
Straightforward Solution 1 Solution 1:Each client handles authentication authorization by itself using its database. Drawbacks: -All user databases need to be synchronized across all client PCs. Management tasks like adding or deleting a user need to be performed on every client PC.Obviously this solution is not scalable with the number of client PCs. 6
6 Straightforward Solution 1 Solution 1: Each client handles authentication & authorization by itself using its database. Drawbacks: ─ All user databases need to be synchronized across all client PCs. Management tasks like adding or deleting a user need to be performed on every client PC. Obviously this solution is not scalable with the number of client PCs

Straightforward Solution 2 Solution 2:Each server handles authentication authorization by itself using its database. Drawbacks: -All user databases need to be synchronized across all servers. Management tasks like adding or deleting a user need to be performed on every server.This solution is not scalable with the number of servers.It is hard to manage user accounts and access rights. 7
7 Straightforward Solution 2 Solution 2: Each server handles authentication & authorization by itself using its database. Drawbacks: ─ All user databases need to be synchronized across all servers. Management tasks like adding or deleting a user need to be performed on every server. This solution is not scalable with the number of servers. It is hard to manage user accounts and access rights

Kerberos Key management: -Every server does have a shared key with AS -Every user has a password with AS -Every client does NOT have a shared key with AS Clients mean the client PCs.Users mean human users. ●Why? We want the clients to be"dummies".This not only makes the management of clients easier but also makes the system secure against client compromises 8
8 Kerberos Key management: ─ Every server does have a shared key with AS ─ Every user has a password with AS ─ Every client does NOT have a shared key with AS ● Clients mean the client PCs. Users mean human users. ● Why? – We want the clients to be “dummies”. This not only makes the management of clients easier but also makes the system secure against client compromises
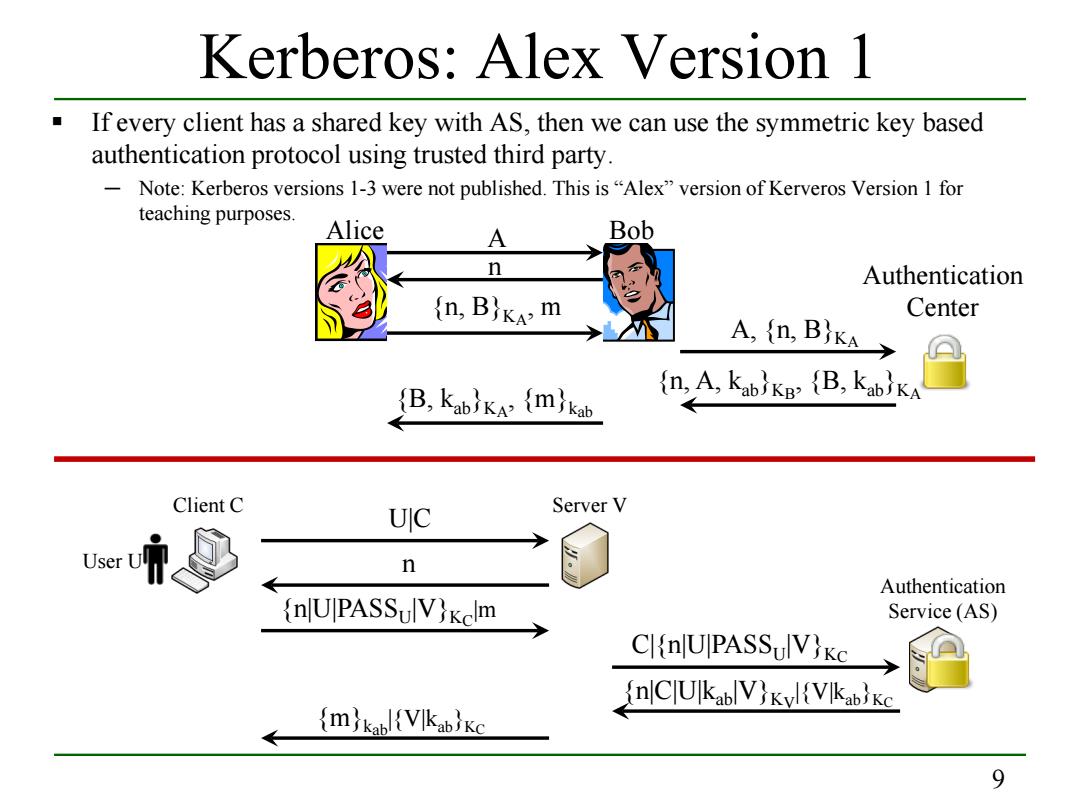
Kerberos:Alex Version 1 If every client has a shared key with AS,then we can use the symmetric key based authentication protocol using trusted third party. Note:Kerberos versions 1-3 were not published.This is"Alex"version of Kerveros Version 1 for teaching purposes. Alice A Bob n Authentication (n,B)KA:m Center A,{,BKA→ (B,KabKa (mkab (n,A,kablkB (B,kabika Client C UIC Server V User n Authentication (nJUPASSulV}Kclm Service(AS) ClinlUIPASSulV)Kc nlClUlkablV}Kyl(Vlkabke (m)kabl{VIkabKc 9
9 Kerberos: Alex Version 1 If every client has a shared key with AS, then we can use the symmetric key based authentication protocol using trusted third party. ─ Note: Kerberos versions 1-3 were not published. This is “Alex” version of Kerveros Version 1 for teaching purposes. Client C Server V User U Authentication {n|U|PASSU|V}K Service (AS) C|m U|C n C|{n|U|PASSU|V}KC {n|C|U|kab|V}KV|{V|kab}KC {m}kab|{V|kab}KC Alice A Bob n {n, B}KA, m A, {n, B}KA {n, A, kab}KB, {B, kab}KA Authentication Center {B, kab}KA, {m}kab

Kerberos:Alex Version 2 Authentication Client C User U UPASSulV Sever(AS) Server V (UlAddressclV)Kv Ul{UlAddressclV}ky ticket Why does the ticket include Addressc? -Otherwise another malicious client can steal a ticket and replay it. -Yes,an attacker can still replay it by changing the address of a compromised client,but he has to wait client C to power off. Why encrypted with Ky? -Prevent ticket from being forgeable. Defect of this protocol: -Password of U is sent in plaintext. -How to encrypt user U's password? Since both Client C and AS knows U's password,they can generate a key from MD(PASSu). 10
10 Kerberos: Alex Version 2 Why does the ticket include AddressC? ─ Otherwise another malicious client can steal a ticket and replay it. ─ Yes, an attacker can still replay it by changing the address of a compromised client, but he has to wait client C to power off. Why encrypted with KV? ─ Prevent ticket from being forgeable. Defect of this protocol: ─ Password of U is sent in plaintext. ─ How to encrypt user U’s password? ● Since both Client C and AS knows U’s password, they can generate a key from MD(PASSU). Server V Client C User U Authentication U|PASS Sever (AS) U|V {U|AddressC|V}KV U|{U|AddressC|V}KV ticket