
Some History ---一-- -一一--一一-0-一一- Developed from the field of theoretical immunology in the mid 1980's. ◆Suggested we‘might look'at the IS *1990-Bersini first use of immune algos to solve problems Forrest et al-Computer Security mid 1990's Hunt et al,mid 1990's-Machine learning
Some History Developed from the field of theoretical immunology in the mid 1980’s. Suggested we ‘might look’ at the IS 1990 – Bersini first use of immune algos to solve problems Forrest et al – Computer Security mid 1990’s Hunt et al, mid 1990’s – Machine learning
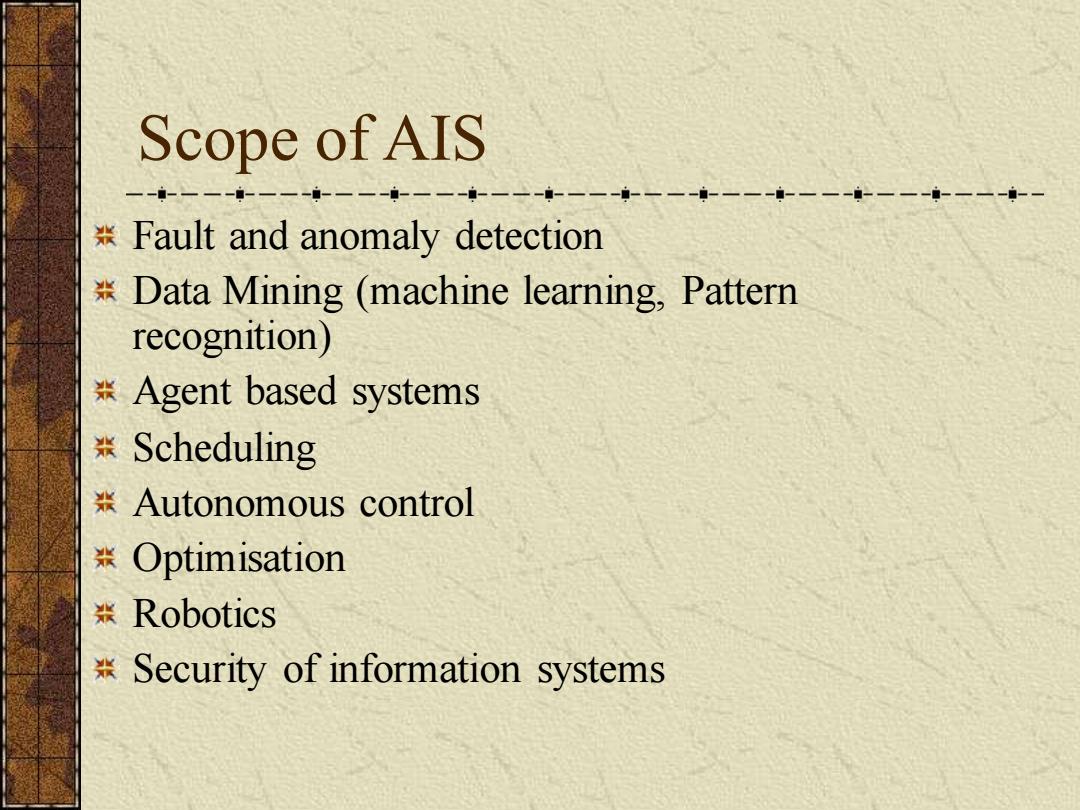
Scope ofAIS Fault and anomaly detection Data Mining (machine learning,Pattern recognition) 张Agent based systems 米 Scheduling 装Autonomous control 张Optimisation 装Robotics Security of information systems
Scope of AIS Fault and anomaly detection Data Mining (machine learning, Pattern recognition) Agent based systems Scheduling Autonomous control Optimisation Robotics Security of information systems

-一一--一--- -一一--一一-- Part I-Basic Immunology
Part I – Basic Immunology

Role of the Immune System ---一一-0-一一--一一--一一--一一--一一---一-- Protect our bodies from infection Primary immune response .Launch a response to invading pathogens Secondary immune response Remember past encounters Faster response the second time around
Role of the Immune System Protect our bodies from infection Primary immune response Launch a response to invading pathogens Secondary immune response Remember past encounters Faster response the second time around
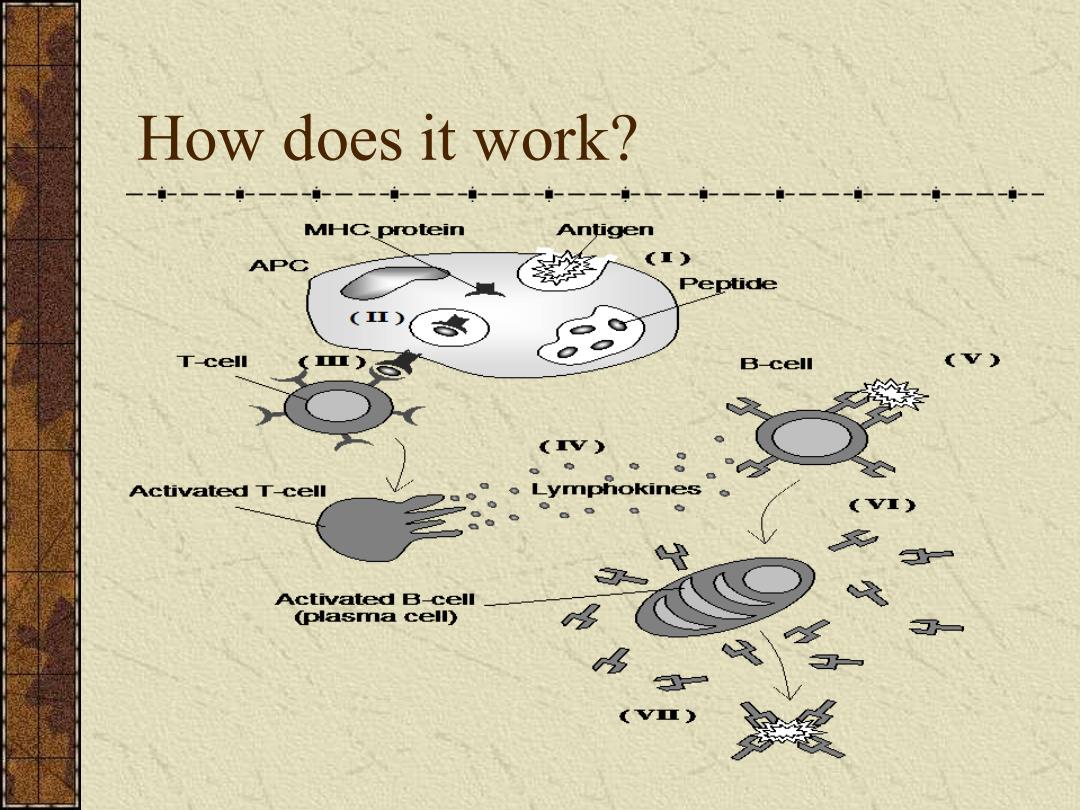
How does it work? ------一---一---一一-----------------一---一---一一-- MHC protein Antigen APC (夏) Peptide ()( 感 T-cell B-cell (v) Activated T-cell 。Lymphokines Activated B-cell (plasma cell) (vn)
How does it work?