Problems of the Monopoly Model There is no such a universally trusted organization. Infeasible to change that CA's public key,if it is compromised. -All software and hardware are preconfigured with the CA's public key Difficult to certify. -How does the CA can certify your identity?Just because you paid? Single point of failure. -What if that CA has a corrupt employee? The world CA will charge monopoly price for certification. Concerns about the use of world directory -Companies don't like making their internal structure public Directory for corporate headhunters -Privacy concerns Directory of single women Directory of teenage children CSE825 6
6 Problems of the Monopoly Model There is no such a universally trusted organization. Infeasible to change that CA’s public key, if it is compromised. ─ All software and hardware are preconfigured with the CA’s public key Difficult to certify. ─ How does the CA can certify your identity? Just because you paid? Single point of failure. ─ What if that CA has a corrupt employee? The world CA will charge monopoly price for certification. Concerns about the use of world directory ─ Companies don’t like making their internal structure public ● Directory for corporate headhunters ─ Privacy concerns ● Directory of single women ● Directory of teenage children CSE825

PKI Trust Model 2:Monopoly Registration Authorities (RAs) Same as the monopoly model except that the world CA uses some other organizations to certify identities of users. ■( Getting certified becomes easier. All other drawbacks of the monopoly model still applies. CSE825 7
7 PKI Trust Model 2: Monopoly + Registration Authorities (RAs) Same as the monopoly model except that the world CA uses some other organizations to certify identities of users. Getting certified becomes easier. All other drawbacks of the monopoly model still applies. CSE825
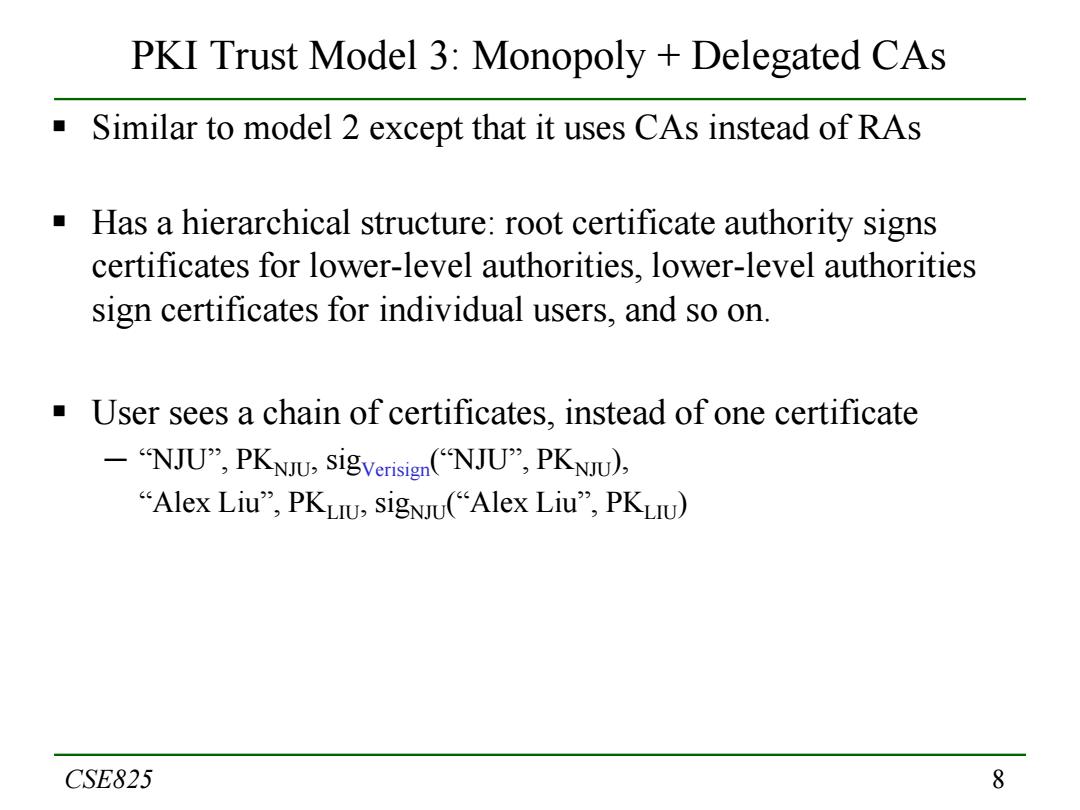
PKI Trust Model 3:Monopoly Delegated CAs Similar to model 2 except that it uses CAs instead of RAs Has a hierarchical structure:root certificate authority signs certificates for lower-level authorities,lower-level authorities sign certificates for individual users,and so on. User sees a chain of certificates,instead of one certificate -"NJU",PKNIU,sigverisign(NJU,PKNJU), "Alex Liu",PKLIU,sigNU("Alex Liu",PKLIU) CSE825 8
8 PKI Trust Model 3: Monopoly + Delegated CAs Similar to model 2 except that it uses CAs instead of RAs Has a hierarchical structure: root certificate authority signs certificates for lower-level authorities, lower-level authorities sign certificates for individual users, and so on. User sees a chain of certificates, instead of one certificate ─ “NJU”, PKNJU, sigVerisign(“NJU”, PKNJU), “Alex Liu”, PKLIU, sigNJU(“Alex Liu”, PKLIU) CSE825

PKI Trust Model 4:Oligarchy -multiple CAs for the world The world trust multiple CAs.This is the model used today for web browsers. Web browsers today come shipped with the public keys of about 80 CAs. ■Problems: -Any of the trust anchor organizations getting comprised will put the security of the world into risk. The trust anchor organizations are trusted by the vendor,not by the user. -It is easy to trick a naive user to add a bogus trust anchor into the set: Warning:This was signed by an unknown CA.Would you like to accept the certificate anyway?(OK) ● Would you like to always accept this certificate without being asked in the future?(OK) ● Would you like to always accept certificates from the CA that issued the certificate? (OK) .Would you like to always accept certificates from any CA?(OK) ● Since you are willing to trust anyone for anything,would you like me to make random edits to the files on your hard drive without bothering you with a pop-up box?(OK) Use of public machine.What if the previous user added a malicious anchor? CSE825 9
9 PKI Trust Model 4: Oligarchy – multiple CAs for the world The world trust multiple CAs. This is the model used today for web browsers. Web browsers today come shipped with the public keys of about 80 CAs. Problems: ─ Any of the trust anchor organizations getting comprised will put the security of the world into risk. ─ The trust anchor organizations are trusted by the vendor, not by the user. ─ It is easy to trick a naïve user to add a bogus trust anchor into the set: ● Warning: This was signed by an unknown CA. Would you like to accept the certificate anyway? (OK) ● Would you like to always accept this certificate without being asked in the future? (OK) ● Would you like to always accept certificates from the CA that issued the certificate? (OK) ● Would you like to always accept certificates from any CA? (OK) ● Since you are willing to trust anyone for anything, would you like me to make random edits to the files on your hard drive without bothering you with a pop-up box? (OK) ─ Use of public machine. What if the previous user added a malicious anchor? CSE825