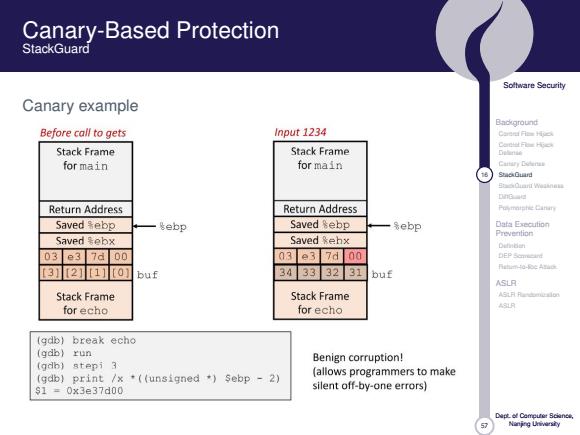
Canary-Based Protection StackGuard Soltware Security Canary example Background Before call to gets Input 1234 eae时AmHa Stack Frame Stack Frame mMeo for main for main Cattary Dodenzs SckGuird StaCiarf Waaanata DnG Return Address Return Address Puymnishie Cinin Saved号ebp 一%ebp Saved Sebp 一&ebp Data Execution Prevention Saved号ebx Saved %ehx Dutidan 03e37d00 03e37d00 [3]【2]【1]0] Fghim-ta-soc buf 34333231buf ASLR Stack Frame Stack Frame for echo for echo ASLR (gdb)break echo (gdb)run (gdb)stepi 3 Benign corruption! (gdb)print /x((unsigned Sebp -2) (allows programmers to make 91=0x3e37d00 silent off-by-one errors) 7 Nanjng Uivarsity
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense Canary Defense 16 StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Canary-Based Protection StackGuard Canary example
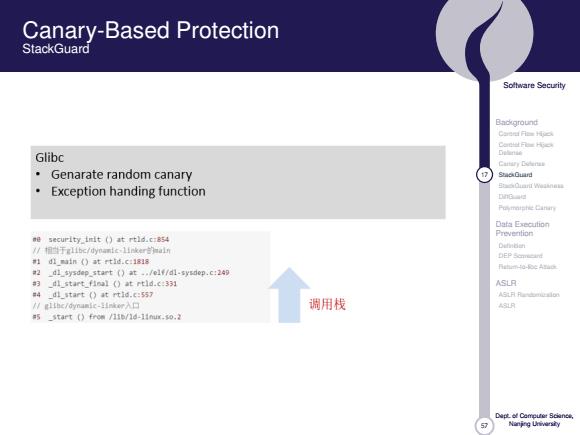
Canary-Based Protection StackGuard Soltware Security Background Carerf Fies Hpck Glibc Delinie Cattary Dodenzs Genarate random canary ⑦ScOurd Exception handing function StaCiarf Waaanata DnG Puymnishie Cinin Data Execution Prevention ee security init (at rtld.c:854 /相于rlibc/d小ynanic-linker的na1r Dh6的 m1 dlmain (at rtid.c:1818 #2 dl sysdep start (at ../elf/dl-sysdop.c:249 a3 dl start final (at rtld.c:331 ASLR #4_dl_start (at rtid.c:557 ASH月uB国 /1hc/dynamic-str入口 调用栈 ASLR a5 _start (from /110/1d-1inux.so.2 Nanjng Uivarsty
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense Canary Defense 17 StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Canary-Based Protection StackGuard
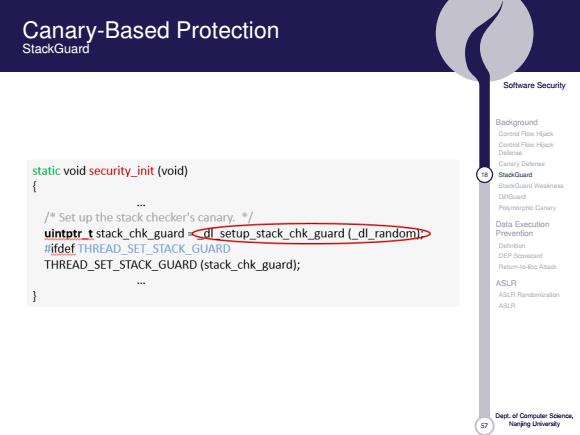
Canary-Based Protection StackGuard Soltware Security Background Carerf Fies Hpck Delinie Cattary Dodenzs static void security_init (void) SckGuird StaCiarf Waaanata DnG Puymnishie Cinin /Set up the stack checker's canary. Data Execution uintptr t stack_chk_guard<dl setup_stack_chk_guard (_dl_random Prevention #ifdef THREAD SET STACK GUARD Dh6的 THREAD_SET_STACK_GUARD(stack_chk_guard); ASLR ASH月uB国 ASLR Nanjng Urivarsiy
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense Canary Defense 18 StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Canary-Based Protection StackGuard
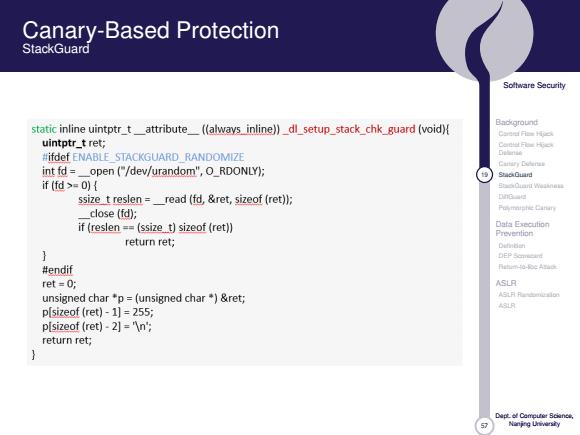
Canary-Based Protection StackGuard Soltware Security static inline uintptr_t_attribute((always_inline))dl_setup_stack_chk_guard (void){ Background Carerf Fies Hpck uintptr_t ret; #ifdef ENABLE STACKGUARD RANDOMIZE Delinie Cattary Codenas int fd=_open ("/dev/urandom",O_RDONLY); SnckGuird if(fd>=0){ StaCiarf Waaanata ssize t reslen =read (fd,&ret,sizeof (ret)); DnG _close(fd); Puymnishie Cinin if (reslen ==(ssize_t)sizeof (ret)) Data Execution Prevention return ret; Dutidan #endif ret=0; ASLR unsigned char "p=(unsigned char *)&ret; p[sizeof (ret)-1]=255; p[sizeof (ret)-2]="n'; return ret; Nanjng Uivarsty
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense Canary Defense 19 StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Canary-Based Protection StackGuard