
Source A Destination B M M K K Compare (a)Message authentication Ck(M) M M K Compare K2 EK2[M I CK (M)] CK;(M) (b)Message authentication and confidentiality;authentication tied to plaintext E2[M] M E M K K Compare K2 K CK [EK,(M)] (c)Message authentication and confidentiality:authentication tied to ciphertext Figure 11.4 Basic Uses of Message Authentication Code(MAC)
2022/10/9 现代密码学理论与实践-11 12/34
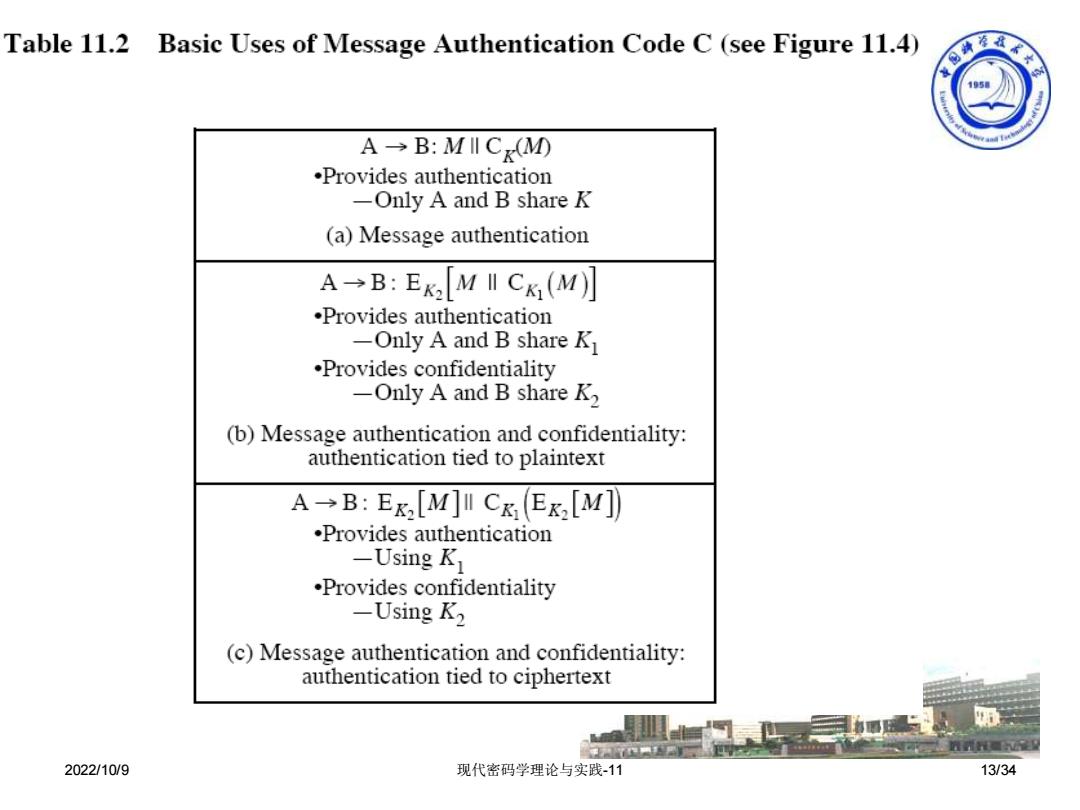
Table 11.2 Basic Uses of Message Authentication Code C (see Figure 11.4) 105 A→B:MICx(M0 .Provides authentication -Only A and B share K (a)Message authentication A→B:Ek[MICK(M] .Provides authentication -Only A and B share K .Provides confidentiality -Only A and B share K2 (b)Message authentication and confidentiality: authentication tied to plaintext A→B:E,[M]IC&(Ex,[M] .Provides authentication -Using K .Provides confidentiality -Using K2 (c)Message authentication and confidentiality: authentication tied to ciphertext 道道量 2022/10/9 现代密码学理论与实践-11 13/34
2022/10/9 现代密码学理论与实践-11 13/34