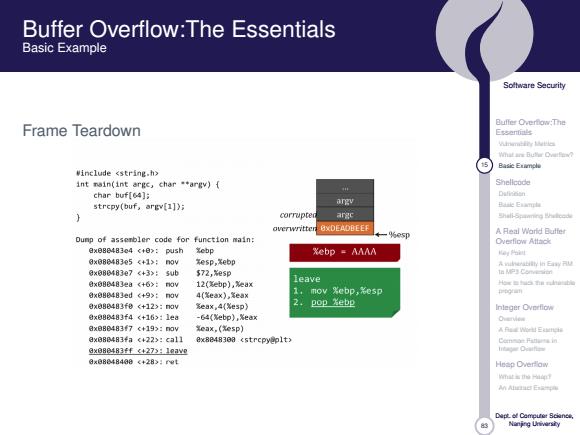
Buffer Overflow:The Essentials Basic Example Soltware Security Frame Teardown Essentials 5 Basic Etimple winclude <string.h> int main(int arge,char "argv){ Shellcode char buf[64]; Dulineisn strcpy(buf,ary[1]》i angv corrupten argc Shali-Spanmning overwnitter 5:0B401EE A Real Word Butter Dunp of asserbler code for function main: Overflow Attac比 日x888483c4c+8>:Push Zebp Xebp AAAA 0x088483e5(+1>:0w zesp,Zebp 0x080483e7<+3>:sub 事72,esp 0x08B483ea<+6>:3v 12(Xebp),%eax leave 0x88483ed<+9>:n3v 4(%eax),ea× 1 mov Xebp,名esp 学■n 0x888483fe<+12>:n3v %eaX,4(%esp】 2 pop Xebp Inleger Overfiow 0x088483f4<+16):1ea -64(%ebp),%eax Owerve ax880483f7《+193:nav eax,(esp) Aah出E 0x0804834a《+223:ca11 8x8848308 <strcpyeplt> 已nmoe Fatlinta 0x8B483ff《4273110w里 0x8B848498(+28>1et Hesp Overflow m过士aM年 Ahead Ex-年 Naning Ueivarsity
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? 15 Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials Basic Example Frame Teardown

Buffer Overflow:The Essentials Basic Example Soltware Security Frame Teardown Essentials Basic Etimple #include <string.h> int main(int argc.char argv){ Shellcode char buf[64]: Dulineisn strcpy(buf,argv(1]); argv corrupted 专一%esp Shali-Spanmning A Real Word Butter Dunp of asserbler code for function main: Overflow Attac比 axe83483e4《+8):pu5h Xebp 8xe©0483e5c+1):m0w xesp,%ebp 0x09348307(43): sub $72,zesp 0x883483ea《+6):m0W 12(¥ebp),eax eip 0xDEADBEEF 0×883483ed(+9>:0W 4(eax),ea× (probably crush) 学■n 0x883483fB(+12>:m0W ¥ea×,4(305p】 Inleger Overfiow 8×880483f4(+15>:10a -64(Zobp).xeax Overveu 0×883483f7c+19>:m0y ex,(¥esp) Aah出E 0×080483fa<+22>:ca11 0x8048300 <strcpyeplt> 已nmoe Faturta in 0x099483ff+27>:1eave lrtagar Diuifen gx88948480<+28>:nrL Hesp Overflow m过士aM年 Ahead Ex=年 Naning Ueivarsity
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? 16 Basic Example Shellcode Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Buffer Overflow:The Essentials Basic Example Frame Teardown

Shellcode Definition Soltware Security Bufler Overflow;The Essentials What's Shellcode? B4eEi山 Shellcode Traditionally,shellcode is byte code that executes a shell. Definiien Shellcode now has a broader meaning,to define the code Shali-Spanmning that is executed when an exploit is successful.The purpose A Real Word Butter Overflow Attac比 of most shellcode is to return a shell address,but many shellcodes exist for other purposes such as breaking out og每ta nhatb of a chroot shell,creating a file,and proxying system calls. 学■n Inleger Overfiow Owerve AAdM出En 已nmon F4n lrtagar Diuifen Hesp Overflow m过士aM年 Ahead Ex=年 Nanjng Uivarsiy
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? Basic Example Shellcode 17 Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Shellcode Definition What’s Shellcode? I Traditionally, shellcode is byte code that executes a shell. Shellcode now has a broader meaning, to define the code that is executed when an exploit is successful.The purpose of most shellcode is to return a shell address, but many shellcodes exist for other purposes such as breaking out of a chroot shell, creating a file, and proxying system calls
Shellcode Definition Soltware Security Bufler Overflow;The Essentials Shellcode at ars But的O Executable content(Often called shell code or exploits) Banc Elurnphe Shellcode Usually,a shell should be started Defintion for remote exploits -input/output redirection via socket Shali-Spanmning use system call (execve)to spawn shell A Real Word Butter Overflow Attac比 Shell code can do practically anything e时行创 create a new user m位匀m 年每sh鞋nh change a user password 学■n bind a shell to a port(remote shell) Inleger Overfiow Overveu open a connection to the attacker machine Aad出E 已nmon F4n litagar Diaifes Hesp Overflow 过士sM Ahead Ex-年 Nanjng Urivarsiy
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? Basic Example Shellcode 18 Definition Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Shellcode Definition Shellcode I Executable content (Often called shell code or exploits) I Usually, a shell should be started I for remote exploits - input/output redirection via socket I use system call (execve) to spawn shell I Shell code can do practically anything I create a new user I change a user password I bind a shell to a port (remote shell) I open a connection to the attacker machine
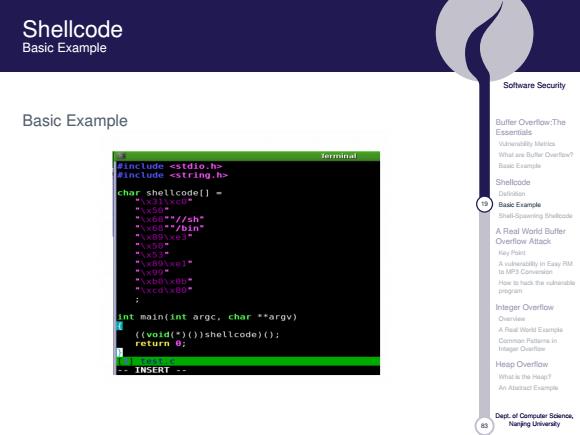
Shellcode Basic Example Soltware Security Basic Example Essentials Termninal 4 include←stdio.h> Banc Elurnphe include <string.h> Shellcode char shellcodel】- Dafieian Basie Erample “6//sh Shali-Spanrng -"/bin" A Real Warid Butfer Overflow Attac比 气×53 1 a的jm o每ta nhatib "\xcd\x80 学■n Inleger Overfiow int main(int argc.char argv) Overveu ((void(")())shellcode)(): Ad出E return 已mnmon F4n litagar Diaife INSERT Hesp Overflow m过士aM年 Ahead Ex-年 Nanjng Uivarsiy
83 Software Security Buffer Overflow:The Essentials Vulnerability Metrics What are Buffer Overflow? Basic Example Shellcode Definition 19 Basic Example Shell-Spawning Shellcode A Real World Buffer Overflow Attack Key Point A vulnerability in Easy RM to MP3 Conversion How to hack the vulnerable program Integer Overflow Overview A Real World Example Common Patterns in Integer Overflow Heap Overflow What is the Heap? An Abstract Example Dept. of Computer Science, Nanjing University Shellcode Basic Example Basic Example