Problem As a result,firewall rules are hard to specify correctly hard to understand correctly hard to change correctly ■ Consequently,firewall configuration errors are common -Most firewalls are poorly designed with errors [Wool04] Firewall errors are unacceptable -Accept malicious packets:lose security -Discard legitimate packets:disrupt business Problem:How to design firewalls? 6
6 Problem As a result, firewall rules are hard to specify correctly hard to understand correctly hard to change correctly Consequently, firewall configuration errors are common ─ Most firewalls are poorly designed with errors [Wool'04] Firewall errors are unacceptable ─ Accept malicious packets: lose security ─ Discard legitimate packets: disrupt business Problem: How to design firewalls?
State-of-the-art Industry:tweak and pray “God bless my rules" Academia:analyze rules -Such as conflict detection ([HSP 00][EM 01][BV 02]) anomaly detection ([AH 03][AH 041) 7
7 State-of-the-art Industry: tweak and pray Academia: analyze rules ─ Such as conflict detection ([HSP 00] [EM 01] [BV 02]) anomaly detection ([AH 03] [AH 04]) “God bless my rules

Structured Firewall Design:Motivation The convention of designing a firewall directly as a sequence of conflicting rules has been taken for granted We point out that this convention is BAD. Why:this convention has three major issues -Consistency issue Completeness issue -Compactness issue 8
8 Structured Firewall Design: Motivation The convention of designing a firewall directly as a sequence of conflicting rules has been taken for granted We point out that this convention is BAD. Why: this convention has three major issues ─ Consistency issue ─ Completeness issue ─ Compactness issue
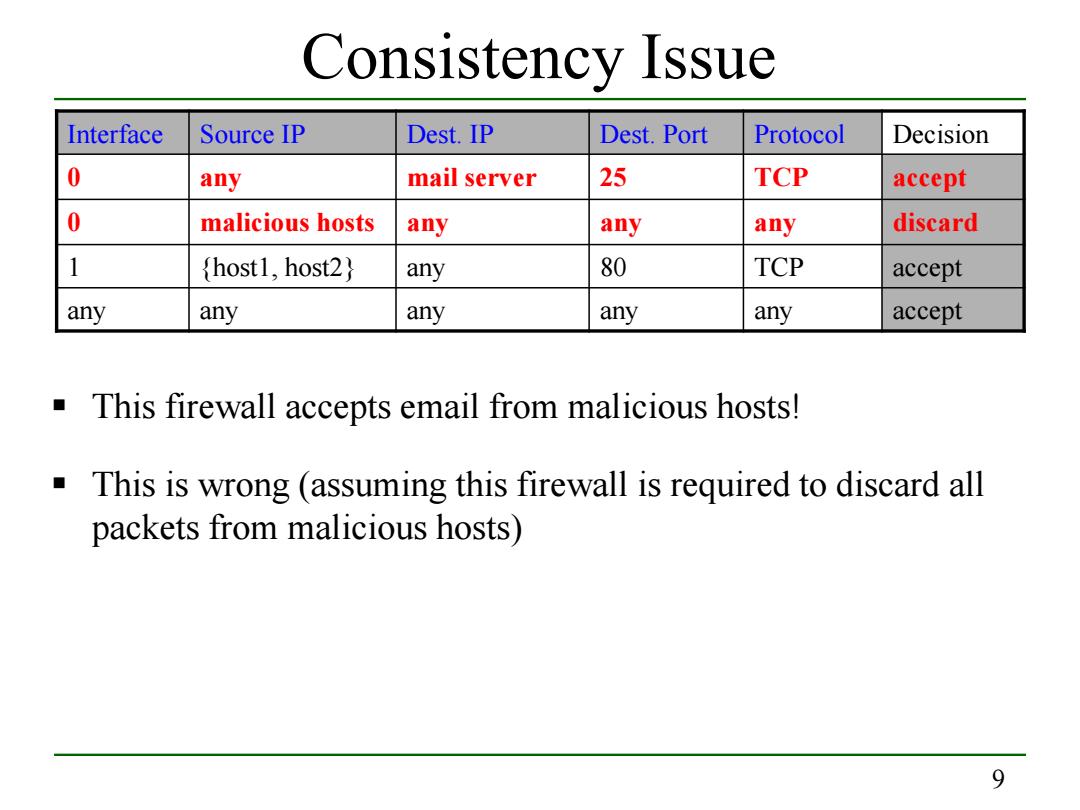
Consistency Issue Interface Source IP Dest.IP Dest.Port Protocol Decision 0 any mail server 25 TCP accept 0 malicious hosts any any any discard host1,host2) any 80 TCP accept any any any any any accept This firewall accepts email from malicious hosts! This is wrong(assuming this firewall is required to discard all packets from malicious hosts) 9
9 Consistency Issue This firewall accepts email from malicious hosts! This is wrong (assuming this firewall is required to discard all packets from malicious hosts) Interface Source IP Dest. IP Dest. Port Protocol Decision 0 any mail server 25 TCP accept 0 malicious hosts any any any discard 1 {host1, host2} any 80 TCP accept any any any any any accept

Consistency Issue Interface Source IP Dest.IP Dest.Port Protocol Decision 0 any mail server 25 TCP accept 0 malicious hosts any any any discard host1,host2) any 80 TCP accept any any any any any accept This firewall accepts email from malicious hosts! This is wrong (assuming this firewall is required to discard all packets from malicious hosts) We should swap the first two rules Consistency issue:hard to ensure rules are ordered correctly 10
10 Consistency Issue This firewall accepts email from malicious hosts! This is wrong (assuming this firewall is required to discard all packets from malicious hosts) We should swap the first two rules Consistency issue: hard to ensure rules are ordered correctly Interface Source IP Dest. IP Dest. Port Protocol Decision 0 any mail server 25 TCP accept 0 malicious hosts any any any discard 1 {host1, host2} any 80 TCP accept any any any any any accept