
Section 16.5.Combining Security Associations 503 Section 16.6.Key Management Section 16.7.Recommended Reading and Web Site Section 16.8.Key Terms,Review Questions,and Problems 51亚 Appendix 16A Internetworking and Internet Protocols 8 Chapter 17.Web Security 52 Section 17.1.Web Security Considerations Section 17.2.Secure Socket Layer and Transport Layer Security Section 17.3.Secure Electronic Transaction 549 Section 17.4.Recommended Reading and Web Sites 560 Section 17.5.Key Terms,Review Questions,and Problems Part Four:System Security Chapter 18.Intruders Section 18.1.Intruders Section 18.2.Intrusion Detection Section 18.3.Password Management Section 18.4.Recommended Reading and Web Sites Section 18.5.Key Terms.Review Questions,and Problems Appendix 18A The Base-Rate Fallacy Chapter 19.Malicious Software Section 19.1.Viruses and Related Threats Section 19.2.Virus Countermeasures 第10 Section 19.3.Distributed Denial of Service Attacks Section 19.4.Recommended Reading and Web Sites Section 19.5.Key Terms,Review Questions,and Problems 102 Chapter 20.Firewalls Section 20.1.Firewall Design Principles Section 20.2.Trusted Systems Section 20.3.Common Criteria for Information Technology Security Evaluation Section 20.4.Recommended Reading and Web Sites Section 20.5.Key Terms.Review Questions.and Problems Appendix A.Standards and Standards-Setting Organizations Section A.1.The Importance of Standards Section A.2.Internet Standards and the Internet Society Section A.3.National Institute of Standards and Technology Appendix B.Projects for Teaching Cryptography and Network Security Section B.1.Research Projects 54 Section B.2.Programming Projects 6 Section B.3.Laboratory Exercises Section B.4.Writing Assignments Section B.5.Reading/Report Assignments Glossary 657 References 663 Abbreviations 663 Inside Front Cover InsideFrontCover Inside Back Cover InsideBackCover Index ◆PREY NEXT◆
Section 16.5. Combining Security Associations 503 Section 16.6. Key Management 506 Section 16.7. Recommended Reading and Web Site 516 Section 16.8. Key Terms, Review Questions, and Problems 517 Appendix 16A Internetworking and Internet Protocols 518 Chapter 17. Web Security 527 Section 17.1. Web Security Considerations 528 Section 17.2. Secure Socket Layer and Transport Layer Security 531 Section 17.3. Secure Electronic Transaction 549 Section 17.4. Recommended Reading and Web Sites 560 Section 17.5. Key Terms, Review Questions, and Problems 561 Part Four: System Security 563 Chapter 18. Intruders 565 Section 18.1. Intruders 567 Section 18.2. Intrusion Detection 570 Section 18.3. Password Management 582 Section 18.4. Recommended Reading and Web Sites 591 Section 18.5. Key Terms, Review Questions, and Problems 592 Appendix 18A The Base-Rate Fallacy 594 Chapter 19. Malicious Software 598 Section 19.1. Viruses and Related Threats 599 Section 19.2. Virus Countermeasures 610 Section 19.3. Distributed Denial of Service Attacks 614 Section 19.4. Recommended Reading and Web Sites 619 Section 19.5. Key Terms, Review Questions, and Problems 620 Chapter 20. Firewalls 621 Section 20.1. Firewall Design Principles 622 Section 20.2. Trusted Systems 634 Section 20.3. Common Criteria for Information Technology