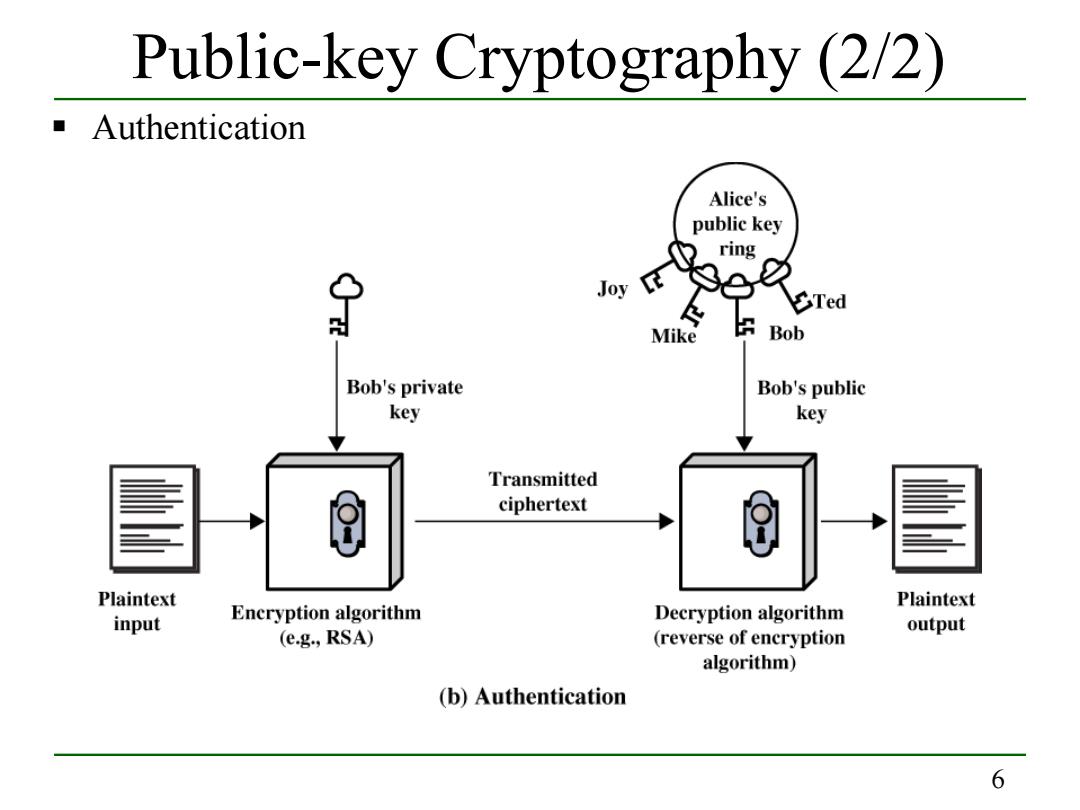
Public-key Cryptography (2/2) Authentication Alice's public key ring Joy 9e1 必 Ted Mike Bob Bob's private Bob's public key key Transmitted ciphertext Plaintext Plaintext Decryption algorithm input Encryption algorithm output (e.g.,RSA) (reverse of encryption algorithm) (b)Authentication 6
6 Public-key Cryptography (2/2) Authentication

Conventional and Public-Key Encryption Conventional Encryption Public-Key Encryption Needed to Work: Needed to Work: 1.The same algorithm with the same key is 1.One algorithm is used for encryption and used for encryption and decryption. a related algorithm for decryption with a pair of keys,one for encryption and one 2.The sender and receiver must share the for decryption. algorithm and the key. 2. The sender and receiver must each have Needed for Security: one of the matched pair of keys (not the same one). 1.The key must be kept secret. Needed for Security: 2.It must be impossible or at least impractical to decipher a message if the 1.One of the two keys must be kept secret. key is kept secret. 