
上游充通大¥ SHANGHAI JIAO TONG UNIVERSITY Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks Jinbei Zhang,Luoyifu,Xinbing Wang Department of Electronic Engineering Shanghai Jiao Tong University Aug.13,2013
Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks Jinbei Zhang, Luoyifu, Xinbing Wang Department of Electronic Engineering Shanghai Jiao Tong University Aug. 13, 2013

Outline 上浒充通大¥ SHANGHAI JIAO TONG UNIVERSITY ▣Introduction Motivations Related works >Objectives Q Network Modeland Definition QSecrecy Capacity for Independent Eavesdroppers QSecrecy Capacity for Colluding Eavesdroppers ▣Discussion Q Conclusion and Future Work Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 2
Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 2 Outline ❑ Introduction ➢ Motivations ➢ Related works ➢ Objectives ❑ Network Model and Definition ❑ Secrecy Capacity for Independent Eavesdroppers ❑ Secrecy Capacity for Colluding Eavesdroppers ❑ Discussion ❑ Conclusion and Future Work

Motivations 上浒充通大粤 SHANGHAI JIAO TONG UNIVERSITY Secrecy is a Major Concern in Wireless Networks. >Mobile Phone Wallet Military networks CARD HERE Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 3
3 Motivations ❑ Secrecy is a Major Concern in Wireless Networks. ➢ Mobile Phone Wallet ➢ Military networks ➢ … Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks
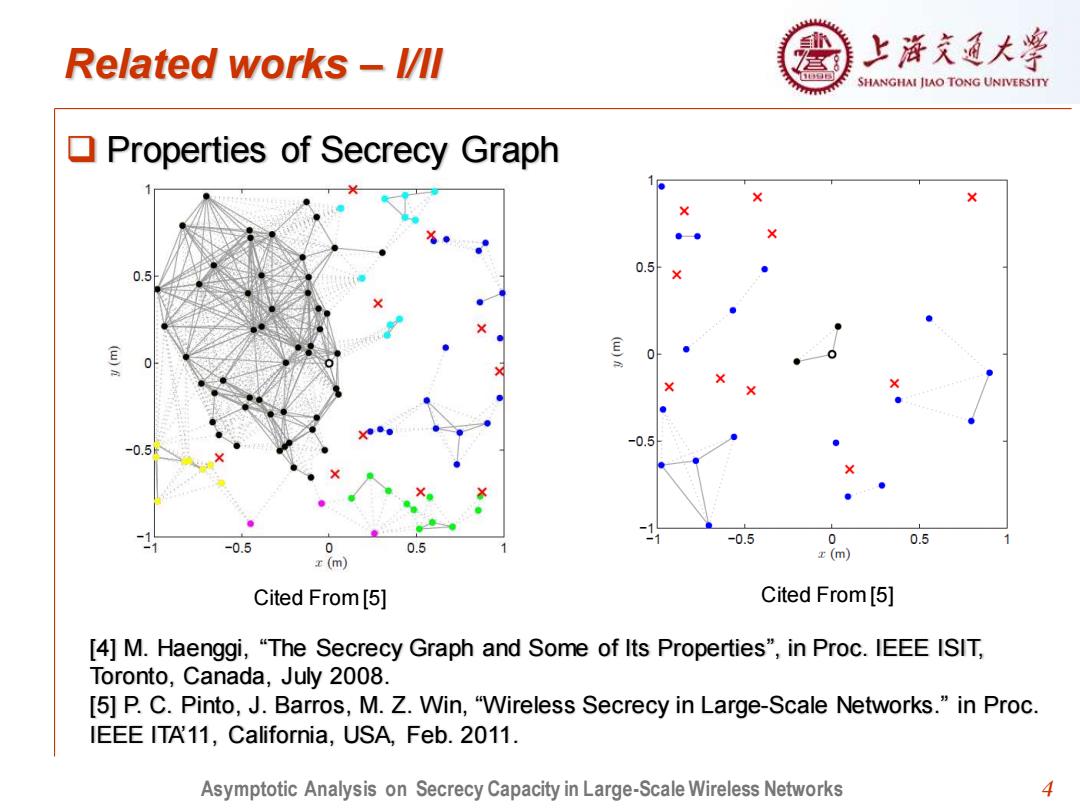
Related works l/ll 上浒充通大 SHANGHAI JIAO TONG UNIVERSITY Properties of Secrecy Graph + 0.5 ● 0.5 ● ● -0.5 -0.5 0 -0.5 0 0.5 -0.5 0.5 (m) z(m) Cited From [5] Cited From [5] [4]M.Haenggi,"The Secrecy Graph and Some of Its Properties",in Proc.IEEE ISIT, Toronto,Canada,July 2008. [5]P.C.Pinto,J.Barros,M.Z.Win,"Wireless Secrecy in Large-Scale Networks."in Proc. IEEE ITA11,California,USA,Feb.2011. Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 4
4 Related works – I/II ❑ Properties of Secrecy Graph [4] M. Haenggi, “The Secrecy Graph and Some of Its Properties”, in Proc. IEEE ISIT, Toronto, Canada, July 2008. [5] P. C. Pinto, J. Barros, M. Z. Win, “Wireless Secrecy in Large-Scale Networks.” in Proc. IEEE ITA’11, California, USA, Feb. 2011. Cited From [5] Cited From [5] Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks
Related works ll/lI 上浒充通大 SHANGHAI JIAO TONG UNIVERSITY Secrecy Capacity in large-scale networks, Mobile Networks [16] Guard Zone [13] Artificial Noise+Fading Gain(CSI needed)[12] Cited from [12] [16]Y.Liang,H.V.Poor and L.Ying,"Secrecy Throughput of MANETs under Passive and Active Attacks",in IEEE Trans.Inform.Theory,Vol.57,No.10,Oct.2011. [13]O.Koyluoglu,E.Koksal,E.Gammel,"On Secrecy Capacity Scaling in Wireless Networks",submitted to IEEE Trans.Inform.Theory,Apr.2010. [12]S.Vasudevan,D.Goeckel and D.Towsley,"Security-capacity Trade-off in Large Wireless Networks using Keyless Secrecy",in Proc.ACM MobiHoc,Chicago,Illinois,USA, Sept.2010. Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 5
5 Related works – II/II ❑ Secrecy Capacity in large-scale networks, ➢ Mobile Networks [16] ➢ Guard Zone [13] ➢ Artificial Noise+Fading Gain(CSI needed) [12] [16] Y. Liang, H. V. Poor and L. Ying, “Secrecy Throughput of MANETs under Passive and Active Attacks”, in IEEE Trans. Inform. Theory, Vol. 57, No. 10, Oct. 2011. [13] O. Koyluoglu, E. Koksal, E. Gammel, “On Secrecy Capacity Scaling in Wireless Networks”, submitted to IEEE Trans. Inform. Theory, Apr. 2010. [12] S. Vasudevan, D. Goeckel and D. Towsley, “Security-capacity Trade-off in Large Wireless Networks using Keyless Secrecy”, in Proc. ACM MobiHoc, Chicago, Illinois, USA, Sept. 2010. Cited from [12] Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks