
What changes do Morris Worm bring to Computer Security? A real Buffer Overflow Attack Return Address Control flow Software Security 11
11 What changes do Morris Worm bring to Computer Security? A real Buffer Overflow Attack Software Security
Outline ·Background 0 Software Security:Control-flow Hijack Attack Memory Layout,Stack frame,Procedure Buffer Overflow:Vulnerability,Defenses RILC,Return-Oriented Programming ASLR CFI Software Security:Non-control Data Attack Data Oriented Programming Summary 12
12 Outline • Background • Software Security: Control-flow Hijack Attack ➢ Memory Layout , Stack frame, & Procedure ➢ Buffer Overflow: Vulnerability, & Defenses ➢ RILC, Return-Oriented Programming ➢ ASLR & CFI • Software Security: Non-control Data Attack ➢ Data Oriented Programming • Summary
Outline ·Background Software Security:Control-flow Hijack Attack Memory Layout,Stack frame,Procedure Buffer Overflow:Vulnerability,Defenses RILC,Return-Oriented Programming ASLR CFI Software Security:Non-control Data Attack Data Oriented Programming Summary 13
13 Outline • Background • Software Security: Control-flow Hijack Attack ➢ Memory Layout , Stack frame, & Procedure ➢ Buffer Overflow: Vulnerability, & Defenses ➢ RILC, Return-Oriented Programming ➢ ASLR & CFI • Software Security: Non-control Data Attack ➢ Data Oriented Programming • Summary