2.It must be impossible or at least 3.Knowledge of the algorithm plus impractical to decipher a message if one samples of ciphertext must be of the keys is kept secret. insufficient to determine the key. 3. Knowledge of the algorithm plus one of the keys plus samples of ciphertext must be insufficient to determine the other key. 7
7 Conventional and Public-Key Encryption

Public-Key Cryptosystem:Secrecy Cryptanalyst PRb Source A Destination B Message X Encryption Decryption Destination Source Algorithm Y=EPUb,X灯 Algorithm X= DPRb,Y门 PUb PRb Key Pair Source 8
8 Public-Key Cryptosystem: Secrecy
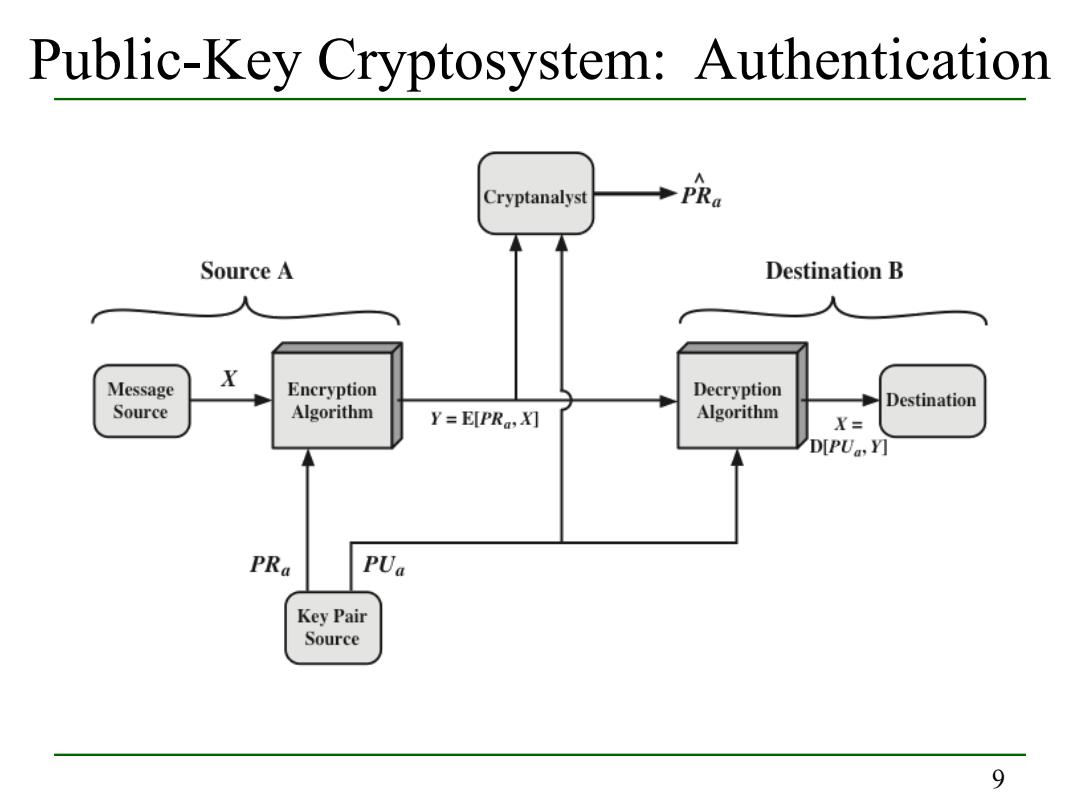
Public-Key Cryptosystem:Authentication Cryptanalyst PRa Source A Destination B Message X Encryption Decryption Destination Source Algorithm Y=EPRa,X灯 Algorithm X= D[PU,Y] PRa PUa Key Pair Source 9
9 Public-Key Cryptosystem: Authentication
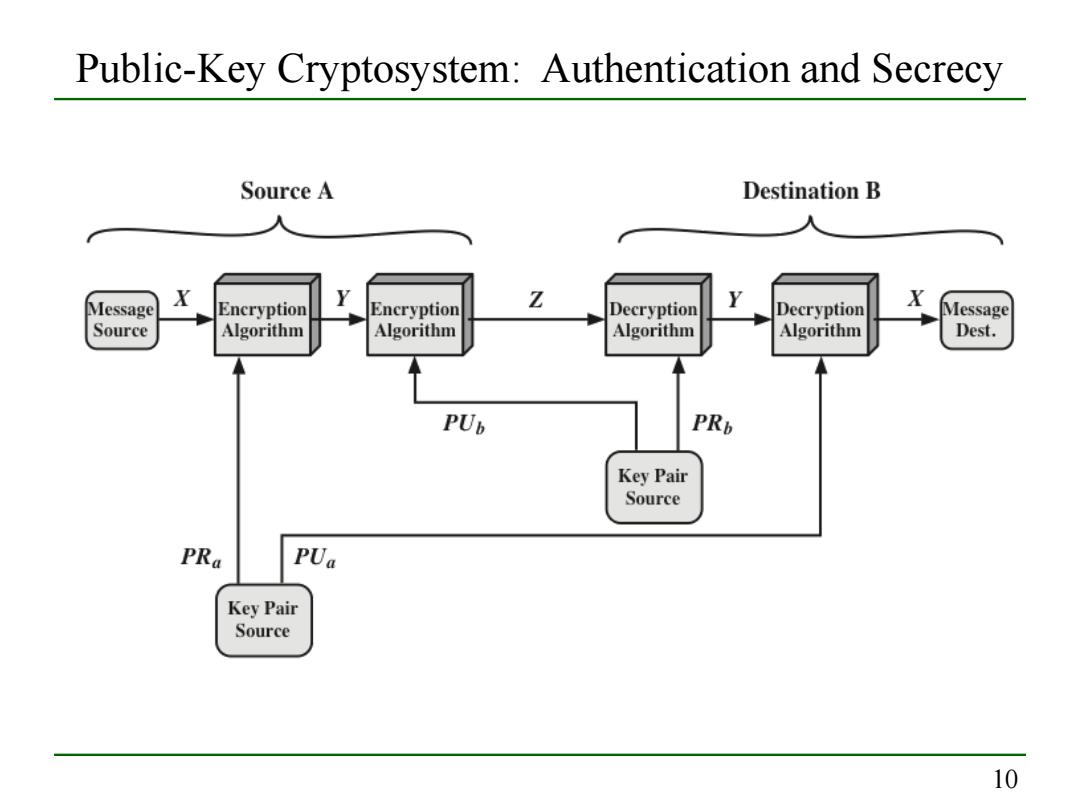
Public-Key Cryptosystem:Authentication and Secrecy Source A Destination B Message X Encryption Y Encryption Z Decryption Decryption X Message Source Algorithm Algorithm Algorithm Algorithm Dest. PUb PRb Key Pair Source PRa PUa Key Pair Source 10
10 Public-Key Cryptosystem: Authentication and Secrecy