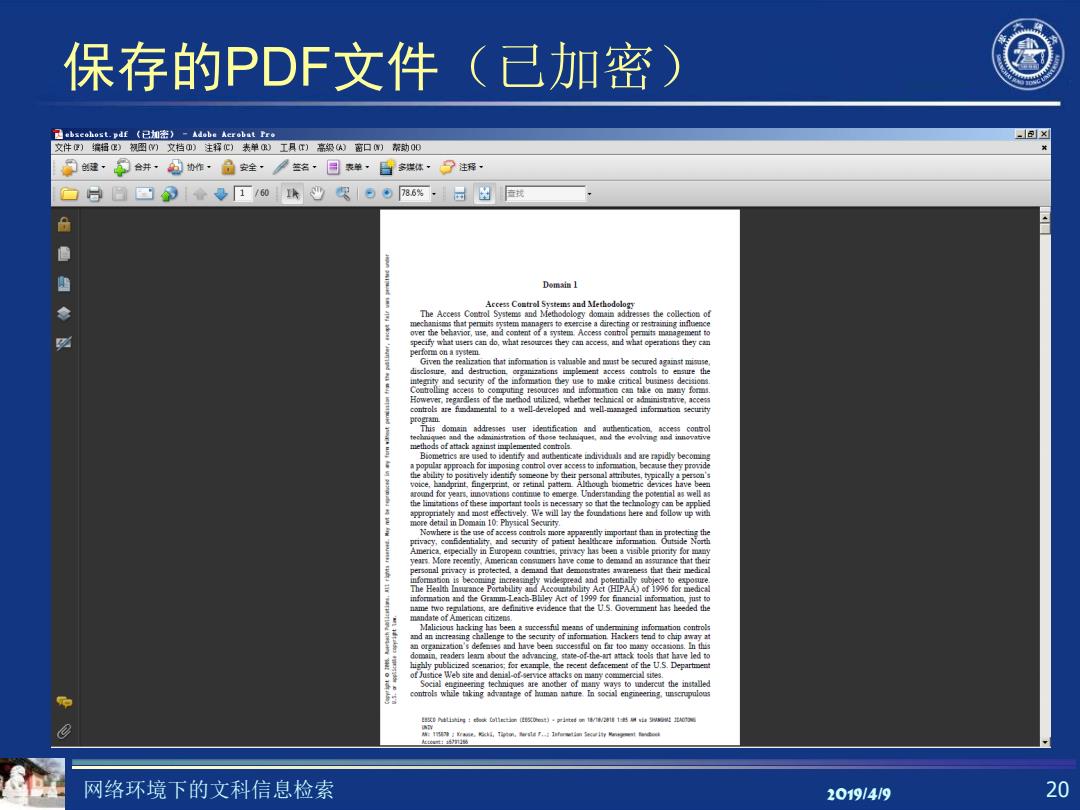
保存的PDF文件(己加密 ) 己bseohost.pdf《已如密)-Adobe Aerobat Pro 包 文件)编辑)初图们文档四)注择c)表单)工具T)高级)密口)黎助00 门的速·合并·的0作·局安全·名,日表单,日多体,了注将, 白日□》◆工10珠出图5。阳%·日凶我 Access Comtrol Systems and Methodology The Access Comtrol Systeme and Methodology domain addresses the collection of eatgorTetaiminginhgnce Access com p折些sc边db,what resources the与y can acces数md what operations they c2a perfom o如ayem Given the realization that information is valuable and mmst be secured against misuse. ing access to controls are fimdamental to a well-developed and well-manged information security program. the abil的yto positivel山yidenti的someone by the如personal attributes,typically a peron's voice,handprint,fingerprint,or retinal pattern.Although boometric devices have been rod for years.innovatics comtinue to emerge.Understanding the potential as well as the limitations of these imp ortant tools is neces or so that the techuo vely. Nowhere is the use of access controls more apparently important than in protecting the privacy,comfidentiality,and secuity of patiet healtheare information Outside North America.especially in European countries.privacy has been a visible priority for mamy years More recentiy,American commer have come to demand an asre that thei nd that information and the Gramm-Leach-Bhley Act of 1999 for financial infommation,just to name two regalations,are definitive evidence that the U.S.Goverment has heeded the mandate of American citizens. Malicions hacking has been get如 Hackers tendc可 organization's defemses and have been sccessful on far too occations.In this domain,readers leam about the advancing.state-of-the-ant attack tools that have led to highly publicized scenarios;for example the recent defacement of the U.S.Departient of Justice Web site and demial of service attacks on many commercial sites. Social engineering techniques are ays to uderet the installed 网络环境下的文科信息检索 20191419 20
