
最 Control Flow Integrity
Control Flow Integrity

最鲁 Outline ·Threat Model 。Control Flow Graph Control Flow Integrity basic implementation Build CFG Instrumentation Evaluation Security and Adversary ·Binary-CFI(CCFIR) - Introduce Implementation Context-Sensitive CFl Context Sensitivity Problems - Context Sensitivity Problems Shadow Call Stack RAP Context-Sensitive CFI 2
2 Outline • Threat Model • Control Flow Graph • Control Flow Integrity basic implementation – Build CFG – Instrumentation – Evaluation – Security and Adversary • Binary-CFI(CCFIR) – Introduce – Implementation – Context-Sensitive CFI • Context Sensitivity Problems – Context Sensitivity Problems – Shadow Call Stack – RAP – Context-Sensitive CFI
最鲁 Threat Model 3
Threat Model 3
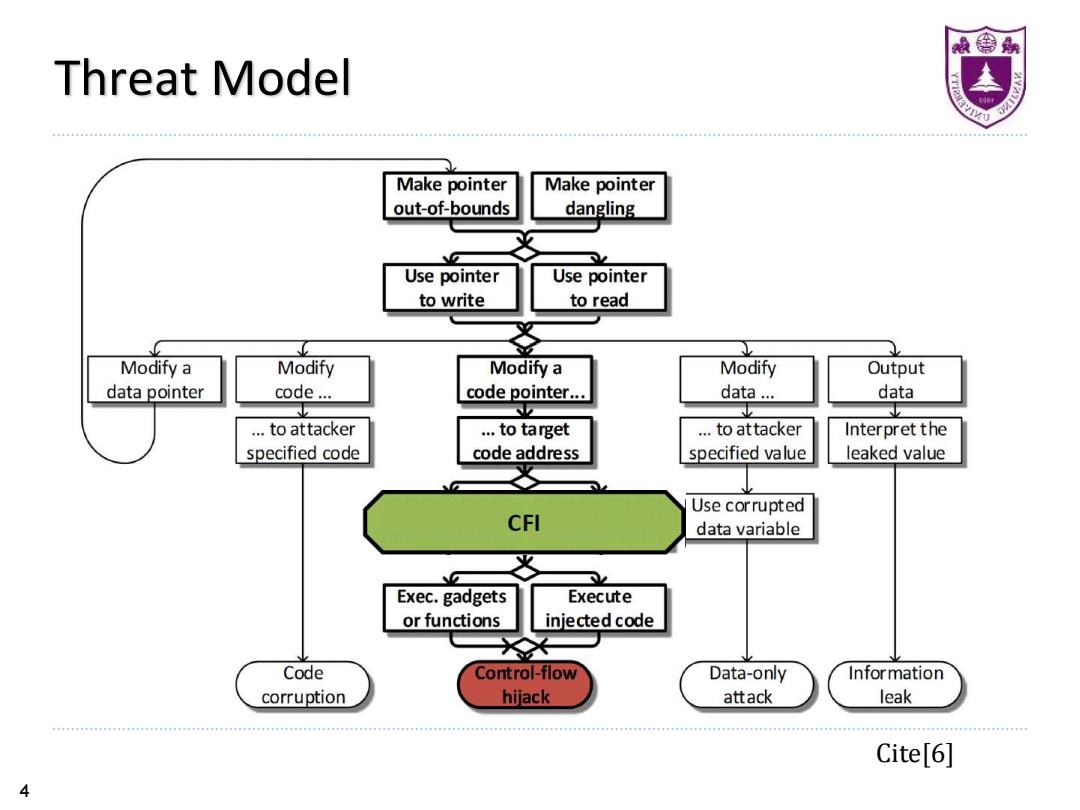
最鲁 Threat Model Make pointer Make pointer out-of-bounds dangling Use pointer Use pointer to write to read Modify a Modify Modify a Modify Output data pointer code... code pointer... data... data …to attacker ..to target ..to attacker Interpret the specified code code address specified value leaked value Use corrupted CFI data variable Exec.gadgets Execute or functions injected code Code Control-flow Data-only Information corruption hijack attack leak Cite[6] 4
4 Threat Model Cite[6]

最 Control Flow Graphs 5
Control Flow Graphs 5