Security Evaluation 640 Section 20.4. Recommended Reading and Web Sites 644 Section 20.5. Key Terms, Review Questions, and Problems 645 Appendix A. Standards and Standards-Setting Organizations 647 Section A.1. The Importance of Standards 648 Section A.2. Internet Standards and the Internet Society 649 Section A.3. National Institute of Standards and Technology 652 Appendix B. Projects for Teaching Cryptography and Network Security 653 Section B.1. Research Projects 654 Section B.2. Programming Projects 655 Section B.3. Laboratory Exercises 655 Section B.4. Writing Assignments 655 Section B.5. Reading/Report Assignments 656 Glossary 657 References 663 Abbreviations 663 Inside Front Cover InsideFrontCover Inside Back Cover InsideBackCover Index
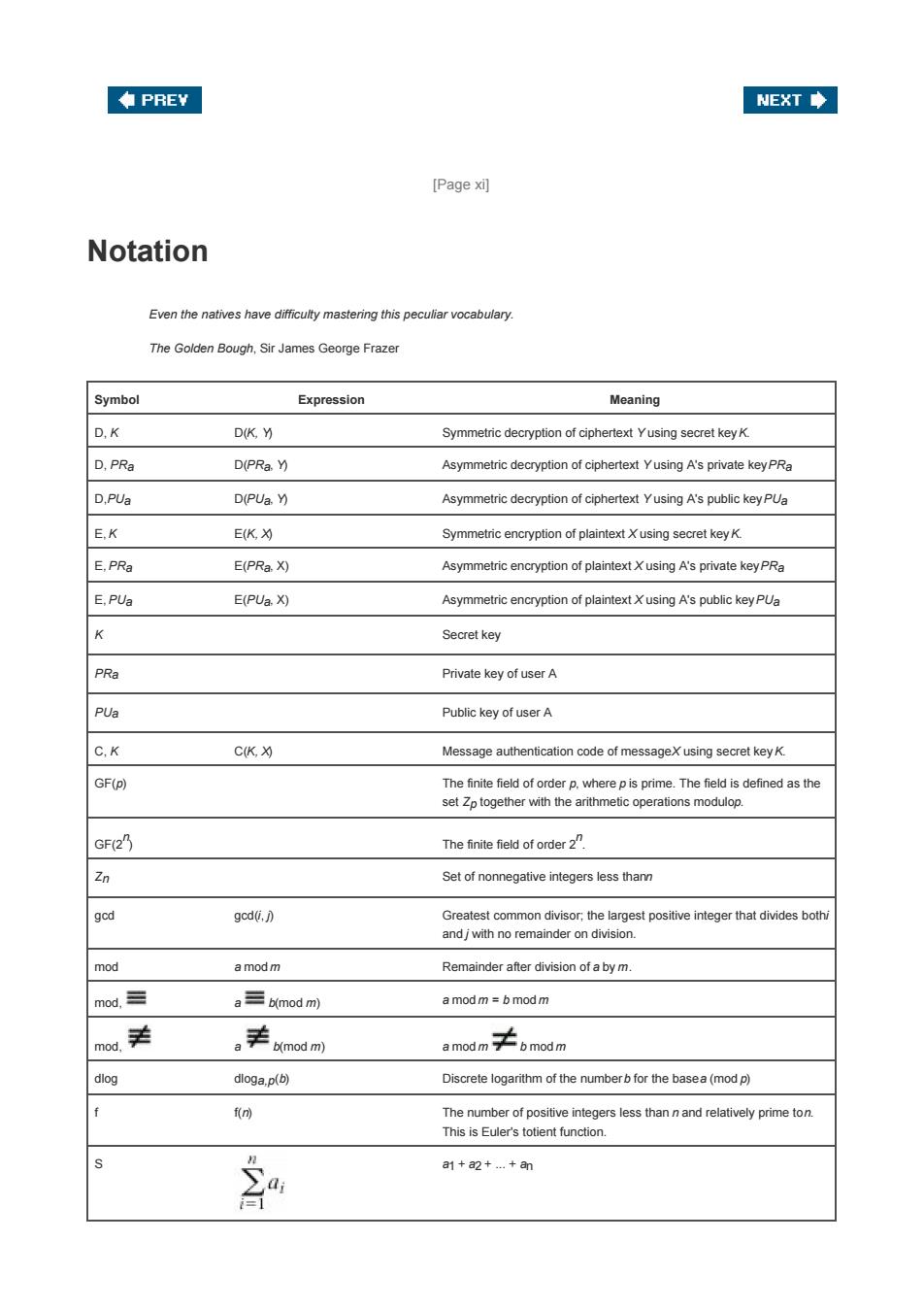
◆PREY NEXT◆ [Page x刈 Notation Even the natives have difficulty mastering this peculiar vocabulary. The Golden Bough,Sir James George Frazer Symbol Expression Meaning D,K D(K,Y) Symmetric decryption of ciphertext Yusing secret key K. D,PRa D(PRa.Y) Asymmetric decryption of ciphertext Yusing A's private key PRa D,PUa D(PUa.Y) Asymmetric decryption of ciphertext Yusing A's public key PUa E,K E(K,9 Symmetric encryption of plaintext X using secret key K. E.PRa E(PRa.X) Asymmetric encryption of plaintext X using A's private key PRa E,PUa E(PUa.X) Asymmetric encryption of plaintext X using A's public key PUa K Secret key PRa Private key of user A PUa Public key of user A C.K C(K,X) Message authentication code of messageX using secret key K. GF(p) The finite field of order p.where p is prime.The field is defined as the set Zp together with the arithmetic operations modulop. GF(2 The finite field of order2 Zn Set of nonnegative integers less thann gcd gcd〔,) Greatest common divisor;the largest positive integer that divides bothi and jwith no remainder on division. mod amodm Remainder after division of a by m. mod,≡ a三b(mod m) a mod m b mod m mog美 ,丰kmo8m a mod m≠6mdnm dlog dloga.p(b) Discrete logarithm of the numberb for the basea(mod p) f f The number of positive integers less than n and relatively prime ton. This is Euler's totient function. 和 a1+a2+.+an
[Page xi] Notation Even the natives have difficulty mastering this peculiar vocabulary. The Golden Bough, Sir James George Frazer Symbol Expression Meaning D, K D(K, Y) Symmetric decryption of ciphertext Y using secret key K. D, PRa D(PRa, Y) Asymmetric decryption of ciphertext Y using A's private key PRa D,PUa D(PUa, Y) Asymmetric decryption of ciphertext Y using A's public key PUa E, K E(K, X) Symmetric encryption of plaintext X using secret key K. E, PRa E(PRa, X) Asymmetric encryption of plaintext X using A's private key PRa E, PUa E(PUa, X) Asymmetric encryption of plaintext X using A's public key PUa K Secret key PRa Private key of user A PUa Public key of user A C, K C(K, X) Message authentication code of message X using secret key K. GF(p) The finite field of order p, where p is prime. The field is defined as the set Zp together with the arithmetic operations modulo p. GF(2 n ) The finite field of order 2 n . Zn Set of nonnegative integers less than n gcd gcd(i, j) Greatest common divisor; the largest positive integer that divides both i and j with no remainder on division. mod a mod m Remainder after division of a by m. mod, a b(mod m) a mod m = b mod m mod, a b(mod m) a mod m b mod m dlog dloga,p(b) Discrete logarithm of the number b for the base a (mod p) f f(n) The number of positive integers less than n and relatively prime to n. This is Euler's totient function. S a1 + a2 + ... + an

