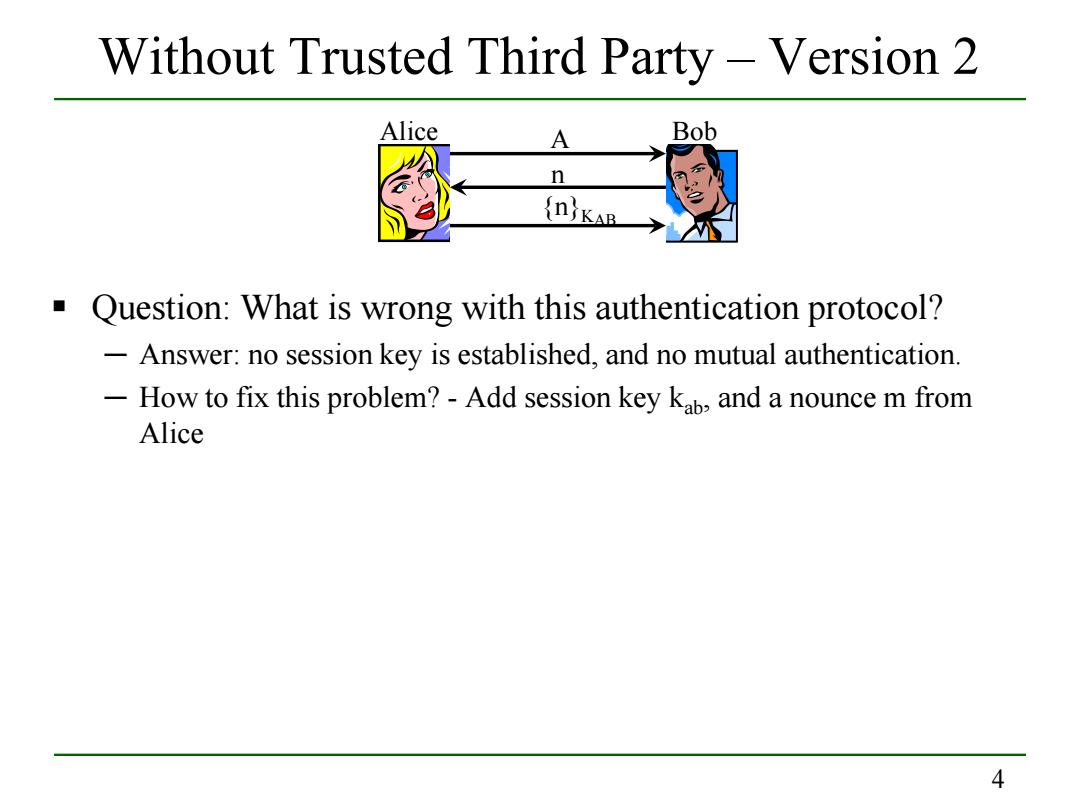
Without Trusted Third Party-Version 2 Alice A Bob n (n KAB Question:What is wrong with this authentication protocol? -Answer:no session key is established,and no mutual authentication. -How to fix this problem?-Add session key kab and a nounce m from Alice 4
4 Without Trusted Third Party – Version 2 Question: What is wrong with this authentication protocol? ─ Answer: no session key is established, and no mutual authentication. ─ How to fix this problem? - Add session key kab, and a nounce m from Alice Alice A Bob n {n}KAB

Without Trusted Third Party-Final Version Alice A Bob n (n,Kab)KaB:m m kab Key management problems in authentication protocols without trusted third party: -1.Every pair of users need to have a shared secret key-too many keys. -2.Hard to manage:when a user joins a group,every one in the group needs to configure a new key with this person. -Solution:use a trusted third party-reduce n2 keys to n keys. 5
5 Without Trusted Third Party – Final Version Key management problems in authentication protocols without trusted third party: ─ 1. Every pair of users need to have a shared secret key – too many keys. ─ 2. Hard to manage: when a user joins a group, every one in the group needs to configure a new key with this person. ─ Solution: use a trusted third party – reduce n2 keys to n keys. Alice A Bob n {n, kab}KAB, m {m} kab