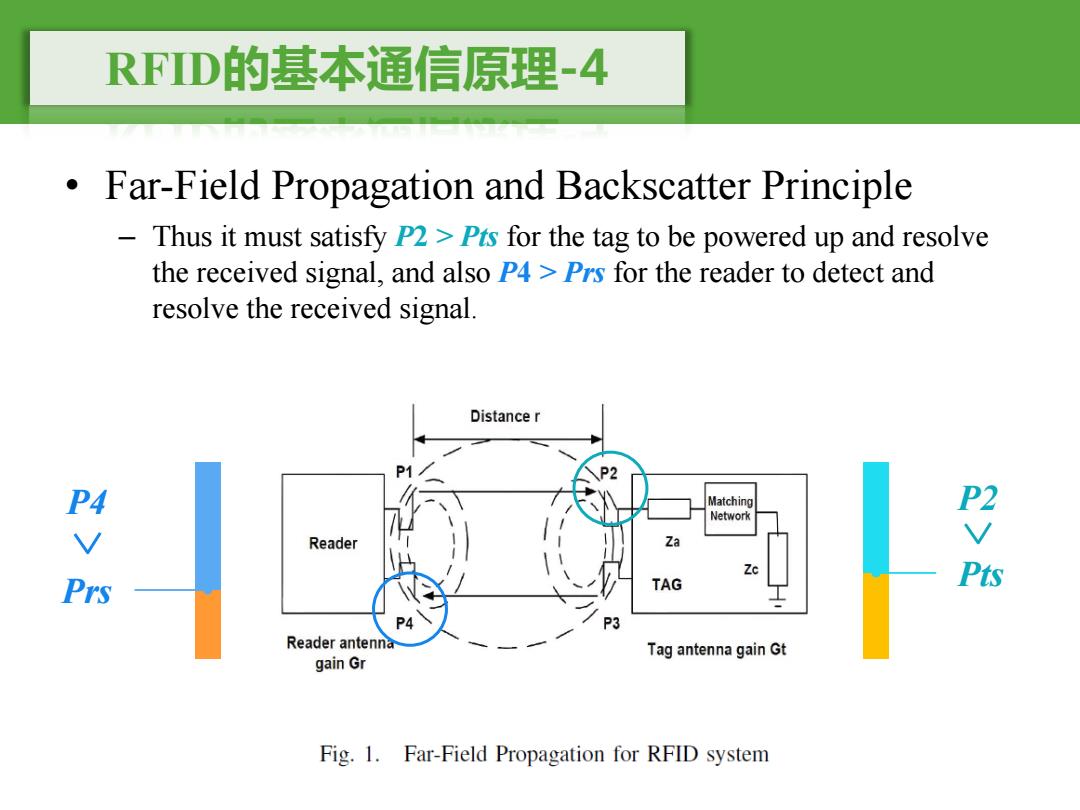
RFD的基本通信原理-4 Far-Field Propagation and Backscatter Principle Thus it must satisfy P2>Pts for the tag to be powered up and resolve the received signal,and also P4 Prs for the reader to detect and resolve the received signal. Distance r P2 Matching Network Reader Za 四V胶 TAG Reader antenna Tag antenna gain Gt gain Gr Fig.1.Far-Field Propagation for RFID system
RFID的基本通信原理-4 • Far-Field Propagation and Backscatter Principle – Thus it must satisfy P2 > Pts for the tag to be powered up and resolve the received signal, and also P4 > Prs for the reader to detect and resolve the received signal. Pts Prs P4 P2

基于时隙ALOHA的标签识别机制-1 Tag inventory and access Interrogator cw Select CW Query cw Ack Cw QueryRep CW NAK Cw Tag PC+EPC RN16 +CRC16 Interrogator cw Query Cw QueryRep CW QueryRep Cw QueryRep CW INo ReplyI Collision Detected Single Reply Tag RN16 RN16 Fig.2.C1G2 protocol
基于时隙ALOHA的标签识别机制-1 • Tag inventory and access

基于时隙ALOHA的标签识别机制-2 Tag inventory and access The MAC protocol for the C1G2 system is based on Slotted ALOHA, where each frame has a number of slots and each active tag will reply in a randomly selected slot per frame. When a reader(interrogator)wishes to read a set of tags,it first powers up and transmits a continuous wave(CW)to energize the tags.It then initiates a series of frames,varying the number of slots in each frame to best accommodate the number of