
2017Fall:Software Security Lecture 3:Buffer Overflow Attack Bing Mao maobingOnju.edu.cn Department of Computer Science
2017Fall:Software Security Lecture 3 : Buffer Overflow Attack Bing Mao maobing@nju.edu.cn Department of Computer Science

Outline Buffer Overflow:The Essentials Soltware Security Vulnerability Metrics What are Buffer Overflow? Bufler Overflow;The Essentials Basic Example Shellcode 五4eE Definition Shellcode Basic Example Dafieien Shell-Spawning Shellcode Shali-Spamning A Real World Buffer Overflow Attack A Real Word Butter Overflow Attac比 Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program 学■n Integer Overflow Inleger Overfiow Owerve Overview AAd出E A Real World Example lrtagar Diuifen Common Patterns in Integer Overflow Hesp Overflow mt士sM年到 Heap Overflow Ahgad Ex=年 What is the Heap? An Abstract Example Naning Ueivarsiy
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Outline Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example
Illustrate Soltware Security Bufler Overflow;The Essentials 五4eE Shellcode Credit:a portion of the slides in this lecture are compiled from Shali-Spamning Dr.David Brumley and also from book CSAPP. A Real Waric时Buie Overflow Attac比 学■n Inleger Overfiow Overveu AdM出En litagar Diaife Hesp Overflaw m过士aM年 M Ahgad Ea=年 Nanjng Uivarsiy
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Illustrate Credit:a portion of the slides in this lecture are compiled from Dr.David Brumley and also from book CSAPP
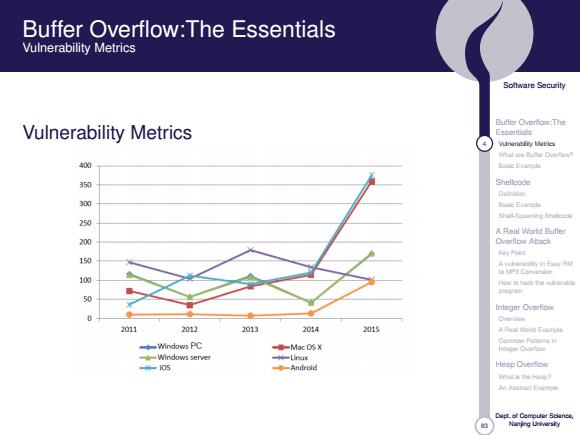
Buffer Overflow:The Essentials Vulnerability Metrics Soltware Security Vulnerability Metrics Essentials Mungrublzy Matrica 400 Banc Elurnphe 350 Shellcode Dufincien 250 Shali-Spamning A Real Word Butter 200 Overflow Attac比 150 学■n 50 Inleger Overfiow Overvie 2011 2012 2013 2014 2015 Aah出E -◆-Windows PC Mac 0S X Windows server ◆-Android Hesp Overflow mt士sM年到 M Ahgtad Exapi Nanjng Uivarsiy
83 Software Security Buffer Overflow:The Essentials 4 Vulnerability Metrics What are Buffer Overflow? Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials Vulnerability Metrics Vulnerability Metrics
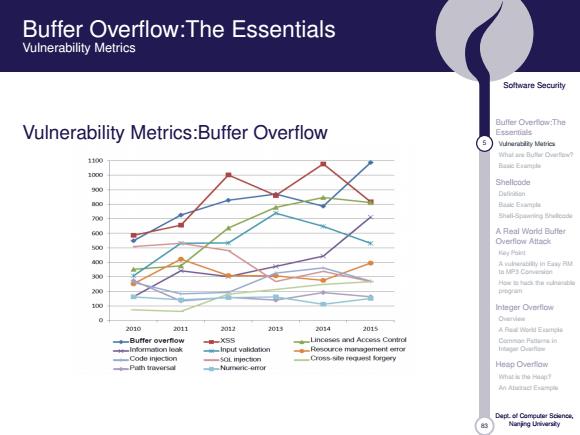
Buffer Overflow:The Essentials Vulnerability Metrics Soltware Security Vulnerability Metrics:Buffer Overflow Essentials 5 Mungrublzy Matrica 1100 Banc Elurnphe 1000 Shellcode Dufincien Shali-Spamning A Real Word Butter Overflow Attac比 学■n Inleger Overfiow Overvie 2010 2011 2012 201 2014 2015 Aah出E Butfer overflow -Input validation Resource mangement etror Code inocoon SOL injection Hesp Overflaw mt士sM年到 M Ahead E-年 Naning Ueivarsiy
83 Software Security Buffer Overflow:The Essentials 5 Vulnerability Metrics What are Buffer Overflow? Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials Vulnerability Metrics Vulnerability Metrics:Buffer Overflow