
Buffer Overflow:The Essentials Basic Example Soltware Security “123456" Essentials sinclude <string.h> 0 Basic Etimple ant main(int arge,char argv){ Shellcode char buf[64]; Dufincien strepy(buf,argv[1]); argv argc Shali-Spanmning return addr Durp of assenbler code for function main: caller's cbp A Real Word Butter 6x88048304C40):Push Xebp 一%ebp Overflow Attac比 0x88348305(+1):ov esp,的p bul 0x08048307c43):ub 72,050 64ts) 0x8804830ac+6):0V 12(%ebp),%eax Bx883483ed c+9>:nov 4(ea×),xeax 学■n BxE88483fB c+12>:nov eax,4(%0sp】 Bx888483f4<+16>:1ea -64(%ebp).%eax Inleger Overfiow exe88483f7<+193:oy Xeax,(Xesp) Owerve 0xe88483fa《+22):ca110x88483085 trcpyp1t) Aah出E arv[1l 0x88g483ff<+27>:1eae lrtagar Diuifen 0x68048408<+28>:ret Sesp Hesp Overflow m过士aM年 Ahead Ex-年 Naning Ueivarsiy
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? 10 Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials Basic Example “123456

Buffer Overflow:The Essentials Basic Example Soltware Security “123456" Essentials Basic Etimple a1 nclude《str1ng.h> int nain(int argc,char *argv){ Shellcode char buf[64]; Dulincisn strcpy(buf,arv1]》i g En argc Shali-Spanmning return addr Dutp of assenbler code for function nain: A Real Word Butter caller's ebp 0x880483e4<+9>:pUsh Sebp %ebp Overflow Attac比 ex889483e5《+1>: Xesp,Xebp ex888483e7c+3): sub 572,e5p 6x8834830ac+63: 12(¥cbp),ca× 0x8884830d《+93:nav 4(0ax),%0ax 学■n Bx288483fe《+12):av Seax,4(Zesp) Inleger Overfiow 0x888483f4《+16):1ed -64(%ebp),eax 01995821 Owerve 8x883483f7《+19y:nav 03x,(黑05p) Aah出E Bx883483faC+223:ca118x83483B9《5 trspyp1t2 argv 1] 8x880483ffc+273:10aw9 huf ttagar Oiaife ex8834848e《+281et esp Hesp Overflow m过士aM年 Ahead Ex=年 Naning Ueivarsity
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? 11 Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials Basic Example “123456

Buffer Overflow:The Essentials Basic Example Soltware Security Essentials #include《str1ng:h> Basic Etimple int nain(int argc,char *argv) char buf[64]; Shellcode strcpy(buf,argv[1]); argv Dufincien arge return addr Shali-Spamning Dunp of assenbler code for function main: caller's ehp A Real Word Butter 8x880483e4<+8>:pu5h 第ebp 。一%bp buf Overflow Attac比 0自80483e5《+1):oy Xesp,Xebp dx880483e7《+3>:sub $72,Xesp [64 bytes) 时国 3x880483ea(+6>:oy 12(%ebp),Xeax x088483ed<+9):m0y 4(第ea×),%ea× 0x080483f8《+12>:moy ¥ea×,4(%0sp】 学■n 8888483f4(+16>:1ca -64(cbp》,%caX Inleger Overfiow 0888483f7c+19):moy Xeax.(Zesp) Owerve 888483fhc422):cn110x8848308<5 trcpy#p1t2 %v对 Aah出E 0880483ff《+27>:1eave buf 0x88048489<+28>:ret %esp ttagar Oiaife Hesp Overflow m过士aM年 Ahead Ex=年 Naning Ueivarsiy
