Classic Ciphers ■ We cover two examples: -Substitution Cipher (also called"monoalphabetic cipher") -Playfair Cipher 16
16 Classic Ciphers We cover two examples: ─ Substitution Cipher (also called “monoalphabetic cipher”) ─ Playfair Cipher
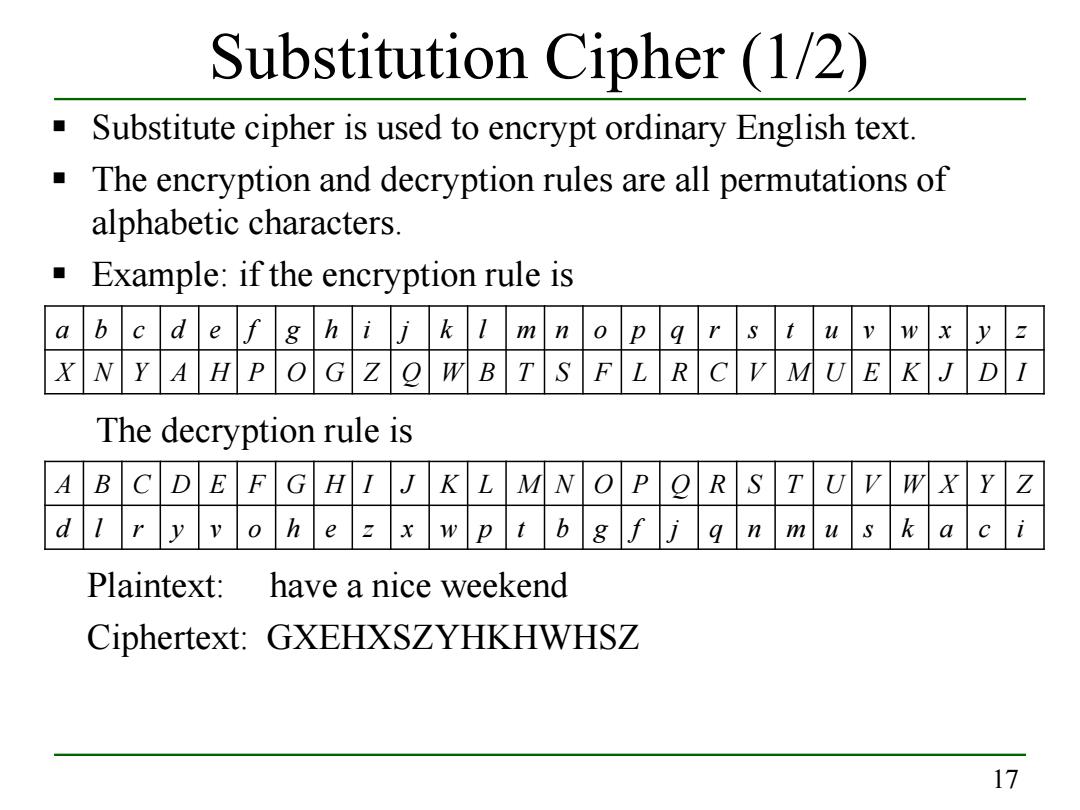
Substitution Cipher (1/2) Substitute cipher is used to encrypt ordinary English text. The encryption and decryption rules are all permutations of alphabetic characters. Example:if the encryption rule is a b c de f g h ijk 1 m n o p g r D wx y X NYAHPO G ZQWBTS FLRC VM U EKJ D I The decryption rule is A C D E FGHI JK L M N O T U VWX Y Z B d 1 r y v o h e z x w p t b g n m usk a c i Plaintext: have a nice weekend Ciphertext:GXEHXSZYHKHWHSZ 17
17 Substitution Cipher (1/2) Substitute cipher is used to encrypt ordinary English text. The encryption and decryption rules are all permutations of alphabetic characters. Example: if the encryption rule is The decryption rule is Plaintext: have a nice weekend