
Who might Bob,Alice be? .well,real-life Bobs and Alices! Web browser/server for electronic transactions (e.g.,on-line purchases) Oon-line banking client/server DNS servers routers exchanging routing table updates other examples? 8:Network Security 8-6
8: Network Security 8-6 Who might Bob, Alice be? . well, real-life Bobs and Alices! Web browser/server for electronic transactions (e.g., on-line purchases) on-line banking client/server DNS servers routers exchanging routing table updates other examples?

There are bad guys (and girls)out there! Q:What can a "bad guy"do? A:a lot! o eavesdrop:intercept messages o actively insert messages into connection o impersonation:can fake (spoof)source address in packet (or any field in packet) o hijacking:"take over"ongoing connection by removing sender or receiver,inserting himself in place o denial of service:prevent service from being used by others(e.g.,by overloading resources) more on this later. 8:Network Security 8-7
8: Network Security 8-7 There are bad guys (and girls) out there! Q: What can a “bad guy” do? A: a lot! eavesdrop: intercept messages actively insert messages into connection impersonation: can fake (spoof) source address in packet (or any field in packet) hijacking: “take over” ongoing connection by removing sender or receiver, inserting himself in place denial of service: prevent service from being used by others (e.g., by overloading resources) more on this later

Chapter 8 roadmap 8.1 What is network security? 8.2 Principles of cryptography 8.3 Authentication 8.4 Integrity 8.5 Key Distribution and certification 8.6 Access control:firewalls 8.7 Attacks and counter measures 8.8 Security in many layers 8:Network Security 8-8