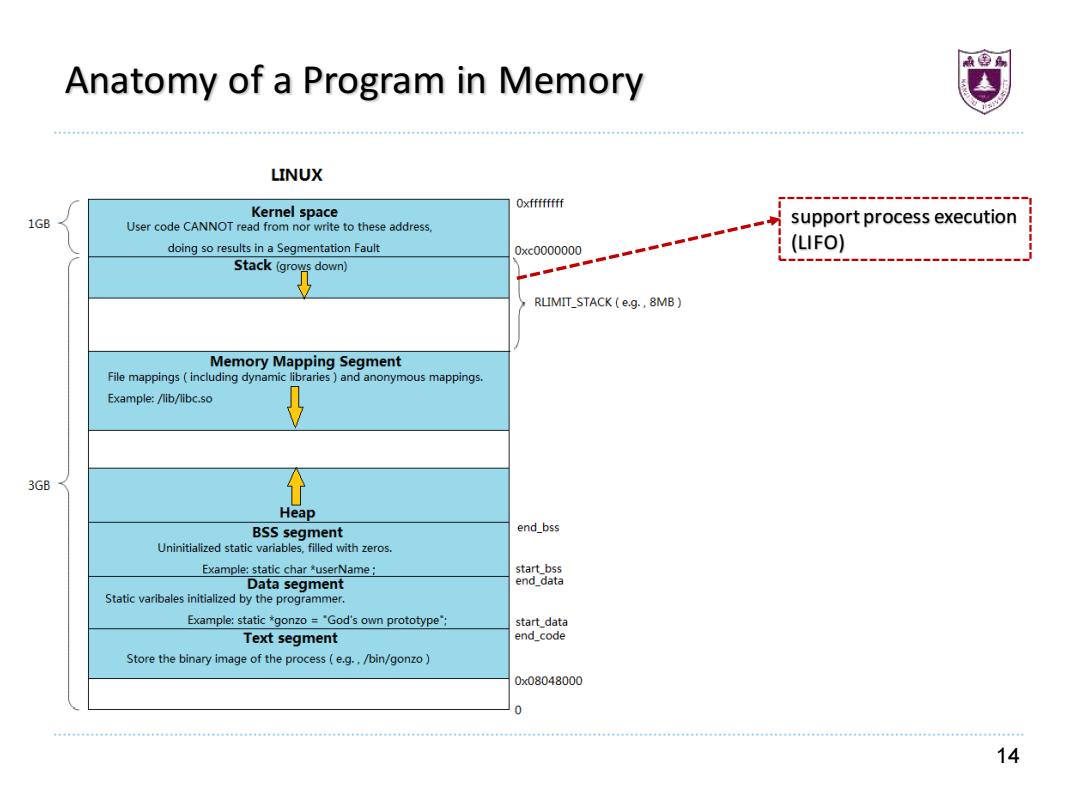
Anatomy of a Program in Memory LINUX Oxffffffff Kernel space 1GB User code CANNOT read from nor write to these address. support process execution doing so results in a Segmentation Fault 0xc0000000 (LIFO) Stack (grows down) RLIMIT_STACK(e.g..8MB) Memory Mapping Segment File mappings(including dynamic libraries and anonymous mappings. Example:/lib/libc.so 3GB Heap BSS segment end_bss Uninitialized static variables,filled with zeros. Example:static char *userName; start_bss Data segment end data Static varibales initialized by the programmer. Example:static *gonzo='God's own prototype": start data Text segment end_code Store the binary image of the process(e.g../bin/gonzo 0x08048000 0 14
14 Anatomy of a Program in Memory support process execution (LIFO)
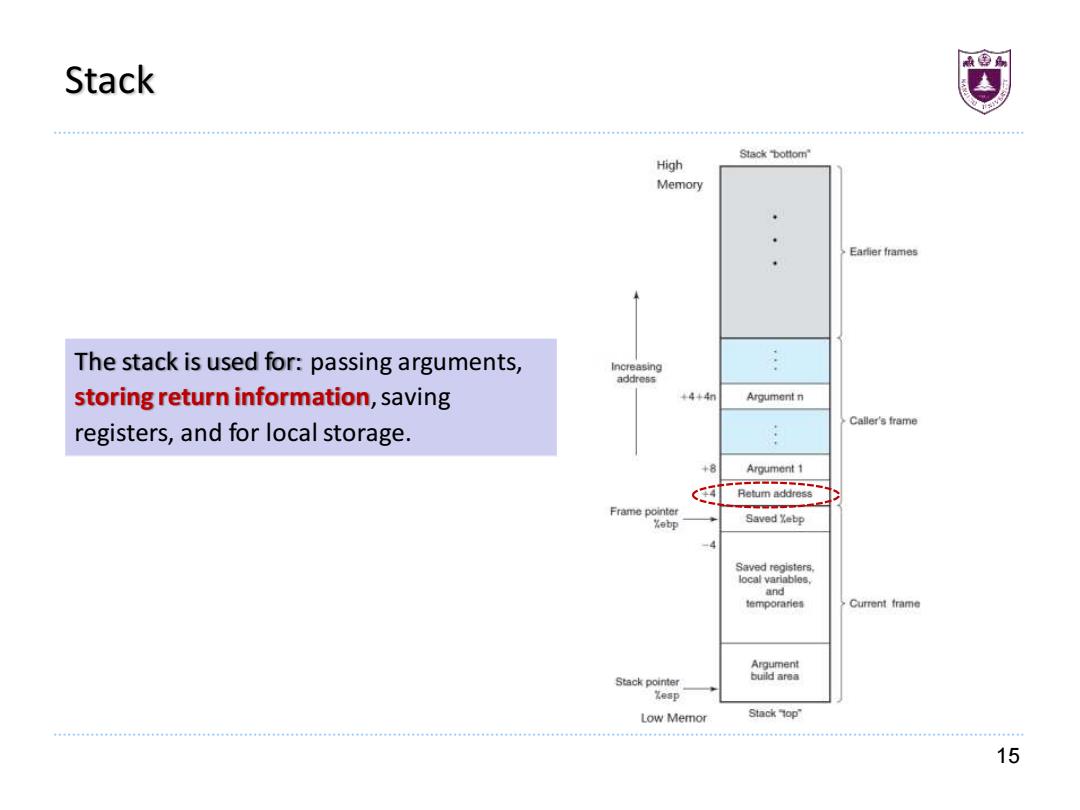
Stack Stackbottom" High Memory Earfier frames The stack is used for:passing arguments, Increasing address storing return information,saving 44+4n Argument n Caller's frame registers,and for local storage. +8 Argument 1 月etum address Frame pointer a明 Saved Yebp Saved registers. local variables. and temporaries Current frame Argument Stack pointer build area Yesp Low Memor Stack Top 15
15 Stack The stack is used for: passing arguments, storing return information, saving registers, and for local storage