
效绵 Ability enough gadgets for attack? English words vary in length,and there is no particular position on the page where a word must end and another start. Intel x86 code is like English written without punctuation or spaces,so that the words all run together. One can make out more words on the page than were intentionally placed there.Some words will be suffixes of other words,as "dress"is a suffix of "address";others will consist of the end of one word and the beginning of the next,as "head"can be found in "theaddress";and so on. 2023/2/7 6
2023/2/7 6 Ability ⚫ enough gadgets for attack? English words vary in length, and there is no particular position on the page where a word must end and another start. Intel x86 code is like English written without punctuation or spaces, so that the words all run together. One can make out more words on the page than were intentionally placed there. Some words will be suffixes of other words, as "dress" is a suffix of "address"; others will consist of the end of one word and the beginning of the next, as "head" can be found in "theaddress"; and so on
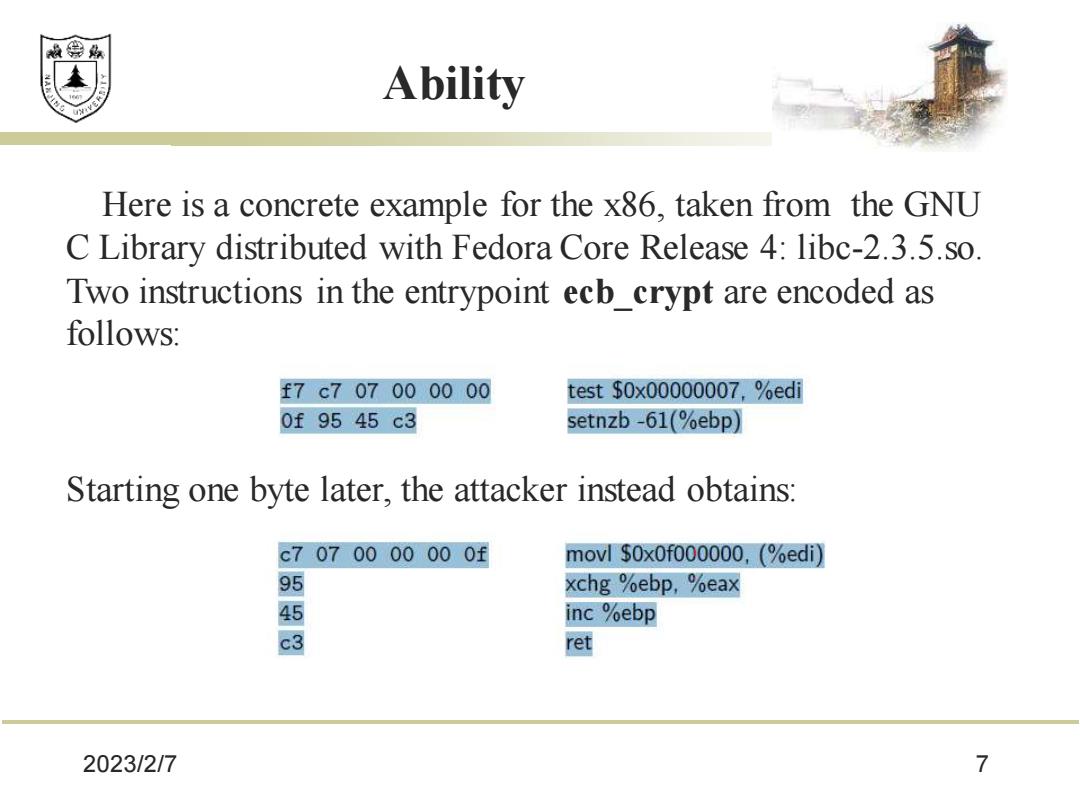
