
15 18.2入侵检测 有效的入侵检测系统可以看成阻止入侵的屏障 ● 入侵检测可以收集入侵技术的信息,用以增强入侵 阻止工具 入侵检测建立的前提是假设入侵者的行为在某些情 况下不同于合法用户的行为,然而两者仍有重叠部 分。放宽定义入侵者行为,会发现更多的入侵者, 也会产生大量的“错误肯定” 为减少错误肯定,严格定义入侵者的行为,将导致 错误否定的增加,即无法判断出入侵者。因此在入 侵的实践中存在巧妙的折衷 2022/10/9 现代密码学理论与实践-18入侵者 12/48
2022/10/9 现代密码学理论与实践-18 入侵者 12/48 18.2 入侵检测 ⚫ 有效的入侵检测系统可以看成阻止入侵的屏障 ⚫ 入侵检测可以收集入侵技术的信息,用以增强入侵 阻止工具 ⚫ 入侵检测建立的前提是假设入侵者的行为在某些情 况下不同于合法用户的行为,然而两者仍有重叠部 分。放宽定义入侵者行为,会发现更多的入侵者, 也会产生大量的“错误肯定” ⚫ 为减少错误肯定,严格定义入侵者的行为,将导致 错误否定的增加,即无法判断出入侵者。因此在入 侵的实践中存在巧妙的折衷

至 入侵者和授权用户行为形态 1050 Probability density function profile of profile of authorized user intruder behavior behavior overlap in observed or expected behavior average behavior Measurable behavior average behavior of intruder of authorized user parameter Figure 18.1 Profiles of Behavior of Intruders and Authorized Users ■】 2022/10/9 现代密码学理论与实践-18入侵者 13/48
2022/10/9 现代密码学理论与实践-18 入侵者 13/48 入侵者和授权用户行为形态

