
Advance in Intrusion Detection Techniques Associate Prof.Fang Xianjin(方贤进) Computer Science Engineering SchoolofAUST
Advance in Intrusion Detection Techniques Associate Prof. Fang Xianjin(方贤进) Computer Science & Engineering School of AUST

Outline Context of computer security problem ● Brief summaries of computer security system What is IDS? Architecture and Classification of IDS Intrusion detection techniques My current research works Questions and answer
Outline ⚫ Context of computer security problem ⚫ Brief summaries of computer security system ⚫ What is IDS? ⚫ Architecture and Classification of IDS ⚫ Intrusion detection techniques ⚫ My current research works ⚫ Questions and answer
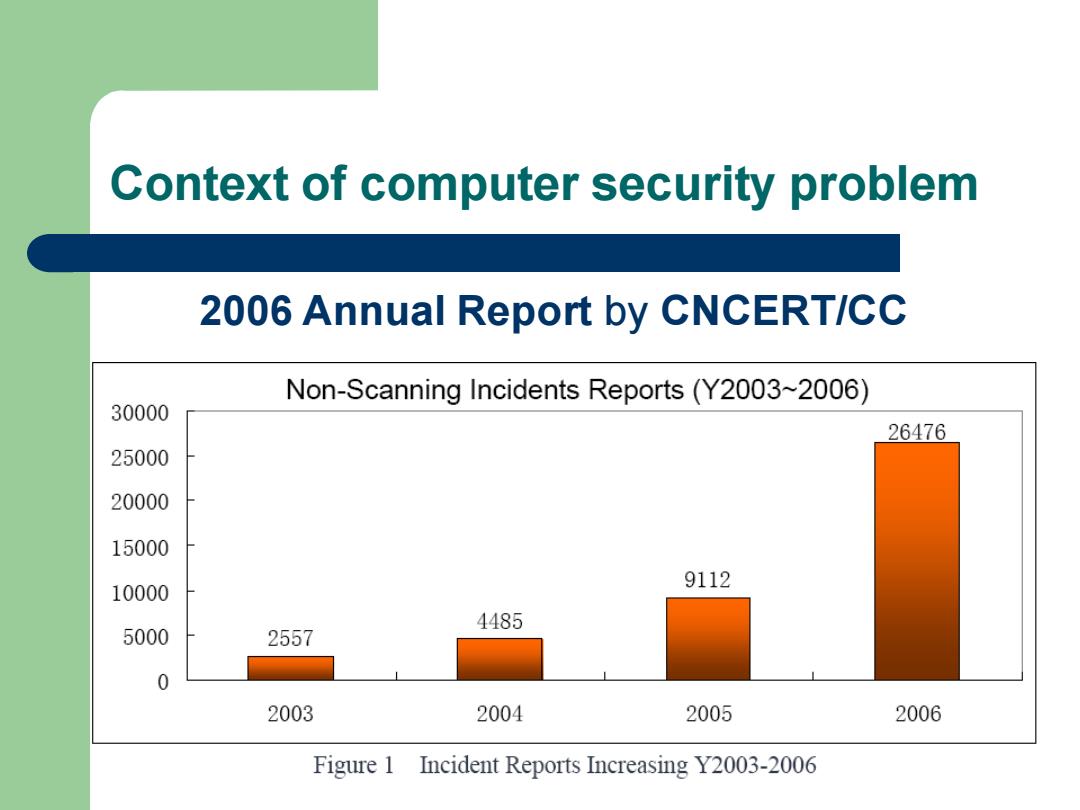
Context of computer security problem 2006 Annual Report by CNCERT/CC Non-Scanning Incidents Reports(Y2003~2006) 30000 26476 25000 20000 15000 10000 9112 4485 5000 2557 0 2003 2004 2005 2006 Figure 1 Incident Reports Increasing Y2003-2006