效绵鼎 Abilit女y Here is a concrete example for the x86,taken from the GNU C Library distributed with Fedora Core Release 4:libc-2.3.5.so. Two instructions in the entrypoint ecb_crypt are encoded as follows: f7c707000000 test$0x00000007,%ed 0f9545c3 setnzb-61(%ebp) Starting one byte later,the attacker instead obtains: c7070000000f movl $OxOf000000,(%edi) 9 xchg %ebp,%eax inc %ebp 3 ret 2023/2/7 7
2023/2/7 7 Ability Here is a concrete example for the x86, taken from the GNU C Library distributed with Fedora Core Release 4: libc-2.3.5.so. Two instructions in the entrypoint ecb_crypt are encoded as follows: Starting one byte later, the attacker instead obtains:

效绵 Abilit女y The set of gadgets described is Turing complete by inspection,so return-oriented programs can do anything possible with x86 code. 2023/2/7 8
2023/2/7 8 Ability The set of gadgets described is Turing complete by inspection, so return-oriented programs can do anything possible with x86 code
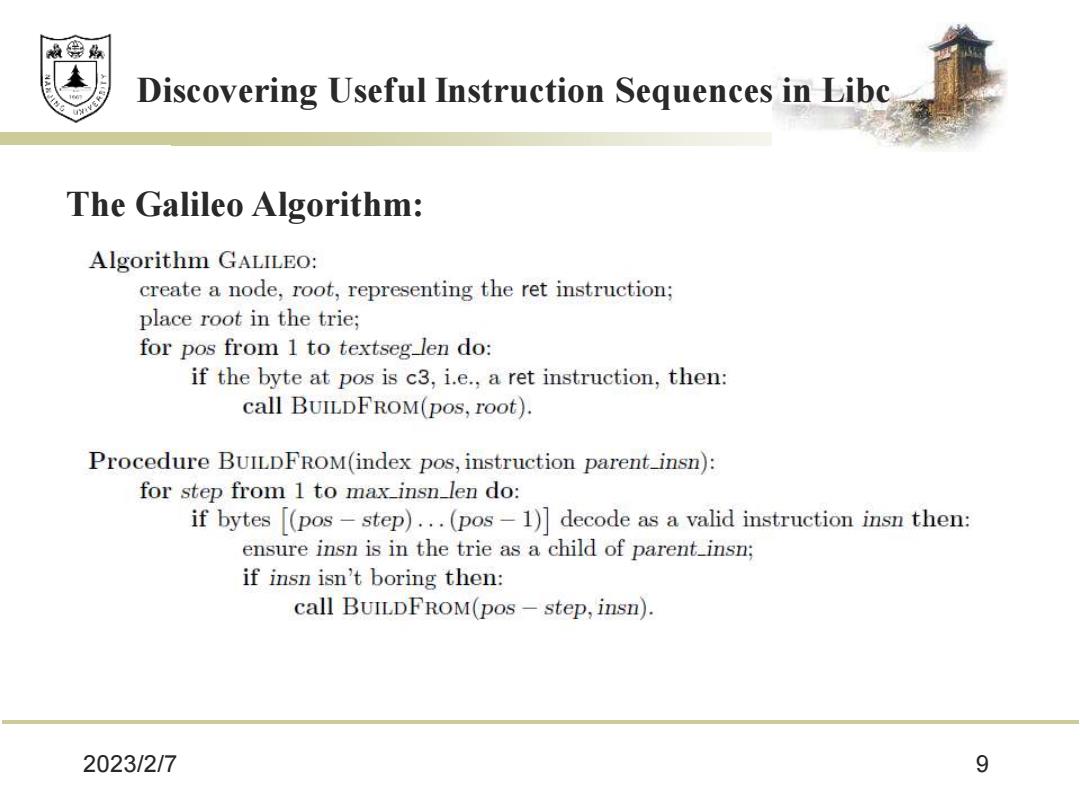
效绵县 Discovering Useful Instruction Sequences in Libc The Galileo Algorithm: Algorithm GALILEO: create a node,root,representing the ret instruction; place root in the trie; for pos from 1 to textseg