Ciphertext: GXEHXSZYHKHWHSZ a b c d e f g h i j k l m n o p q r s t u v w x y z X N Y A H P O G Z Q W B T S F L R C V M U E K J D I A B C D E F G H I J K L M N O P Q R S T U V W X Y Z d l r y v o h e z x w p t b g f j q n m u s k a c i
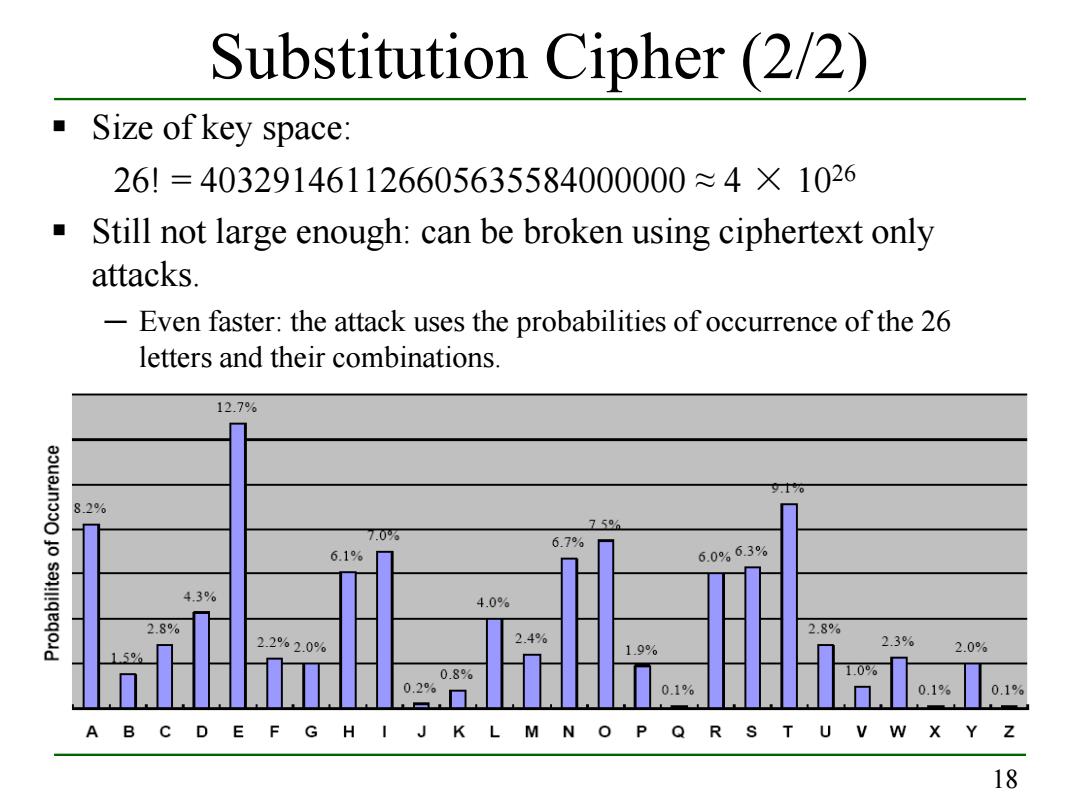
Substitution Cipher(2/2) Size of key space: 26!=403291461126605635584000000≈4×1026 Still not large enough:can be broken using ciphertext only attacks. -Even faster:the attack uses the probabilities of occurrence of the 26 letters and their combinations. 12.7% 8.2% 756 7.0% 6.7% 6.1% 6.0%6.3% 4.3% 4.0% 2.8% 2.2%2.0% 2.4% 2.8% 150 19% 2.3% 2.0% 0.8% 0.2% 0.1% 0.1% 0.1% A B CD EF G H I JK LM N O P Q R S T U V W X Y Z 18
18 Substitution Cipher (2/2) Size of key space: 26! = 403291461126605635584000000 ≈ 4 × 1026 Still not large enough: can be broken using ciphertext only attacks. ─ Even faster: the attack uses the probabilities of occurrence of the 26 letters and their combinations
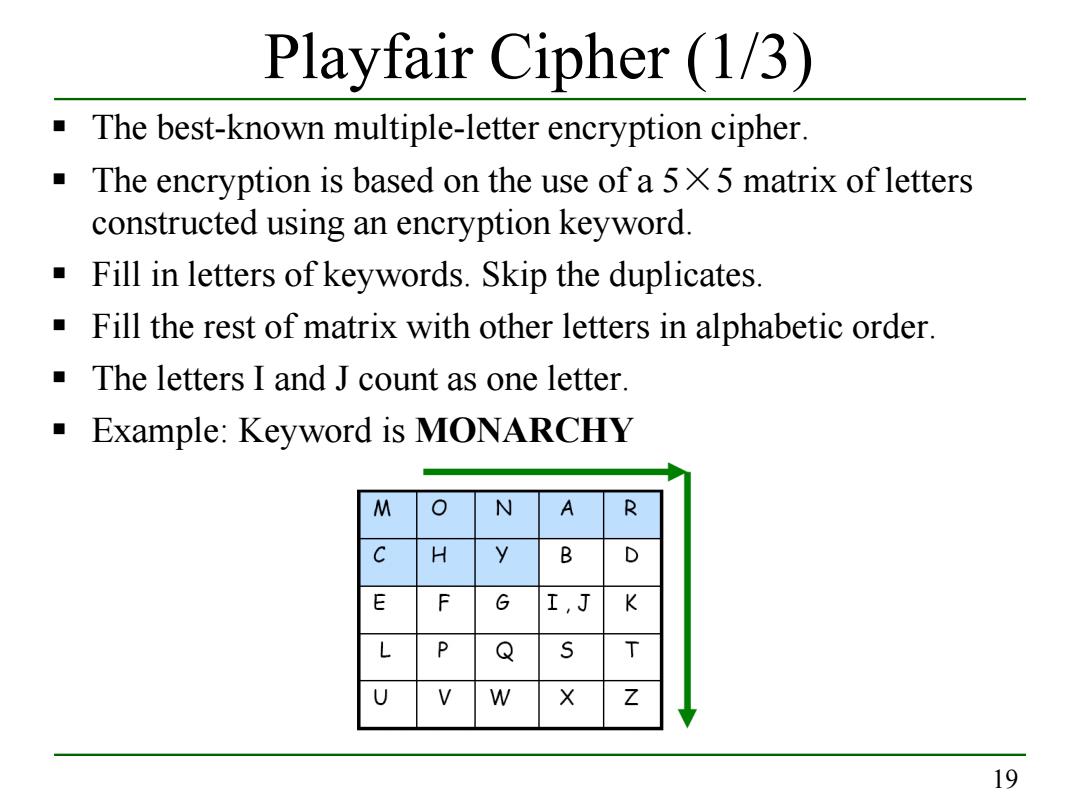
