
Embedding an ActiveX Control <HTML><HEAD> <TITLE>Draw a Square </TITLE> </HEAD> <BODY>Here is an example ActiveX reference: <OBJECT ID="Sample" CODEBASE="http://www.badsite.com/controls/stop.ocx" HEIGHT="101” WIDTH="101 CLASSID="clsid:0342D101-2EE9-1BAF-34565634EB71"> <PARAM NAME="Version"VALUE=45445"> <PARAM NAME="ExtentX"VALUE="3001"> <PARAM NAME="ExtentY"VALUE="2445"> </OBJECT> </BODY></HTML> 10/16/2016 Web Security 11
Embedding an ActiveX Control <HTML> <HEAD> <TITLE> Draw a Square </TITLE> </HEAD> <BODY> Here is an example ActiveX reference: <OBJECT ID="Sample“ CODEBASE="http://www.badsite.com/controls/stop.ocx" HEIGHT="101“ WIDTH="101“ CLASSID="clsid:0342D101-2EE9-1BAF-34565634EB71" > <PARAM NAME="Version" VALUE=45445"> <PARAM NAME="ExtentX" VALUE="3001"> <PARAM NAME="ExtentY" VALUE="2445"> </OBJECT> </BODY> </HTML> 10/16/2016 Web Security 11
Authenticode in ActiveX 】e Pan Duckyne This signed ActiveX control ask the user for Adt时包hp Do you wart to instal and run" permission to run Contiol"signed on 3/24/89 7:32 PM and datbule时y PLEASE WA If approved,the control Frgc5ch Inc Publihe authenticly vered by VenSign Coercial will run with the same Sofware Fublshers CA privileges as the user If your browser Cauion:TegoSo Inc serts thatths conent is safe ns itself。 Otherwise,you YUh3e0 ny nstal/vew的content if you时 Tego5 oft Inc to make thet astetion The "Always trust .Downloa any directory content from..." .Execute yru contert om Tegoof Inc. No Mote irto checkbox automatically accepts controls by the Opering page Htp://www.tegnsolt.ccm/WabProgtams/parducl Inteinet same publisher 用5 t☑)回The Pan Ducky Prog 包QDn102M Probably a bad idea Malicious Mobile Code,by R.Grimes,O'Reilly Books 10/16/2016 Web Security 12
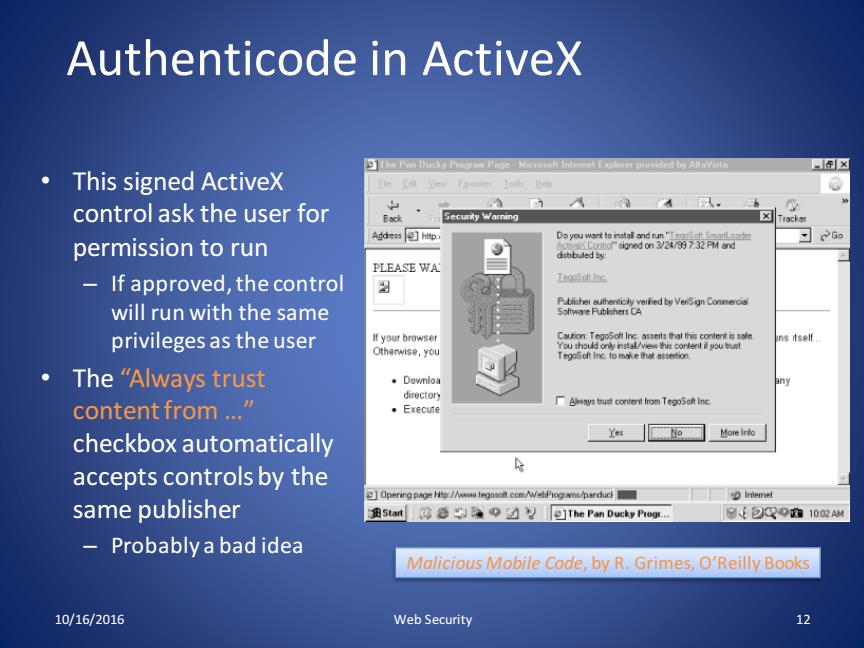
Authenticode in ActiveX • This signed ActiveX control ask the user for permission to run – If approved, the control will run with the same privileges as the user • The “Always trust content from …” checkbox automatically accepts controls by the same publisher – Probably a bad idea 10/16/2016 Web Security 12 Malicious Mobile Code, by R. Grimes, O’Reilly Books

Cookies Cookies are a small bit of information stored on a computer associated with a specific server When you access a specific website,it might store information as a cookie 一 Every time you revisit that server,the cookie is re-sent to the server - Effectively used to hold state information over sessions Cookies can hold any type of information Can also hold sensitive information This includes passwords,credit card information,social security number,etc. Session cookies,non-persistent cookies,persistent cookies Almost every large website uses cookies 10/16/2016 Web Security 13
Cookies • Cookies are a small bit of information stored on a computer associated with a specific server – When you access a specific website, it might store information as a cookie – Every time you revisit that server, the cookie is re-sent to the server – Effectively used to hold state information over sessions • Cookies can hold any type of information – Can also hold sensitive information • This includes passwords, credit card information, social security number, etc. • Session cookies, non-persistent cookies, persistent cookies – Almost every large website uses cookies 10/16/2016 Web Security 13

More on Cookies Cookies are stored on your computer and can be controlled However,many sites require that you enable cookies in order to use the site Their storage on your computer naturally lends itself to exploits(Think about how ActiveX could exploit cookies...) You can (and probably should)clear your cookies on a regular basis Most browsers will also have ways to turn off cookies,exclude certain sites from adding cookies,and accept only certain sites'cookies Cookies expire The expiration is set by the sites'session by default,which is chosen by the server This means that cookies will probably stick around for a while 10/16/2016 Web Security 14
More on Cookies • Cookies are stored on your computer and can be controlled – However, many sites require that you enable cookies in order to use the site – Their storage on your computer naturally lends itself to exploits (Think about how ActiveX could exploit cookies...) – You can (and probably should) clear your cookies on a regular basis – Most browsers will also have ways to turn off cookies, exclude certain sites from adding cookies, and accept only certain sites' cookies • Cookies expire – The expiration is set by the sites' session by default, which is chosen by the server – This means that cookies will probably stick around for a while 10/16/2016 Web Security 14

Cross Site Scripting (XSS) Attacker injects scripting code into pages generated by a web application Script could be malicious code JavaScript(AJAX!),VBScript,ActiveX,HTML,or Flash ·Threats: Phishing,hijacking,changing of user settings,cookie theft/poisoning,false advertising,execution of code on the client,.. 10/16/2016 Web Security 15
Cross Site Scripting (XSS) • Attacker injects scripting code into pages generated by a web application – Script could be malicious code – JavaScript (AJAX!), VBScript, ActiveX, HTML, or Flash • Threats: – Phishing, hijacking, changing of user settings, cookie theft/poisoning, false advertising , execution of code on the client, ... 10/16/2016 Web Security 15