len do: if the byte at pos is c3,i.e.,a ret instruction,then: call BUILDFROM(pos,root). Procedure BUILDFROM(index pos,instruction parent_insn): for step from 1 to max insn_len do: if bytes [(pos-step)...(pos-1)decode as a valid instruction insn then: ensure insn is in the trie as a child of parent insn; if insn isn't boring then: call BUILDFROM(pos-step,insn). 2023/2/7 9
2023/2/7 9 Discovering Useful Instruction Sequences in Libc The Galileo Algorithm:
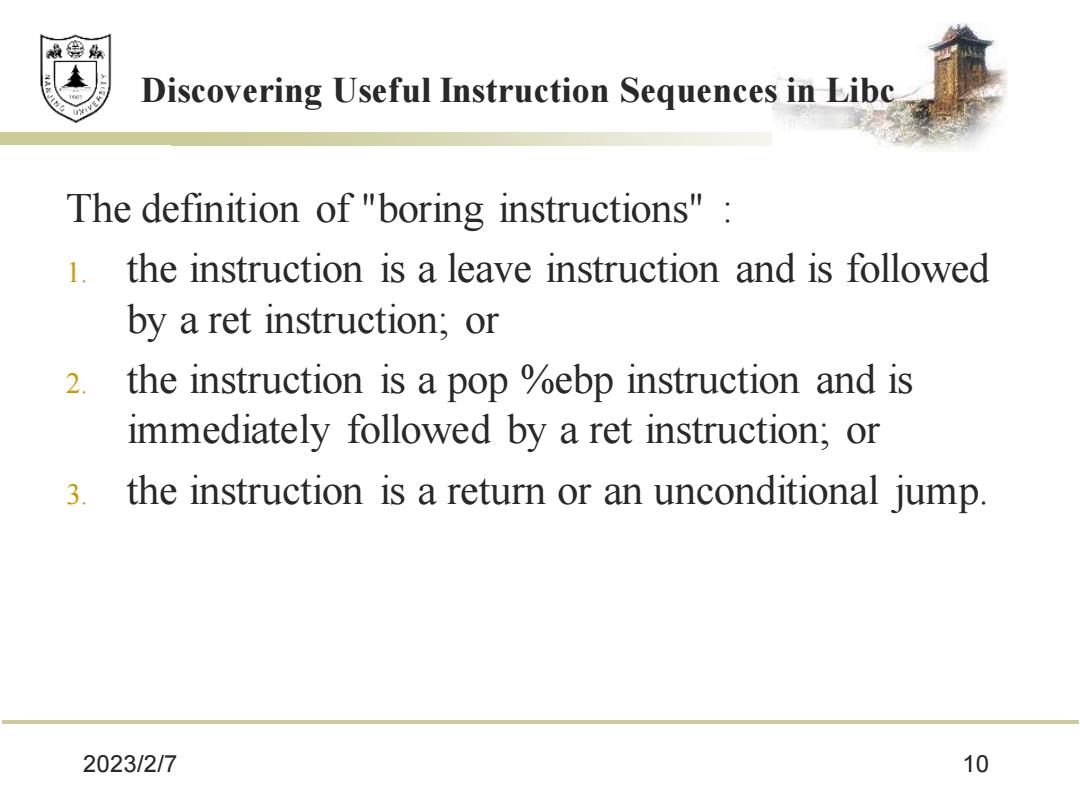
校绵鼎 Discovering Useful Instruction Sequences in Libc The definition of "boring instructions" 1.the instruction is a leave instruction and is followed by a ret instruction;or 2. the instruction is a pop %ebp instruction and is immediately followed by a ret instruction;or 3. the instruction is a return or an unconditional jump. 2023/2/7 10
2023/2/7 10 Discovering Useful Instruction Sequences in Libc The definition of "boring instructions" : 1. the instruction is a leave instruction and is followed by a ret instruction; or 2. the instruction is a pop %ebp instruction and is immediately followed by a ret instruction; or 3. the instruction is a return or an unconditional jump