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? 12 Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials Basic Example
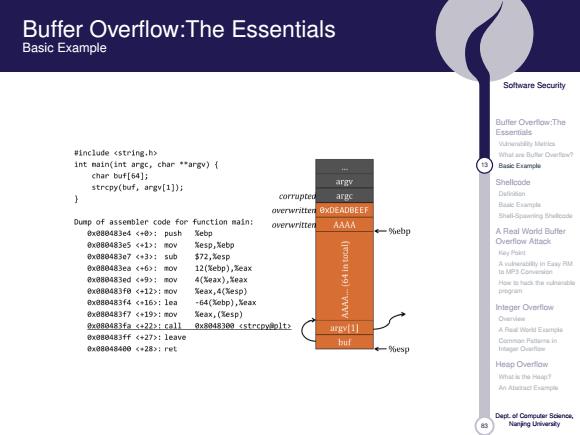
Buffer Overflow:The Essentials Basic Example Soltware Security Essentials #include <string.h> int main(int argc,char *argv){ Basic Etimple char buf[54]; Shellcode strcpy(buf,argv[1]); argv corrupte argc Dulincisn overwritten SxDEADBEEF En Shali-Spamning Dunp of assenbler code for function main: overwritter AAAA 0xe88483e4<+>:push Xebp -%ebp A Real Word Butter 8x080483e5<+1):F0y Xesp,Xebp Overflow Attac比 0088483e7(+3315ub $72,%esp 0g80483ea《+6>:moy 12(餐ebp),ea× 0088483ed449):Woy 4(eax》,eax 0888483f0<+12>:f0y Xeax,4(Xesp) 学■n e088483f4c+16):1c3 -64(Xebp),%eax au888483f7<+19>:ton Inleger Overfiow Xeax,(Sesp) Owerve x983483fa《+222:ra11L9x348303《5trc1t上 urgy 1 Aah出E 888483ff<+27>:1eave bu时 008048480(+28):ret ttagar Oiaife Hesp Overflow m过士aM年 Ahgad Ea-年 Naning Ueivarsity
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? 13 Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials Basic Example
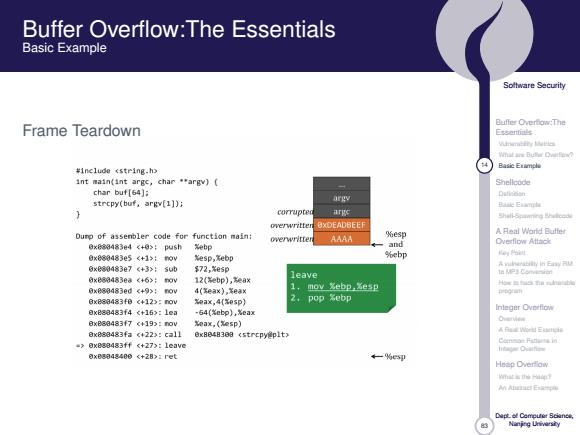
Buffer Overflow:The Essentials Basic Example Soltware Security Frame Teardown Bufler Overflow;The ¥1 nclud0cstr1ng-h> 4 Basic Etimple int main(int argc,char **argv) Shellcode char but[54】: argv Dulineisn strcpy(buf,argv[1])i corrupte arge Shali-Spamning overwritten BKDEADBEEF Durp of assenbler code for function main: A Real Word Butter overwritten AAAA %esp Overflow Attac比 0x89483e4<+0>:pu5h Xebp and 0x089483e5<+1>:0y Xesp,ebp %ebp 0×888483e7<+3>:5u电 72,e5p a位匀snm 0×889483ea<+6>:ov 12(ebp),ea× leave og每fa nhatib 0x889483ed<+9>:F0y 4(ea×),eax 1.mov Xebp,Zesp 学■n 6x883483fec+123:ov 0ax,4(0sp) 2.pop sebp 0xe83483f4《+16>:1e3 -64(%ebp),%eax Inleger Overfiow 8xe80483f7c+193:ov Owerve 0ax,(esp)】 Aah出E 8x883483fa《422:ca11 ex8848303 <strepyplt> =>0xe88483ff《+273:1eave 已nsm开sn lrtagar Diuifen 0xB8848480<+2B>:ret ←一%c Hesp Overflow m过士aM年 Ahead Ex-年 Naning Ueivarsiy
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? 14 Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials Basic Example Frame Teardown