Symbol Expression Meaning Π a1 x a2x ..x an a =1 v i divides j,which means that there is no remainder wheny is divided byi 间 Absolute value of a X x concatenated with y 之 ≈, x is approximately equal toy ⊕ ⊕, Exclusive-OR of x and y for single-bit variables;Bitwise exclusive-OR of x and y for multiple-bit variables J L The largest integer less than or equal tox xEs The elementx is contained in the set S. ←→ A←→(a1,a2,…a The integer A corresponds to the sequence of integers e1,a2....,ak) 中PREY NEXT◆
Symbol Expression Meaning a1 x a2 x ... x an | i|j i divides j, which means that there is no remainder when j is divided by i |,| |a| Absolute value of a || x||y x concatenated with y x y x is approximately equal to y x y Exclusive-OR of x and y for single-bit variables; Bitwise exclusive-OR of x and y for multiple-bit variables , x The largest integer less than or equal to x x S The element x is contained in the set S. A (a1,a2, ...,ak) The integer A corresponds to the sequence of integers (a1,a2, ...,ak)
◆PREY NEXT◆ [Page xii] Preface "The tie,if I might suggest it.sir,a shade more tightly knotted.One aims at the perfect butterfly effect.If you will permit me" "What does it matter,Jeeves,at a time like this?Do you realize that Mr.Little's domestic happiness is hanging in the scale?" "There is no time.sir,at which ties do not matter." Very Good,Jeeves!P.G.Wodehouse In this age of universal electronic connectivity.of viruses and hackers,of electronic eavesdropping and electronic fraud,there is indeed no time at which security does not matter.Two trends have come together to make the topic of this book of vital interest.First,the explosive growth in computer systems and their interconnections via networks has increased the dependence of both organizations and individuals on the information stored and communicated using these systems.This,in turn,has led to a heightened awareness of the need to protect data and resources from disclosure,to guarantee the authenticity of data and messages,and to protect systems from network-based attacks.Second,the disciplines of cryptography and network security have matured,leading to the development of practical,readily available applications to enforce network security. ◆PREY NEXT◆
[Page xiii] Preface "The tie, if I might suggest it, sir, a shade more tightly knotted. One aims at the perfect butterfly effect. If you will permit me" "What does it matter, Jeeves, at a time like this? Do you realize that Mr. Little's domestic happiness is hanging in the scale?" "There is no time, sir, at which ties do not matter." Very Good, Jeeves! P. G. Wodehouse In this age of universal electronic connectivity, of viruses and hackers, of electronic eavesdropping and electronic fraud, there is indeed no time at which security does not matter. Two trends have come together to make