Multi-threading support Pin supports multi-threading Application threads execute jit code including instrumentation code (inlined and not inlined),without any serialization introduced by Pin Instrumentation code can use Pin and/or OS synchronization constructs to introduce serialization if needed. Will see examples of this in Part4 >Pin provides APIs for thread local storage. Will see examples in Part3 Pin callbacks are serialized Jitting is serialized >Only one application thread can be jitting code at any time 11
Multi-threading support 11 • Pin supports multi-threading • Application threads execute jit code including instrumentation code (inlined and not inlined), without any serialization introduced by Pin ➢ Instrumentation code can use Pin and/or OS synchronization constructs to introduce serialization if needed. ✓ Will see examples of this in Part4 ➢ Pin provides APIs for thread local storage. ✓ Will see examples in Part3 • Pin callbacks are serialized • Jitting is serialized ➢ Only one application thread can be jitting code at any time
Pin Probe-Mode Probe mode is a method of using Pin to wrap or replace application functions with functions in the tool.A jump instruction(probe),which redirects the flow of control to the replacement function is placed at the start of the specified function. The bytes being overwritten are relocated,so that Pin can provide the replacement function with the address of the first relocated byte.This enables the replacement function to call the replaced (original) function. In probe mode,the application and the replacement routine are run native (not Jitted).This improves performance,but puts more responsibility on the tool writer.Probes can only be placed on RTN boundaries,and should inserted within the Image load callback.Pin will automatically remove the probes when an image is unloaded. Many of the PIN APIs that are available in JIT mode are not available in Probe mode. 12
Pin Probe-Mode • Probe mode is a method of using Pin to wrap or replace application functions with functions in the tool. A jump instruction (probe), which redirects the flow of control to the replacement function is placed at the start of the specified function. • The bytes being overwritten are relocated, so that Pin can provide the replacement function with the address of the first