tags.After all tags are read,the reader powers down.We refer to an individual frame as a Query Round,and the series of Query Rounds between power down periods as a Query Cycle. Query Cycle Query Round Query Round cee0。 Query Round
基于时隙ALOHA的标签识别机制-2 • Tag inventory and access – The MAC protocol for the C1G2 system is based on Slotted ALOHA, where each frame has a number of slots and each active tag will reply in a randomly selected slot per frame. – When a reader (interrogator) wishes to read a set of tags, it first powers up and transmits a continuous wave (CW) to energize the tags. It then initiates a series of frames, varying the number of slots in each frame to best accommodate the number of tags. After all tags are read, the reader powers down. We refer to an individual frame as a Query Round, and the series of Query Rounds between power down periods as a Query Cycle. Query Round Query Round …… Query Round Query Cycle
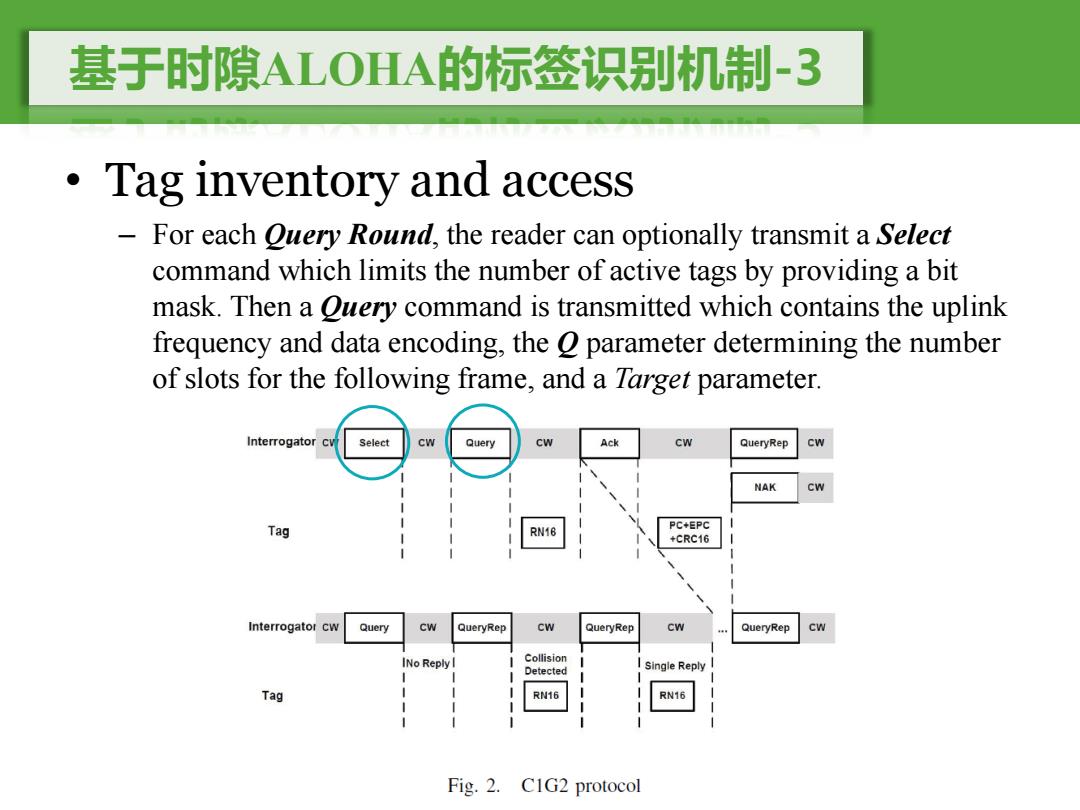
基于时隙ALOHA的标签识别机制-3 Tag inventory and access - For each Query Round,the reader can optionally transmit a Select command which limits the number of active tags by providing a bit mask.Then a Ouery command is transmitted which contains the uplink frequency and data encoding,the o parameter determining the number of slots for the following frame,and a Target parameter. Interrogator Select cw Query cw Ack Cw QueryRep Cw NAK Cw Tag RN16 PC+EPC +CRC16 Interrogator Query CW QueryRep Cw QueryRep Cw QueryRep INo Reply I Collision Detected Single Reply Tag RN16 Fig.2.C1G2 protocol