南冷式不才 入侵检测方法 1950 统计异常检测Statistical anomaly detection,定 义通常的或期望的行为 ·阈值检测Treshold detection ●基于形态的检测Profile based 基于规则的检测Rule based detection,定义合适 的行为 ●异常检测Anomaly detection ●渗透识别Penetration identidication ●1 审计记录,入侵检测的基本工具 ●原有审计记录 。专门用于检测的审计记录 2022/10/9 现代密码学理论与实践-18入侵者 14/48
2022/10/9 现代密码学理论与实践-18 入侵者 14/48 入侵检测方法 ⚫ 统计异常检测Statistical anomaly detection,定 义通常的或期望的行为 ⚫ 阈值检测Treshold detection ⚫ 基于形态的检测Profile based ⚫ 基于规则的检测Rule based detection,定义合适 的行为 ⚫ 异常检测Anomaly detection ⚫ 渗透识别Penetration identidication ⚫ 审计记录,入侵检测的基本工具 ⚫ 原有审计记录 ⚫ 专门用于检测的审计记录
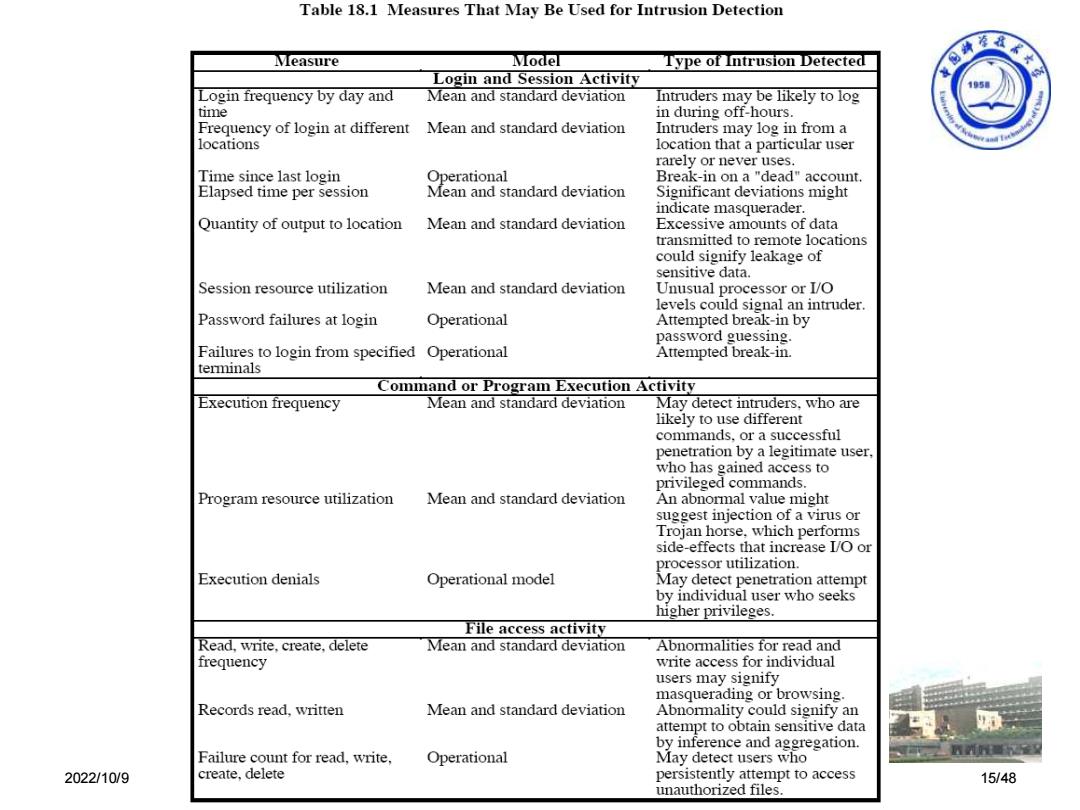
Table 18.1 Measures That May Be Used for Intrusion Detection Measure Model Type of Intrusion Detected 海径K欢 Login and Session Activity 15 Login frequency by day and Mean and standard deviation Intruders may be likely to log time in during off-hours. Frequency of login at different Mean and standard deviation Intruders may log in from a locations location that a particular user rarely or never uses. Time since last login Operational Break-in on a "dead"account. Elapsed time per session Mean and standard deviation Significant deviations might indicate masquerader. Quantity of output to location Mean and standard deviation Excessive amounts of data transmitted to remote locations could signify leakage of sensitive data. Session resource utilization Mean and standard deviation Unusual processor or I/O levels could signal an intruder. Password failures at login Operational Attempted break-in by password guessing. Failures to login from specified Operational Attempted break-in. terminals Command or Program Execution Activity Execution frequency Mean and standard deviation May detect intruders,who are likely to use different commands.or a successful penetration by a legitimate user, who has gained access to privileged commands. Program resource utilization Mean and standard deviation An abnormal value might suggest injection of a virus or Trojan horse,which performs side-effects that increase I/O or processor utilization. Execution denials Operational model May detect penetration attempt by individual user who seeks higher privileges. File access activity Read,write,create,delete Mean and standard deviation Abnormalities for read and frequency write access for individual users may signify masquerading or browsing. Records read,written Mean and standard deviation Abnormality could signify an attempt to obtain sensitive data by inference and aggregation. Failure count for read,write, Operational May detect users who 2022/10/9 create.delete persistently attempt to access 15/48 unauthorized files
2022/10/9 现代密码学理论与实践-18 入侵者 15/48

海拳不 常用监测入侵手段 1950 ·按天记录登录的频率和次数 ·记录在不同地点登录的频率 ·距离上次登录的时间 ·登录时口令失败次数 。程序执行频繁程度 ● 程序拒绝执行次数 ●j 读、写、创建、删除频度 ·读、写、创建、删除失败次数 2022/10/9 现代密码学理论与实践-18入侵者 16/48
2022/10/9 现代密码学理论与实践-18 入侵者 16/48 常用监测入侵手段 ⚫ 按天记录登录的频率和次数 ⚫ 记录在不同地点登录的频率 ⚫ 距离上次登录的时间 ⚫ 登录时口令失败次数 ⚫ 程序执行频繁程度 ⚫ 程序拒绝执行次数 ⚫ 读、写、创建、删除频度 ⚫ 读、写、创建、删除失败次数