Playfair Cipher (1/3) The best-known multiple-letter encryption cipher The encryption is based on the use of a 5X5 matrix of letters constructed using an encryption keyword Fill in letters of keywords.Skip the duplicates. Fill the rest of matrix with other letters in alphabetic order. The letters I and J count as one letter. Example:Keyword is MONARCHY M N A R C H y B D E F G I,J K L P Q U V W Z 19
19 Playfair Cipher (1/3) The best-known multiple-letter encryption cipher. The encryption is based on the use of a 5×5 matrix of letters constructed using an encryption keyword. Fill in letters of keywords. Skip the duplicates. Fill the rest of matrix with other letters in alphabetic order. The letters I and J count as one letter. Example: Keyword is MONARCHY
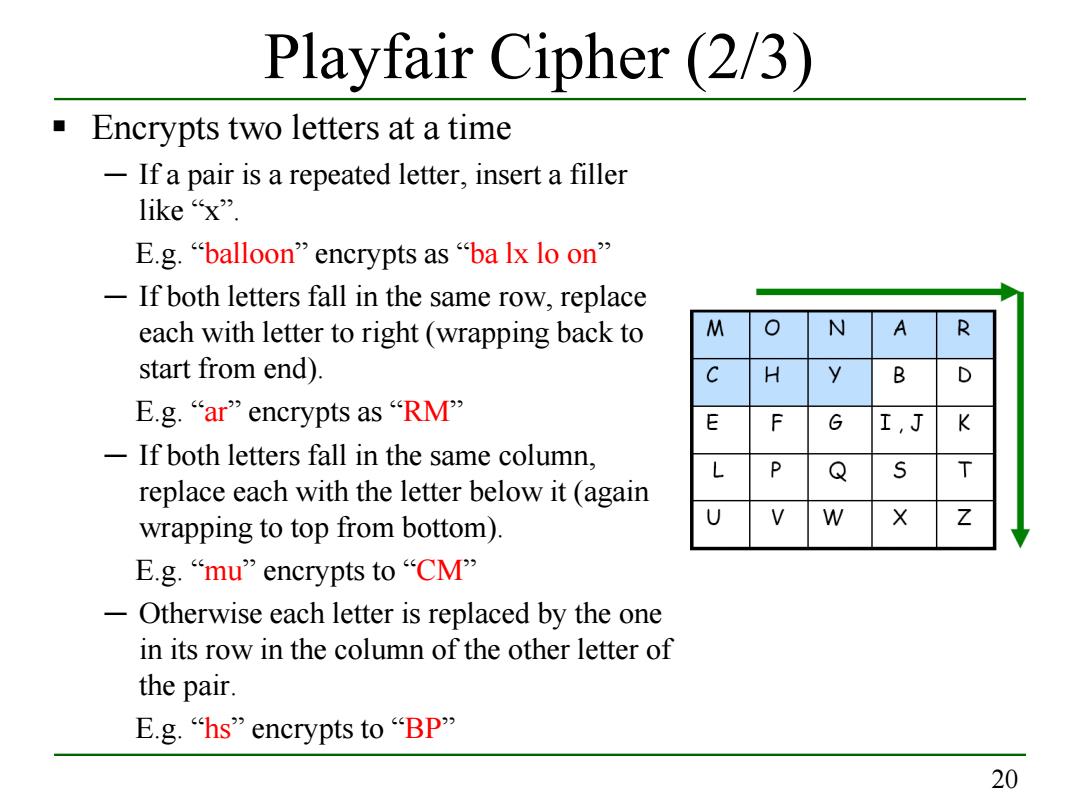
Playfair Cipher(2/3) Encrypts two letters at a time 一 If a pair is a repeated letter,insert a filler like“x”. E.g.“balloon”encrypts as“ba lx lo on' -If both letters fall in the same row,replace each with letter to right (wrapping back to M N R start from end). H B E.g.“ar”encrypts as“RMP E F G I,J K -If both letters fall in the same column, P Q T replace each with the letter below it (again wrapping to top from bottom). V W × Z E.g.“mu”encrypts to“CMP' 一 Otherwise each letter is replaced by the one in its row in the column of the other letter of the pair. E.g.hs”encrypts to "BP” 20
20 Playfair Cipher (2/3) Encrypts two letters at a time ─ If a pair is a repeated letter, insert a filler like “x”. E.g. “balloon” encrypts as “ba lx lo on” ─ If both letters fall in the same row, replace each with letter to right (wrapping back to start from end). E.g. “ar” encrypts as “RM” ─ If both letters fall in the same column, replace each with the letter below it (again wrapping to top from bottom). E.g. “mu” encrypts to “CM” ─ Otherwise each letter is replaced by the one in its row in the column of the other letter of the pair. E.g. “hs” encrypts to “BP