基于时隙ALOHA的标签识别机制-3 • Tag inventory and access – For each Query Round, the reader can optionally transmit a Select command which limits the number of active tags by providing a bit mask. Then a Query command is transmitted which contains the uplink frequency and data encoding, the Q parameter determining the number of slots for the following frame, and a Target parameter
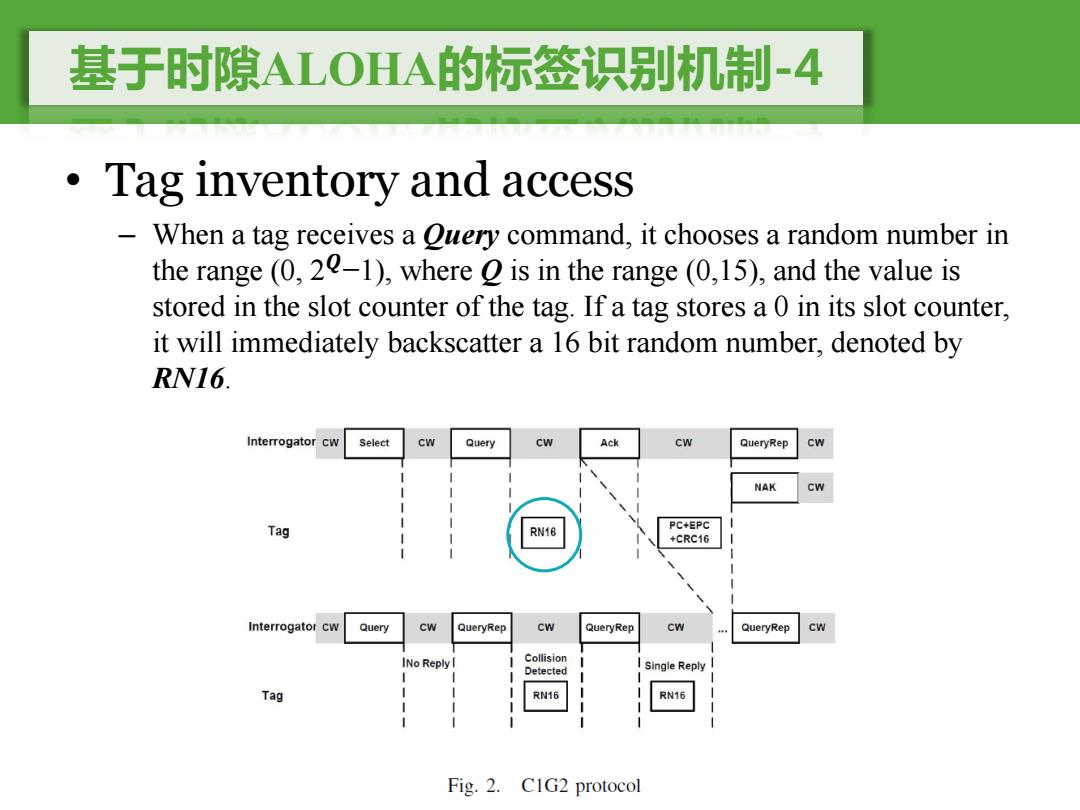
基于时隙ALOHA的标签识别机制-4 Tag inventory and access 一 When a tag receives a Ouery command,it chooses a random number in the range (0,20-1),where is in the range (0,15),and the value is stored in the slot counter of the tag.If a tag stores a 0 in its slot counter, it will immediately backscatter a 16 bit random number,denoted by RN16. Interrogator Cw Select Cw Query cw Ack Cw QueryRep Cw NAK CW Tag RN16 PC+EPC +CRC16 Interrogator Cw Query CW QueryRep Cw QueryRep Cw QueryRep INo Reply I Collision Detected Single Reply Tag RN16 Fig.2.C1G2 protocol
基于时隙ALOHA的标签识别机制-4 • Tag inventory and access – When a tag receives a Query command, it chooses a random number in the range (0, 2�−1), where Q is in the range (0,15), and the value is stored in the slot counter of the tag. If a tag stores a 0 in its slot counter, it will immediately backscatter a 16 bit random number, denoted by RN16