
Software Security Overview Mao Bing Department of Computer Science NanJing University
Software Security Overview Mao Bing Department of Computer Science NanJing University
Outline ·Background 。 Software Security:Control-flow Hijack Attack Memory Layout,Stack frame,Procedure >Buffer Overflow:Vulnerability,Defenses RILC,Return-Oriented Programming ASLR CFI Software Security:Non-control Data Attack Data Oriented Programming ·Summary 2
2 Outline • Background • Software Security: Control-flow Hijack Attack ➢ Memory Layout , Stack frame, & Procedure ➢ Buffer Overflow: Vulnerability, & Defenses ➢ RILC, Return-Oriented Programming ➢ ASLR & CFI • Software Security: Non-control Data Attack ➢ Data Oriented Programming • Summary

Outline ·Background Software Security:Control-flow Hijack Attack Memory Layout,Stack frame,Procedure Buffer Overflow:Vulnerability,Defenses RILC,Return-Oriented Programming ASLR CFI Software Security:Non-control Data Attack Data Oriented Programming Summary 3
3 Outline • Background • Software Security: Control-flow Hijack Attack ➢ Memory Layout , Stack frame, & Procedure ➢ Buffer Overflow: Vulnerability, & Defenses ➢ RILC, Return-Oriented Programming ➢ ASLR & CFI • Software Security: Non-control Data Attack ➢ Data Oriented Programming • Summary
Computer Security Computer security,also known as cybersecurity or IT security,is the "...protection of information systems from theft(secrecy/confidentiality) or damage (integrity)to the 取7Y hardware,the software,and This picture is from http: to the information on them,..." //securitygem.com/home-security-reviews -Gasser,Morrie(1988)
4 Computer Security Computer security, also known as cybersecurity or IT security, is the “...protection of information systemsfrom theft(secrecy/confidentiality) or damage (integrity) to the hardware, the software, and to the information on them, ...” —Gasser, Morrie (1988)
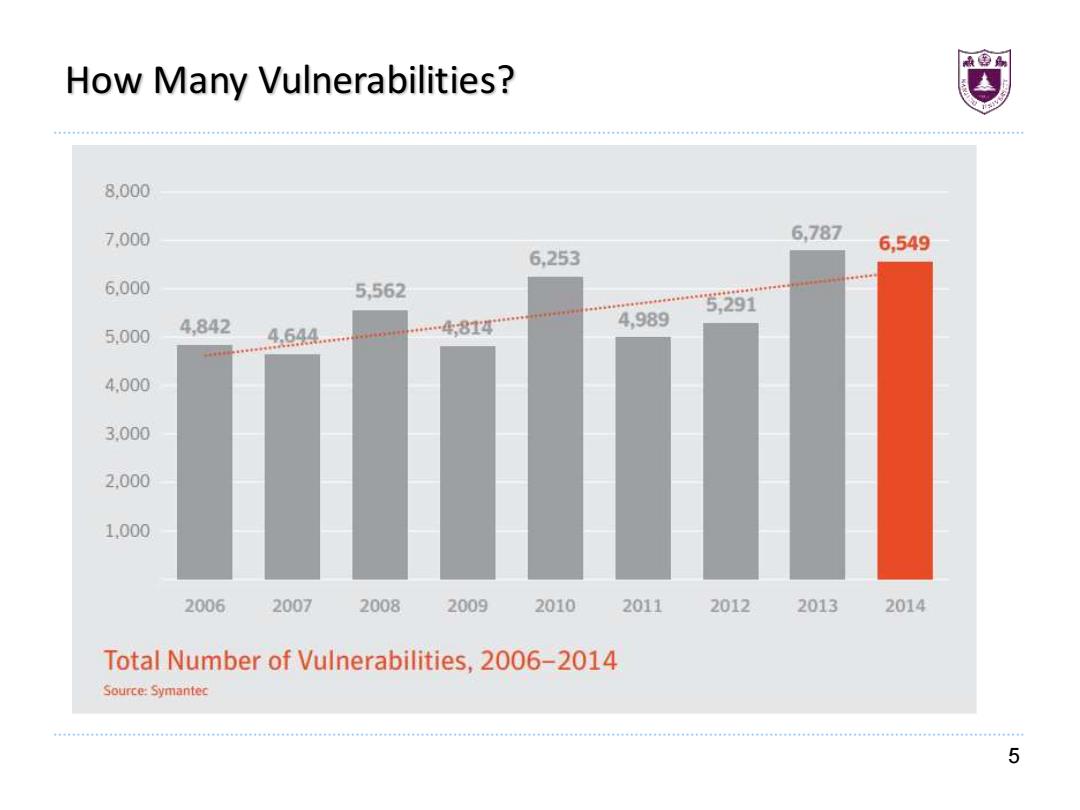
How Many Vulnerabilities? 8,000 7,000 6,787 6,549 6,253 6.000 5,562 5,291 4.989 5.000 4,842 4.644. 4814 4.000 3.000 2.000 1.000 2006 2007 2008 2009 2010 2011 2012 2013 2014 Total Number of Vulnerabilities,2006-2014 Source:Symantec 5
5 How Many Vulnerabilities?