
Buffer Overflow:The Essentials Vulnerability Metrics Soltware Security Buffer Overfow;The Essentials Vunarbliy Matres Banc Elurnphe Exploits vs.Buffer Overflows Shellcode Dufincien Given the amount of vulnerabilities associated with buffer overflows,we felt it necessary to have a look at the principle of Shali-Spanmning A Real Word Butter buffer overflow.As you have probably come to realize already, Overflow Attac比 buffer overflows are a specific type of vulnerability and the process of leveraging or utilizing that vulnerability to penetrate a vulnerable system is referred to as exploiting a system. 字■n Inleger Overfiow Owerve AA:dM出E ttagar Oiaife Hesp Overflow m过士aM年 Ahgad Ex-年 Naning Ueivarsity
83 Software Security Buffer Overflow:The Essentials 6 Vulnerability Metrics What are Buffer Overflow? Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials Vulnerability Metrics Exploits vs. Buffer Overflows Given the amount of vulnerabilities associated with buffer overflows, we felt it necessary to have a look at the principle of buffer overflow. As you have probably come to realize already, buffer overflows are a specific type of vulnerability and the process of leveraging or utilizing that vulnerability to penetrate a vulnerable system is referred to as exploiting a system

Buffer Overflow:The Essentials What are Buffer Overflow? Soltware Security In computer security and programming,a buffer overflow,or Bufler Overfow:The buffer overrun,is an anomaly where a program,while writing data to a buffer,overruns the buffer's boundary and overwrites Wihat are Butur Ovetow? adjacent memory locations.This is a special case of the Banc Eluntha Shellcode violation of memory safety. Dulineisn C/C++does not check that the writes are in-bound Shali-Spamning A Real Word Butter Recently,Intel offered a new set of instructions (MPX)that Overflow Attac比 allow fast-bounds check of memory writes. 时内国 og每shmt 学■n Inleger Overfiow Owerve Ad出E Hesp Overflow mt士sM年到 Angad Ex-年 Naning Ueivarsiy
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics 7 What are Buffer Overflow? Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials What are Buffer Overflow? In computer security and programming, a buffer overflow, or buffer overrun, is an anomaly where a program, while writing data to a buffer, overruns the buffer’s boundary and overwrites adjacent memory locations. This is a special case of the violation of memory safety. I C/C++ does not check that the writes are in-bound I Recently, Intel offered a new set of instructions (MPX) that allow fast-bounds check of memory writes. Stack-based I Heavily covered in this class Heap-based I More advanced I Very dependent on system and library version

Buffer Overflow:The Essentials What are Buffer Overflow? Soltware Security In computer security and programming,a buffer overflow,or Bufler Overfow:The buffer overrun,is an anomaly where a program,while writing data to a buffer,overruns the buffer's boundary and overwrites What are Buter Oveetiow? adjacent memory locations.This is a special case of the Banc Eluntha Shellcode violation of memory safety. Dufincien C/C++does not check that the writes are in-bound Shali-Spamning A Real Word Butter Recently,Intel offered a new set of instructions (MPX)that Overflow Attac比 allow fast-bounds check of memory writes. 时内国 Stack-based o每shm山ht 学■n Heavily covered in this class Inleger Overfiow Owerve Heap-based AAd出E More advanced Hesp Overflow Very dependent on system and library version m过士aM年 Angad Ex=年 Naning Ueivarsiy
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics 7 What are Buffer Overflow? Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials What are Buffer Overflow? In computer security and programming, a buffer overflow, or buffer overrun, is an anomaly where a program, while writing data to a buffer, overruns the buffer’s boundary and overwrites adjacent memory locations. This is a special case of the violation of memory safety. I C/C++ does not check that the writes are in-bound I Recently, Intel offered a new set of instructions (MPX) that allow fast-bounds check of memory writes. Stack-based I Heavily covered in this class Heap-based I More advanced I Very dependent on system and library version

Buffer Overflow:The Essentials Basic Example Soltware Security Basic Example Essentials 8 Basic Etimple ainclude <string.h> int main(int argc,char argv)( Shellcode char buf[64]; Dulincisn strcpy(buf,argv[1]); y arge Shali-Spamning retum addr A Real Word Butter callers ebp Overflow Attac比 。一%ebp buf (64bt) a位匀snm 学■n Inleger Overfiow Overveu Aah出E argv 1] 巴nmon Fanimta litagar Diaifes buf esp Hesp Overflow m过士aM年 Ahead Ex=年 Nanjng Uivarsiy
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? 8 Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials Basic Example Basic Example
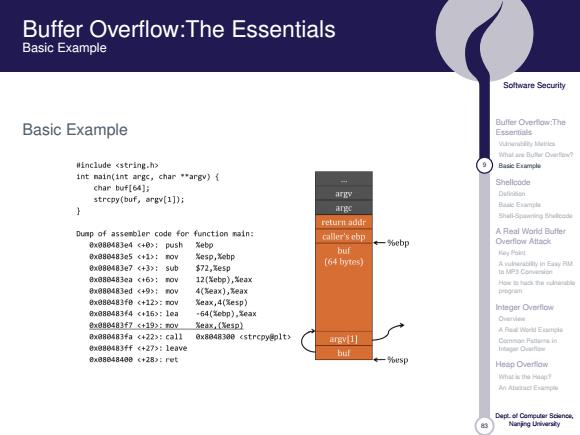
Buffer Overflow:The Essentials Basic Example Soltware Security Basic Example Essentials Winclude <string.h> Basic Etimple int nain(int argc,char *"argv){ Shellcode char buf[64]; Dulincisn strcpy(buf,srgv(1]); w型 g Shali-Spamning returi adur Dunp of asserblor code for function nain: caller's ebp A Real Word Butter 8x080483e4<+0>;push Xebp 一%0bp Overflow Attac比 buf 0a88483e5《+1):oy Xesp,ebp (64 bytes) 0080483e7<+3>:5ub 72,e5p a位匀snm 8B08e483e1(t6):roy 12(%ebp),%eax 8x880483ed<+9>:r0v 4(ea×),ea× 学■n ex888483fe<+12):rov %eax,4(e5p】 Inleger Overfiow 8x088483f4c+153:1ea 64(¥cbp).¥03 @x088483f7 <+19>:rov Xeax,(Xesp) Owerve Aah出E 8x380483fa <+22>:call 0x8048300 <strcpyeplt> argv 1] 8u880483ff<+27>:1eave bul lrtagar Diuifen e08848408《+28):ret 。一%tsp Hesp Overflow m过士aM年 Ahead Ex=年 Naning Ueivarsiy
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? 9 Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials Basic Example Basic Example