relocated byte. This enables the replacement function to call the replaced (original) function. • In probe mode, the application and the replacement routine are run native (not Jitted). This improves performance, but puts more responsibility on the tool writer. Probes can only be placed on RTN boundaries, and should inserted within the Image load callback. Pin will automatically remove the probes when an image is unloaded. • Many of the PIN APIs that are available in JIT mode are not available in Probe mode. 12
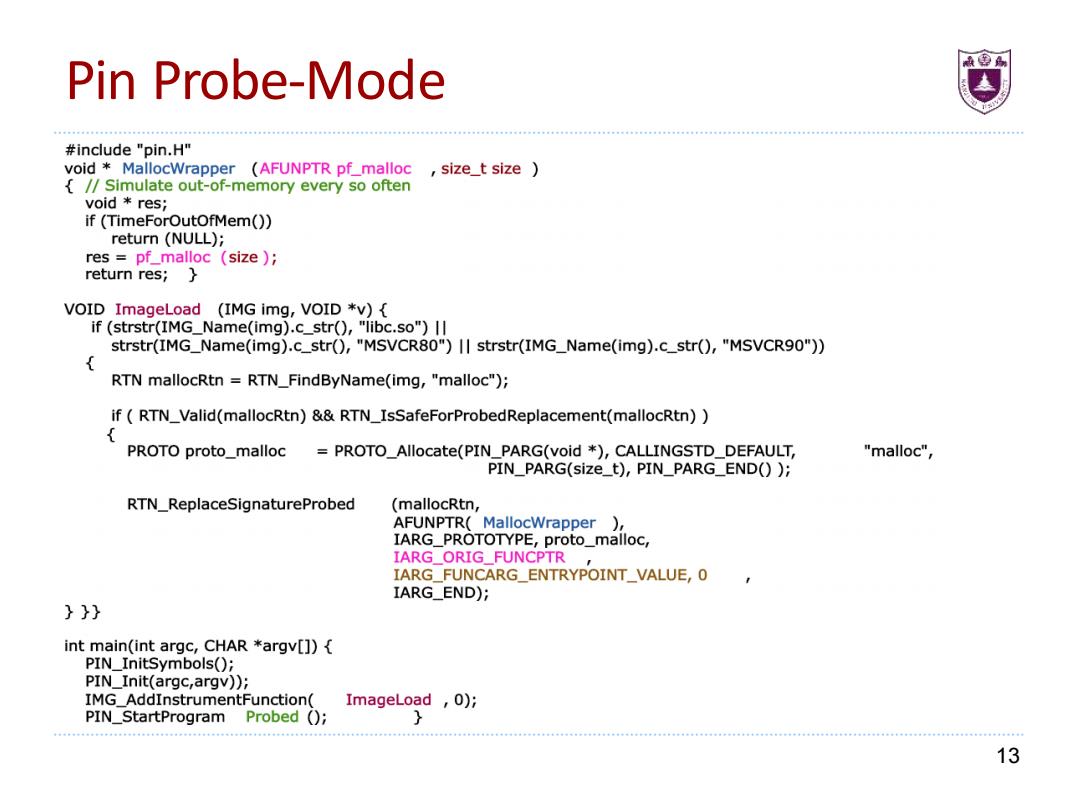
Pin Probe-Mode #include "pin.H" void MallocWrapper (AFUNPTR pf_malloc,size_t size /Simulate out-of-memory every so often void res; if(TimeForOutOfMem()) return (NULL); res pf_malloc (size ) return res; VOID ImageLoad (IMG img,VOID *v){ if (strstr(IMG_Name(img).c_str(),"libc.so")Il strstr(IMG_Name(img).c_str(),"MSVCR80")II strstr(IMG_Name(img).c_str(),"MSVCR90")) RTN mallocRtn RTN_FindByName(img,"malloc"); if(RTN_Valid(mallocRtn)&&RTN_IsSafeForProbedReplacement(mallocRtn)) { PROTO proto_malloc PROTO_Allocate(PIN_PARG(void *)CALLINGSTD_DEFAULT, "malloc", PIN_PARG(size_t),PIN_PARG_END()); RTN_ReplaceSignatureProbed (mallocRtn, AFUNPTR(MallocWrapper ) IARG_PROTOTYPE,proto_malloc, IARG ORIG FUNCPTR IARG_FUNCARG_ENTRYPOINT_VALUE,0 IARG_END); }} int main(int argc,CHAR *argv[]){ PIN_InitSymbols(; PIN_Init(argc,argv)); IMG_AddInstrumentFunction( ImageLoad ,0); PIN_StartProgram Probed () } 13
Pin Probe-Mode 13
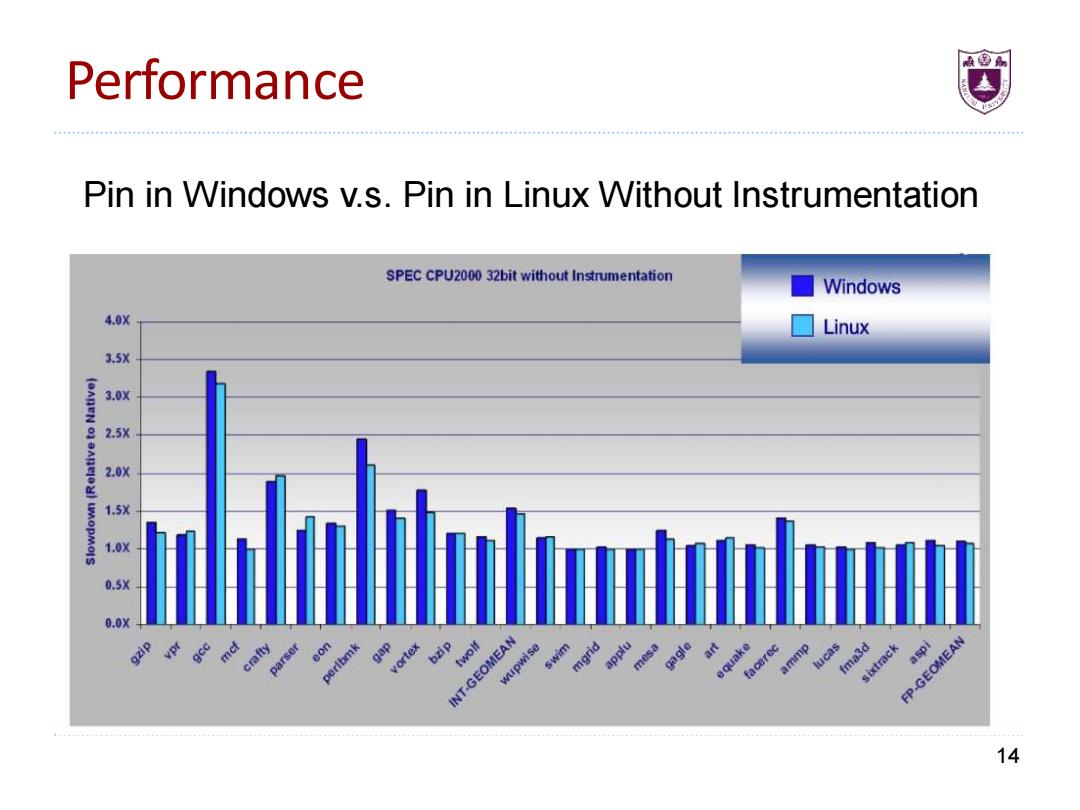
Performance Pin in Windows v.s.Pin in Linux Without Instrumentation SPEC CPU2000 32bit without Instrumentation Windows 4.0X Linux 3.5X 3.0X 2.5X 2.0X 1.5X 1.0X 0.5X 0.0X INT-GEOMEAN wupwise aspi e au facere mmp fma3d sixtrack FP-GEOMEAN 14
Performance 14 Pin in Windows v.s. Pin in Linux Without Instrumentation
Taint Analysis Introduction Basic concept Shadow Memory Introduction .Classify oftaint analysis >Statistic Taint Analysis >Dynamic Taint Analysis >Byte or bit ·Taint procedure Catch the syscalls > Spread the taint Taint analysis for security 15
Taint Analysis 15 • Introduction ➢ Basic concept ➢ Shadow Memory ➢ Introduction • Classify of taint analysis ➢ Statistic Taint Analysis ➢ Dynamic Taint Analysis ➢ Byte or bit • Taint procedure ➢ Catch the syscalls ➢ Spread the taint • Taint analysis for security