the topic of this book of vital interest. First, the explosive growth in computer systems and their interconnections via networks has increased the dependence of both organizations and individuals on the information stored and communicated using these systems. This, in turn, has led to a heightened awareness of the need to protect data and resources from disclosure, to guarantee the authenticity of data and messages, and to protect systems from network-based attacks. Second, the disciplines of cryptography and network security have matured, leading to the development of practical, readily available applications to enforce network security

◆PREY NEXT◆ [Page xii(continued)] Objectives It is the purpose of this book to provide a practical survey of both the principles and practice of cryptography and network security.In the first two parts of the book,the basic issues to be addressed by a network security capability are explored by providing a tutorial and survey of cryptography and network security technology.The latter part of the book deals with the practice of network security:practical applications that have been implemented and are in use to provide network security. The subject,and therefore this book,draws on a variety of disciplines.In particular,it is impossible to appreciate the significance of some of the techniques discussed in this book without a basic understanding of number theory and some results from probability theory. Nevertheless,an attempt has been made to make the book self-contained.The book presents not only the basic mathematical results that are needed but provides the reader with an intuitive understanding of those results.Such background material is introduced as needed.This approach helps to motivate the material that is introduced,and the author considers this preferable to simply presenting all of the mathematical material in a lump at the beginning of the book. ◆ ◆PREY NEXT◆
[Page xiii (continued)] Objectives It is the purpose of this book to provide a practical survey of both the principles and practice of cryptography and network security. In the first two parts of the book, the basic issues to be addressed by a network security capability are explored by providing a tutorial and survey of cryptography and network security technology. The latter part of the book deals with the practice of network security: practical applications that have been implemented and are in use to provide network security. The subject, and therefore this book, draws on a variety of disciplines. In particular, it is impossible to appreciate the significance of some of the techniques discussed in this book without a basic understanding of number theory and some results from probability theory. Nevertheless, an attempt has been made to make the book self-contained. The book presents not only the basic mathematical results that are needed but provides the reader with an intuitive understanding of those results. Such background material is introduced as needed. This approach helps to motivate the material that is introduced, and the author considers this preferable to simply presenting all of the mathematical material in a lump at the beginning of the book