8: Network Security 8-8 Chapter 8 roadmap 8.1 What is network security? 8.2 Principles of cryptography 8.3 Authentication 8.4 Integrity 8.5 Key Distribution and certification 8.6 Access control: firewalls 8.7 Attacks and counter measures 8.8 Security in many layers
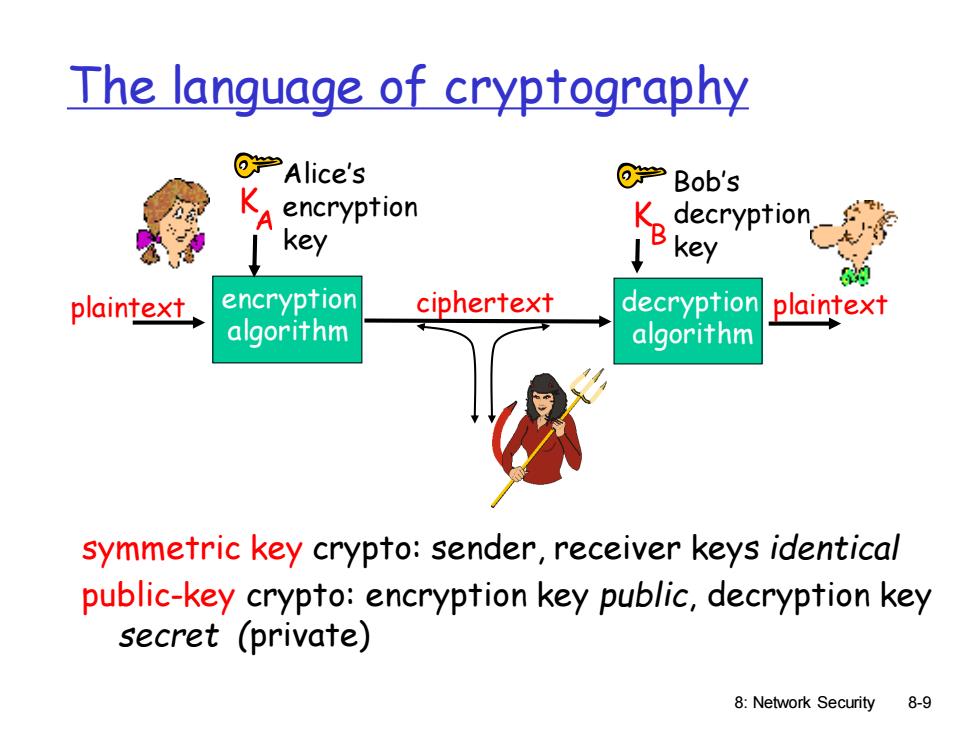
The language of cryptography ⑥学Alice's ⑥学Bob's encryption K decryption key B key plaintext encryption ciphertext decryption plaintext algorithm algorithm symmetric key crypto:sender,receiver keys identical public-key crypto:encryption key public,decryption key secret (private) 8:Network Security 8-9
8: Network Security 8-9 The language of cryptography symmetric key crypto: sender, receiver keys identical public-key crypto: encryption key public, decryption key secret (private) plaintext ciphertext plaintext K A encryption algorithm decryption algorithm Alice’s encryption key Bob’s decryption key K B
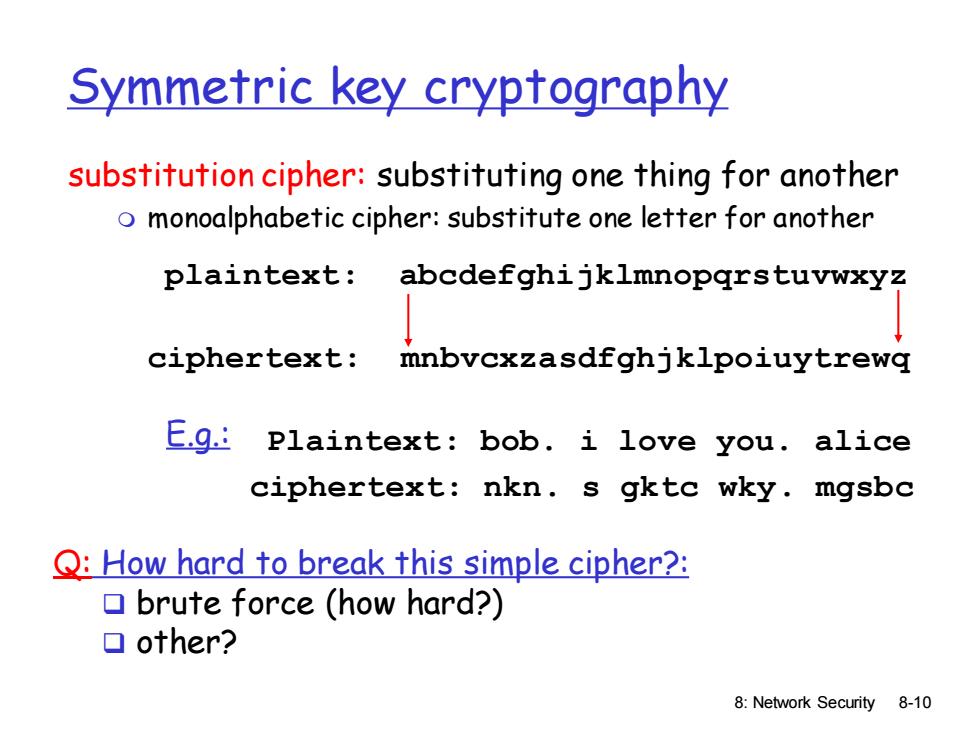
Symmetric key cryptography substitution cipher:substituting one thing for another o monoalphabetic cipher:substitute one letter for another plaintext:abcdefghijklmnopqrstuvwxyz ciphertext:mnbvcxzasdfghjklpoiuytrewq E.g.:plaintext:bob.i love you.alice ciphertext:nkn.s gktc wky.mgsbc Q:How hard to break this simple cipher?: brute force (how hard?) ▣other? 8:Network Security 8-10
8: Network Security 8-10 Symmetric key cryptography substitution cipher: substituting one thing for another monoalphabetic cipher: substitute one letter for another plaintext: abcdefghijklmnopqrstuvwxyz ciphertext: mnbvcxzasdfghjklpoiuytrewq Plaintext: bob. i love you. alice ciphertext: nkn. s gktc wky. mgsbc E.g.: Q: How hard to break this simple cipher?: ❑ brute force (how hard?) ❑ other?