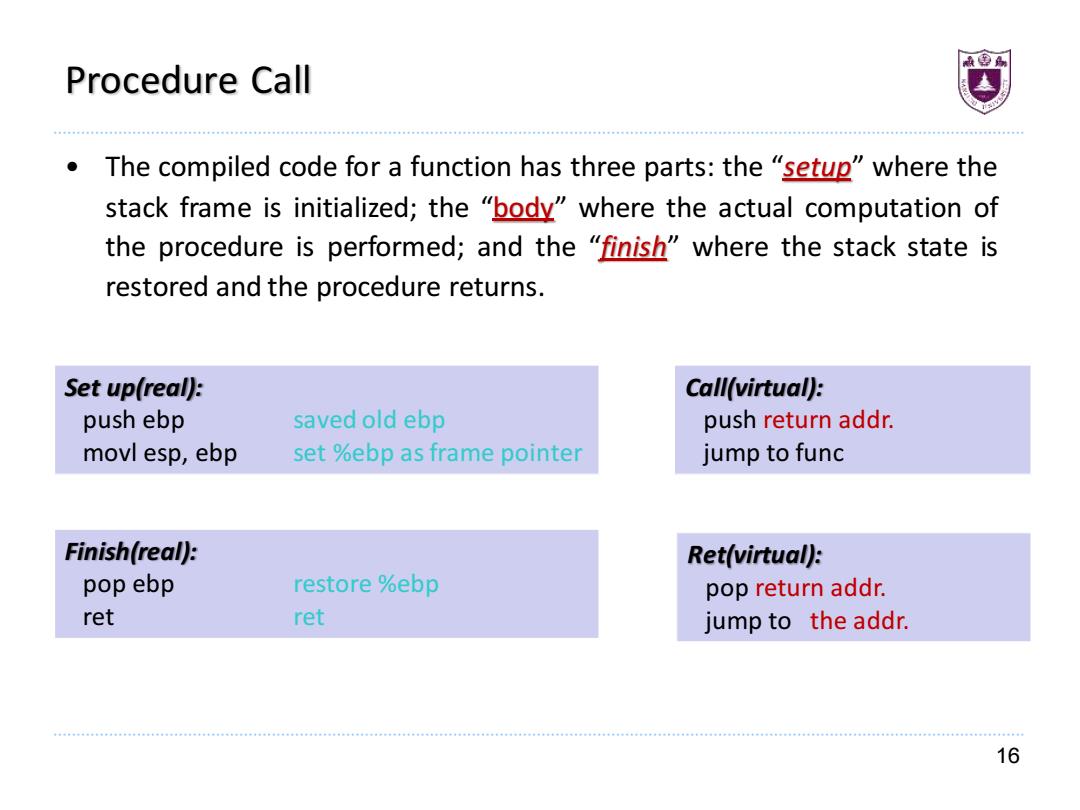
Procedure Call The compiled code for a function has three parts:the "setup"where the stack frame is initialized;the "body"where the actual computation of the procedure is performed;and the "finish"where the stack state is restored and the procedure returns. Set up(real): Call(virtual): push ebp saved old ebp push return addr. movl esp,ebp set %ebp as frame pointer jump to func Finish(real): Ret(virtual): pop ebp restore %ebp pop return addr. ret ret jump to the addr. 16
16 Procedure Call • The compiled code for a function has three parts: the “setup” where the stack frame is initialized; the “body” where the actual computation of the procedure is performed; and the “finish” where the stack state is restored and the procedure returns. Set up(real): push ebp saved old ebp movl esp, ebp set %ebp as frame pointer Finish(real): pop ebp restore %ebp ret ret Call(virtual): push return addr. jump to func Ret(virtual): pop return addr. jump to the addr

Stack Frame Structure 1 int swap_add(int *xp,int *yp) Just before call In body of 2 to swap_add swap_add 3 intx■*xp; Frame pointer 4 int y *yp; %ebp 0 Saved %ebp Saved %ebp 5 arg1 arg1 6 *x即=y: 7 *yp■x; 8 arg2 arg2 return x y; Stack frame 8 9 Unused for caller Unused 10 11 int caller() karg2 +12 karg2 12 { 13 int arg1 534; %esp- 0 karg1 +8 karg1 14 int arg2 1057; Stack pointer + Return address ■一▣=一=一 15 int sum swap_add(arg1,&arg2); 16 int diff arg1 -arg2; Frame pointer %ebp 0 Saved %ebp Stack frame 17 Stack pointer %esp Saved %ebx for swap_add return sum diff; 19 The key of the Buffer Overflow Attack!!! 17
17 Stack Frame Structure The key of the Buffer Overflow Attack!!!
Outline ·Background 0 Software Security:Control-flow Hijack Attack Memory Layout,Stack frame,Procedure Buffer Overflow:Vulnerability,&Defenses RILC,Return-Oriented Programming ASLR CFI Software Security:Non-control Data Attack Data Oriented Programming Summary 18
18 Outline • Background • Software Security: Control-flow Hijack Attack ➢ Memory Layout , Stack frame, & Procedure ➢ Buffer Overflow: Vulnerability, & Defenses ➢ RILC, Return-Oriented Programming ➢ ASLR & CFI • Software Security: Non-control Data Attack ➢ Data Oriented Programming • Summary