Context of computer security problem 2006 Annual Report by CNCERT/CC
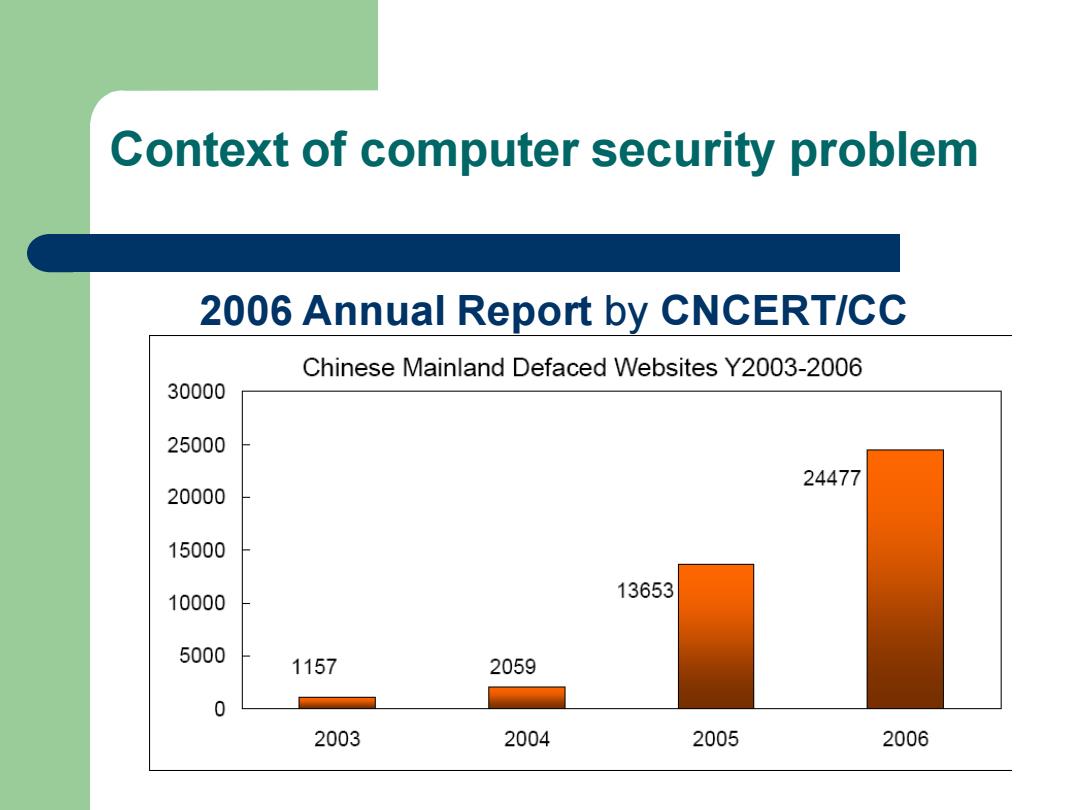
Context of computer security problem 2006 Annual Report by CNCERT/CC Chinese Mainland Defaced Websites Y2003-2006 30000 25000 24477 20000 15000 10000 13653 5000 1157 2059 0 2003 2004 2005 2006
Context of computer security problem 2006 Annual Report by CNCERT/CC
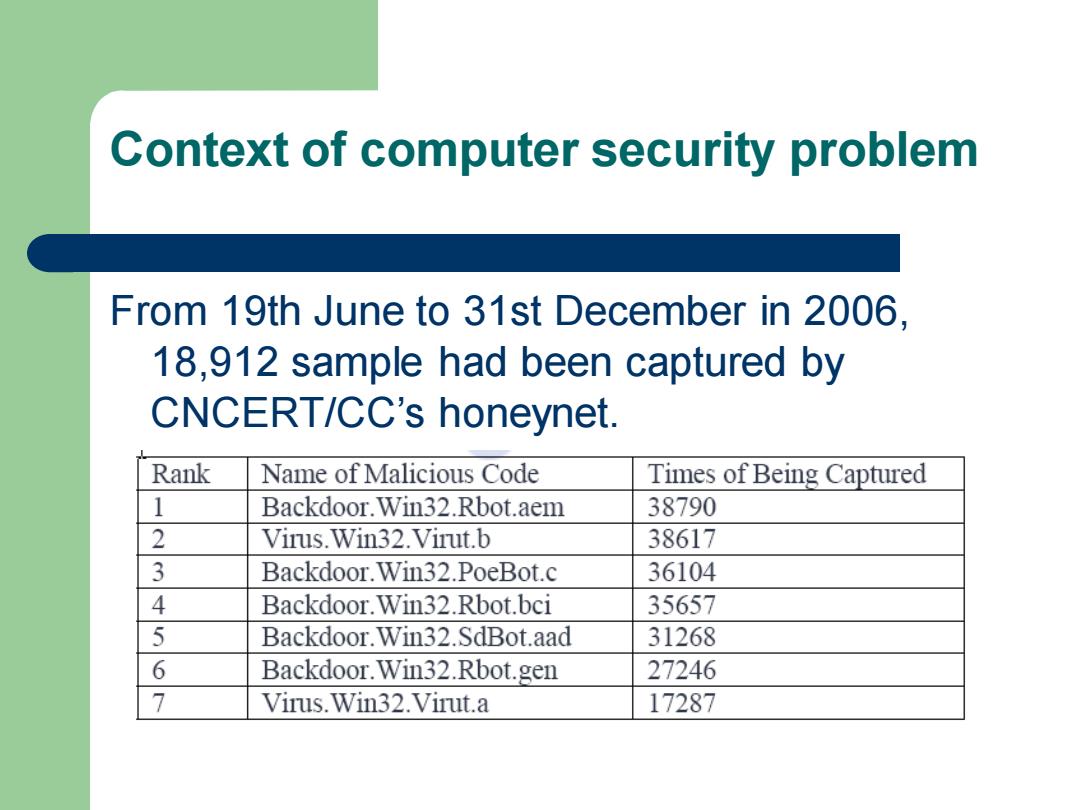
Context of computer security problem From 19th June to 31st December in 2006. 18,912 sample had been captured by CNCERT/CC's honeynet. Rank Name of Malicious Code Times of Being Captured 1 Backdoor.Win32.Rbot.aem 38790 2 Virus.Win32.Virut.b 38617 3 Backdoor.Win32.PoeBot.c 36104 4 Backdoor.Win32.Rbot.bci 35657 5 Backdoor.Win32.SdBot.aad 31268 6 Backdoor.Win32.Rbot.gen 27246 Virus.Win32.Virut.a 17287
Context of computer security problem From 19th June to 31st December in 2006, 18,912 sample had been captured by CNCERT/CC’s honeynet