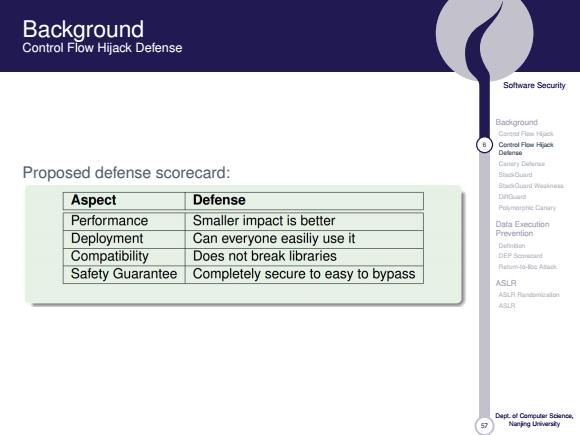
Background Control Flow Hijack Defense Soltware Security Background Cordol月e Definse Cattary Codenas Proposed defense scorecard: BS0au时 SOianT weaneu Aspect Defense DnG Puymnishie Cinin Performance Smaller impact is better Data Execution Deployment Can everyone easiliy use it Prevention Dutidan Compatibility Does not break libraries Fghim-ta-soc Arad Safety Guarantee Completely secure to easy to bypass ASLR ASLR Nanjng Urivarsiy
57 Software Security Background Control Flow Hijack 6 Control Flow Hijack Defense Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Background Control Flow Hijack Defense Proposed defense scorecard:

Canary-Based Protection Canary Defense Soltware Security Background Wikipedia:"the historic practice of using canaries in coal mines,since they would be affected by toxic gases earlier than )Carary Delarse the miners,thus providing a biological warning system." DnG Pulmnishie Cinin Data Execution Prevention Dutindan Canary Stack Cookies ASLR A9月
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense 7 Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Canary-Based Protection Canary Defense
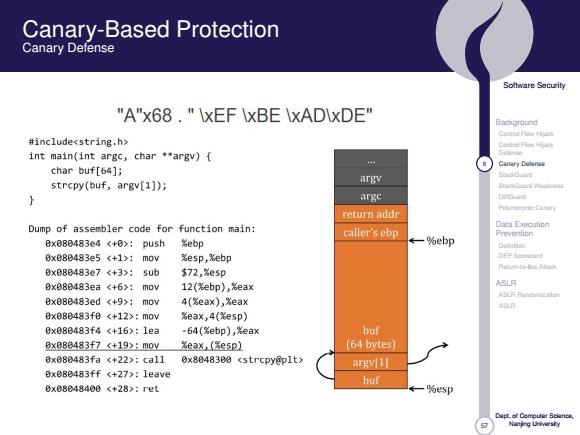
Canary-Based Protection Canary Defense Soltware Security "A"x68."IxEF IxBE \xADIxDE" Background Carerf Fies Hpck #include<string.h> int main(int argc,char *argv){ mMeo Cantary Delaree char buf[64]; s0a时 strcpy(buf,argv[1]); argv SOianT weiana argc DnG return addr Puymnishie Cinin Dump of assembler code for function main: Data Execution caller's ebp 0x080483e4<+0>:push Xebp ←一%ebp Prevention Dutidan 8xe80483e5<+1>:m0v %esp,%ebp 0x080483e7<+3>:sub $72,Xesp Bx888483ea<+6>:mov 12(%ebp),%eax ASLR ASL月月uo Bx880483ed(+9>:mov 4(影eax),%eax ASLR 8xe80483f8<+12>:mov eax,4(%esp) 8x080483f4<+16>:1ea -64(%ebp),Xeax buf 0x888483f7<+19>:m0w%eaX,(Xe5p】 (64 bytes) 0x08483fac+22>:ca110x80483e0(strcpy@p1t> argv[1l 8x080483ff《+27,:1eave buf 8x08048408《+28>:ret ←一%esp Nanjng Uivarsiy
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense 8 Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Canary-Based Protection Canary Defense
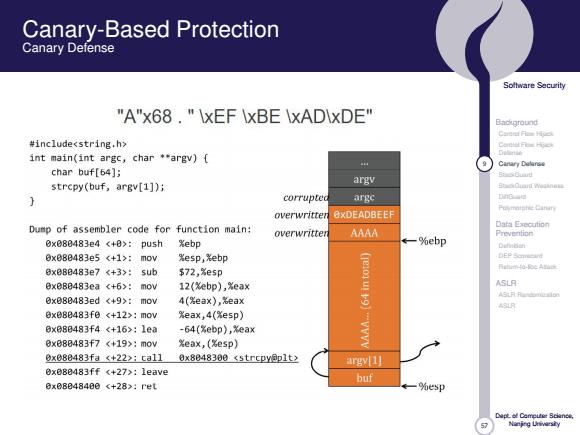
Canary-Based Protection Canary Defense Soltware Security "A"x68."IxEF IxBE \xADIxDE" Background Carerf Fies Hpck #includesstring.h> mMeo int main(int argc,char argv){ 4 Cantary Delaree char buf[64]; strcpy(buf,argv[1]); argv corrupte argc DnG overwritten OxDEADBEEF Puymnishie Cinin Dump of assembler code for function main: Data Execution overwritter AAAA 0x080483e4 <+0>:push %ebp -%ebp Prevention Dutidan 0xe88483e5<+1>:mov %esp,Xebp 9xe88483e7<+3>:sub $72,%e5p 0x0B0483ea <+6>:mov 12(%ebp),%eax ASLR AS月月o 0x08B483ed<+9>:mov 4(%eax),名eax ASLR 0x08B483f0<+12>:mov eax,4(%esp) 0xeBB483f4<+16>:1ea -64(Xebp),%eax 0xe88483f7<+19>:mov xeax,(%esp)】 0x088483fa<+22):ca110x8848308<5 trcpy@p1t2 argy 1] 0x888483ff(+27):1eave buf Bxe8B48488<+28>:ret %esp Naning Ueivarsiy
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense 9 Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Canary-Based Protection Canary Defense
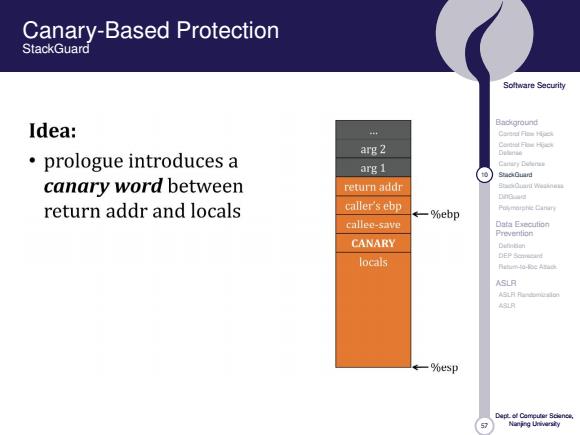
Canary-Based Protection StackGuard Soltware Security Idea: Background arg 2 e prologue introduces a arg 1 Cattary Dodenzs © ShackCurd canary word between return addr StaCianf Waaanat DnG return addr and locals caller's ebp ←-%ebp Puymnishie Cinin callee-save Data Execution Prevention CANARY Dutindan locals ASLR A9月 一%esp
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense Canary Defense 10 StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Canary-Based Protection StackGuard