
Why SSL?SSL Provides Confidentiality (Privacy) Data integrity (Tamper-proofing) -done as part of digital signing. ■ Server authentication(Proving a server is what it claims it is) Used in typical B2C transactions Optional client authentication -Would be required in B2B(or Web services environment in which program talks to program) Why not B2C:server use passwords to authenticate clients,not certificates.Clients normally do not have certificates. 6
6 Why SSL? SSL Provides ... Confidentiality (Privacy) Data integrity (Tamper-proofing) ─ done as part of digital signing. Server authentication (Proving a server is what it claims it is) Used in typical B2C transactions Optional client authentication ─ Would be required in B2B (or Web services environment in which program talks to program) ─ Why not B2C: server use passwords to authenticate clients, not certificates. Clients normally do not have certificates

TLS Basics TLS consists of two protocols ■Handshake protocol -Use public-key cryptography to establish a shared secret key between the client and the server Record protocol -Use the secret key established in the handshake protocol to protect communication between the client and the server We will focus on the handshake protocol 7
7 TLS Basics TLS consists of two protocols Handshake protocol ─ Use public-key cryptography to establish a shared secret key between the client and the server Record protocol ─ Use the secret key established in the handshake protocol to protect communication between the client and the server We will focus on the handshake protocol

TLS Handshake protocol Two parties:client and server Negotiate version of the protocol and the set of cryptographic algorithms to be used -Interoperability between different implementations of the protocol Authenticate server and client (optional) Use digital certificates to learn each other's public keys and verify each other's identity Use public keys to establish a shared secret 8
8 TLS Handshake Protocol Two parties: client and server Negotiate version of the protocol and the set of cryptographic algorithms to be used ─ Interoperability between different implementations of the protocol Authenticate server and client (optional) ─ Use digital certificates to learn each other’s public keys and verify each other’s identity Use public keys to establish a shared secret
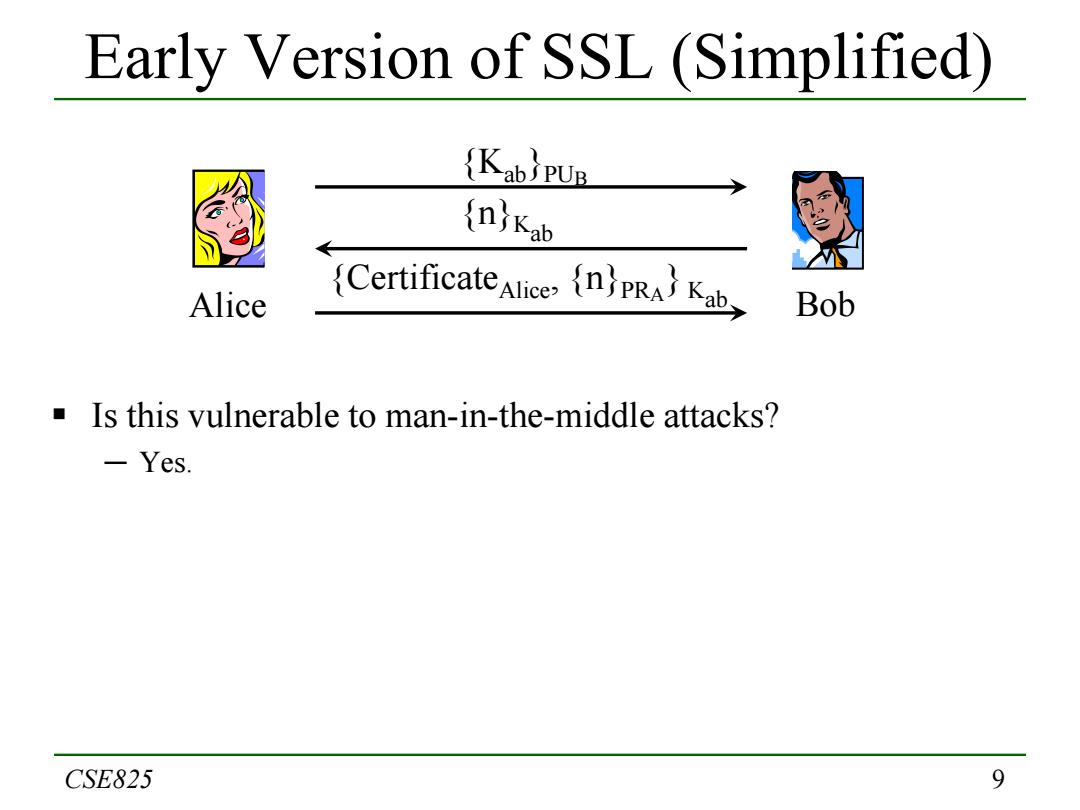
Early Version of SSL (Simplified) (KabpUp njKab Alice CertificateliceKab Bob Is this vulnerable to man-in-the-middle attacks? -Yes. CSE825 9
9 Early Version of SSL (Simplified) Is this vulnerable to man-in-the-middle attacks? ─ Yes. CSE825 Alice Bob {n}Kab {CertificateAlice, {n}PRA} Kab {Kab}PUB