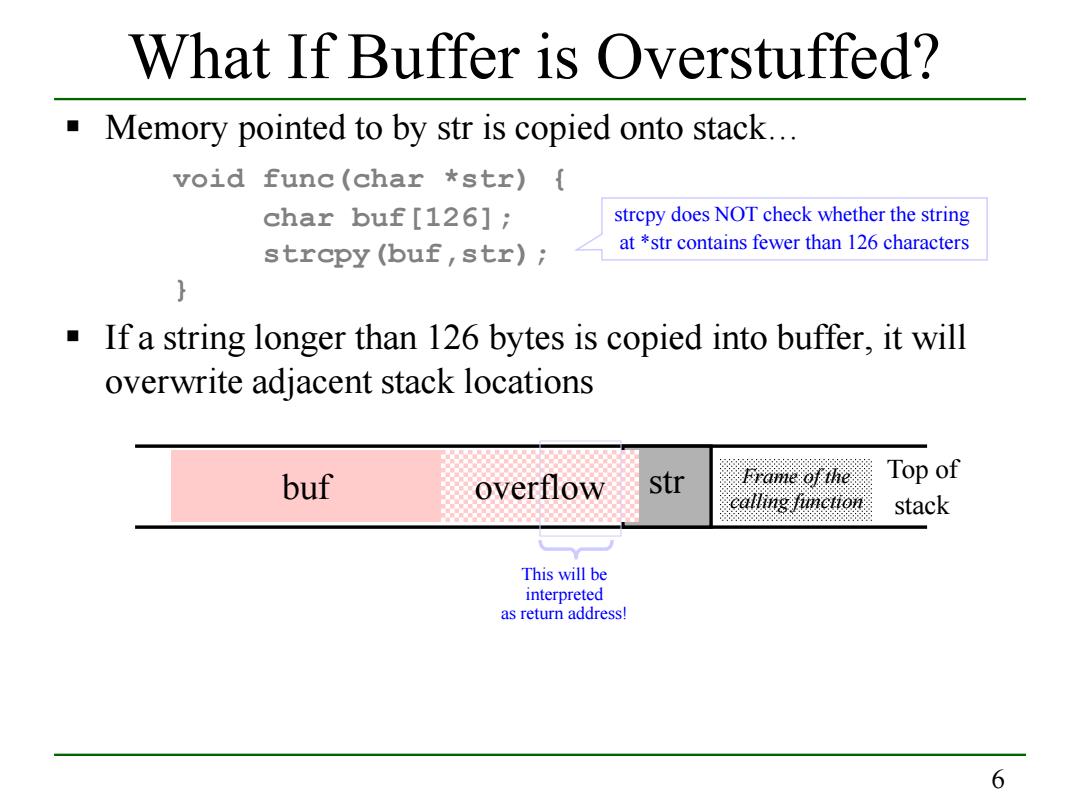
What If Buffer is Overstuffed? Memory pointed to by str is copied onto stack... void func(char *str){ char buf[126]; strcpy does NOT check whether the string strcpy(buf,str); at *str contains fewer than 126 characters a If a string longer than 126 bytes is copied into buffer,it will overwrite adjacent stack locations buf overflow str Frame of the Top of calling function stack This will be interpreted as return address! 6
6 What If Buffer is Overstuffed? Memory pointed to by str is copied onto stack… void func(char *str) { char buf[126]; strcpy(buf,str); } If a string longer than 126 bytes is copied into buffer, it will overwrite adjacent stack locations strcpy does NOT check whether the string at *str contains fewer than 126 characters buf str This will be interpreted as return address! overflow Top of stack Frame of the calling function
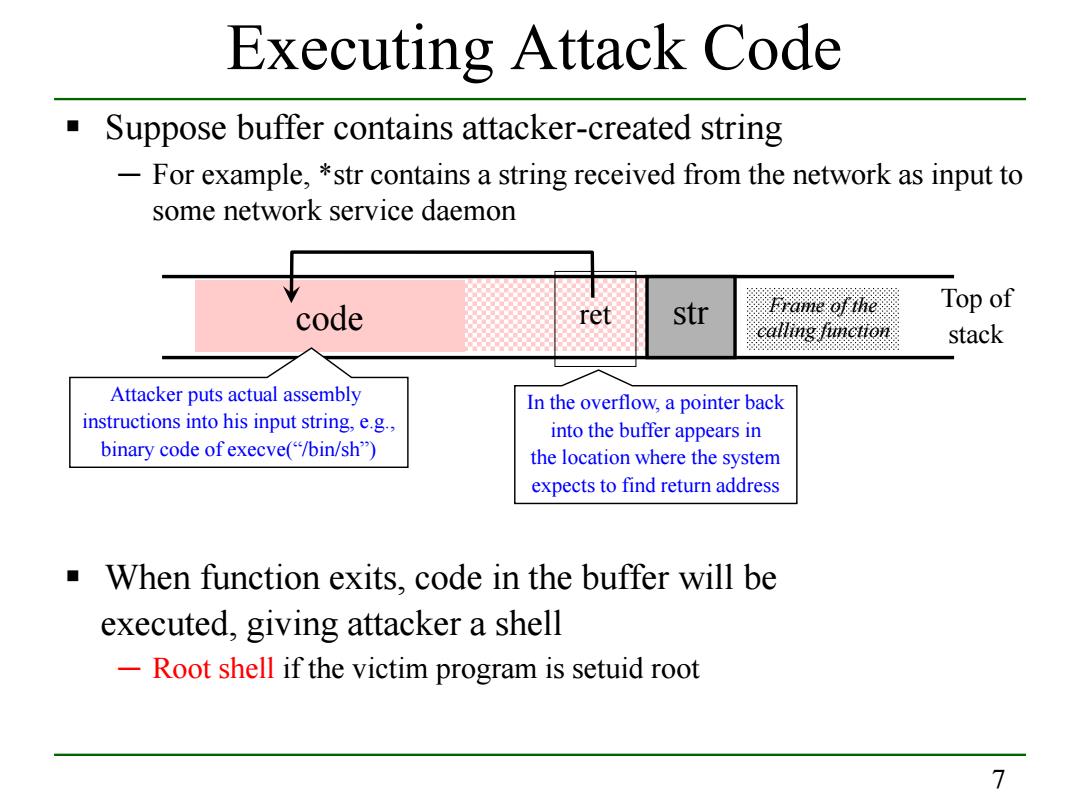
Executing Attack Code Suppose buffer contains attacker-created string For example,*str contains a string received from the network as input to some network service daemon str Frame of thie Top of code et ℃illing functto stack Attacker puts actual assembly In the overflow,a pointer back instructions into his input string,e.g., into the buffer appears in binary code of execve("/bin/sh") the location where the system expects to find return address When function exits,code in the buffer will be executed,giving attacker a shell -Root shell if the victim program is setuid root 7
7 Executing Attack Code Suppose buffer contains attacker-created string ─ For example, *str contains a string received from the network as input to some network service daemon When function exits, code in the buffer will be executed, giving attacker a shell ─ Root shell if the victim program is setuid root code str Frame of the calling function ret Attacker puts actual assembly instructions into his input string, e.g., binary code of execve(“/bin/sh”) In the overflow, a pointer back into the buffer appears in the location where the system expects to find return address Top of stack