
2017Fall:Software Security Lecture 5:Practical Control Flow Hijack Defense: StackGuard,DEP,and ASLR Bing Mao maobingon ju.edu.cn Department of Computer Science
2017Fall:Software Security Lecture 5 : Practical Control Flow Hijack Defense: StackGuard, DEP, and ASLR Bing Mao ♠❛♦❜✐♥❣❅♥❥✉✳❡❞✉✳❝♥ Department of Computer Science

Outline Soltware Security Background Control Flow Hijack Background Carerf Fies Hpck Control Flow Hijack Defense CaciaFas Hick Delinie Canary Defense Cattary Codenas B:s0a时 StackGuard 9S0ia过ana StackGuard Weakness DnG 4na中eCanin DiffGuard Data Execution Polymorphic Canary Prevention Dutidan Data Execution Prevention Fghim-ta-soc Arad Definition ASLR DEP Scorecard A9月 Return-to-libc Attack ASLR ASLR Randomization ASLR Nanjng Uivarsity
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Outline Background Control Flow Hijack Control Flow Hijack Defense Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR
Background Control Flow Hijack Soltware Security Background Contol Flow Hijack Occurs when an attacker gains control of Carnial Fis Hyck Delinie Cattary Codenas the instruction pointer s0au时 SOianT weianat DnG A few common hijack methods Puymnishie Cinin buffer overflows Data Execution Prevention heap overflow Dutidan format string attacks ASLR ASLR Credit:a portion of the slides in this lecture are compiled from Dr.David Brumley and also from book CSAPP Nanjng Uivarsty
57 Software Security Background 3 Control Flow Hijack Control Flow Hijack Defense Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Background Control Flow Hijack
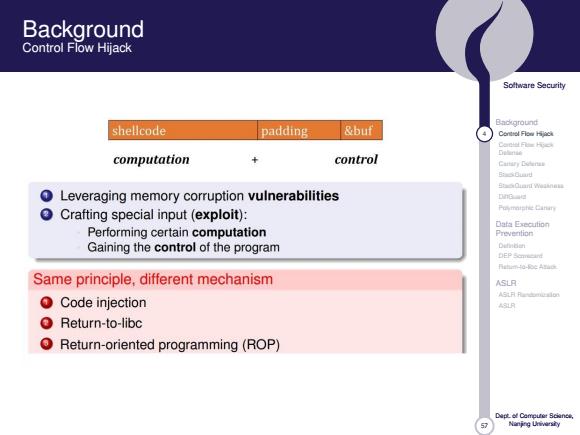
Background Control Flow Hijack Soltware Security Background shellcode padding &buf Contol Flow Hijack Carnial Fis Hyck control Delinie computation Cattary Codenas Bs0au时 SOianT weaneu 0 Leveraging memory corruption vulnerabilities DnG Crafting special input(exploit): Puymnishie Cinin Data Execution Performing certain computation Prevention Gaining the control of the program Dh6的 Same principle,different mechanism ASLR Code injection ASLR Return-to-libc OReturn-oriented programming(ROP) Nanjng Urivarsiy
57 Software Security Background 4 Control Flow Hijack Control Flow Hijack Defense Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Background Control Flow Hijack

Background Control Flow Hijack Defense Soltware Security Background 5】 Cordol月ea Detinse Vulnerabilities(bugs)are the root cause of hijacks Cattary Codenas Bs0au时 Identify vulnerabilities with analysis tools(before attackers) SOianT weianei DnG Prove program correctness Puymnishie Cinin Data Execution Prevention Mitigation Techniques: Dutidan Canaries-StackGuard Data Execution Prevention(DEP)/No eXecute(NX) ASLR Address Space Layout Randomization(ASLR) ASLR Nanjng Uivarsty
57 Software Security Background Control Flow Hijack 5 Control Flow Hijack Defense Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Background Control Flow Hijack Defense