网络环境下的文科信息检索 2019/4/9 20 保存的PDF文件(已加密)
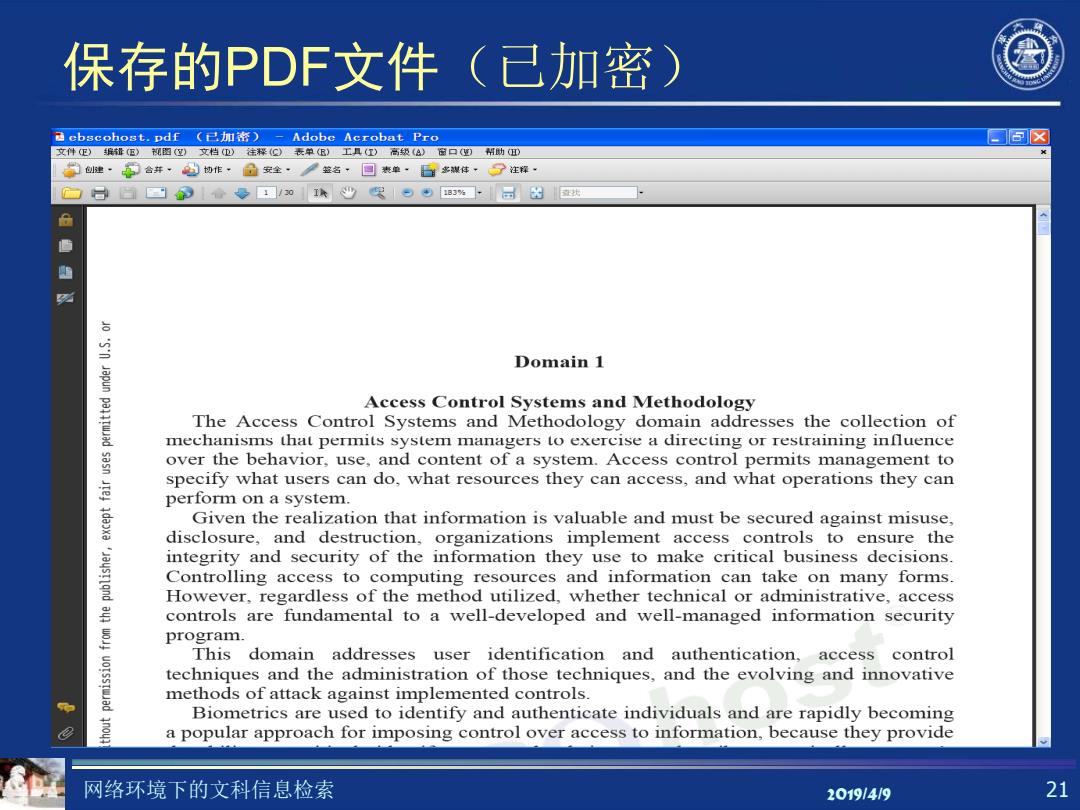
保存的PDF文件(已加密) ebscohost.pdf(已加帝)-Adobe Acrobat Pro ▣☒ 文件便)珉都E)视圈)文档(D往释(@)衣单B)工AD高级(a)图口)州助(D 创健·合并·码切作·局安全·接名·回表单·后多体,了注释· Domain 1 Japun paad Access Control Systems and Methodology The Access Control Systems and Methodology domain addresses the collection of mechanisms that permits system managers to exercise a directing or restraining influence 多 over the behavior,use,and content of a system.Access control permits management to specify what users can do,what resources they can access,and what operations they can perform on a system. Given the realization that information is valuable and must be secured against misuse, disclosure,and destruction,organizations implement access controls to ensure the Jaysrlqnd integrity and security of the information they use to make critical business decisions. Controlling access to computing resources and information can take on many forms However,regardless of the method utilized,whether technical or administrative,access 岩 controls are fundamental to a well-developed and well-managed information security program. This domain addresses user identification and authentication,access control techniques and the administration of those techniques,and the evolving and innovative methods of attack against implemented controls. Biometrics are used to identify and authenticate individuals and are rapidly becoming 10mc2 a popular approach for imposing control over access to information,because they provide 网络环境下的文科信息检索 201914/9 21
网络环境下的文科信息检索 2019/4/9 21 保存的PDF文件(已加密)

保存的PDF文件(已加密 Access Control Systems and Methodology.pdf ()Adobe Acrobat Pro ▣ 文件便)珉都E)视圈)文档(D)往释(@四衣单B)工A(D高级(8)窗口)州助(印 创健·合并,】协作·局安全·签名·回表单·多谋体,了注释· sasn Jrey idaoxa Domain 1 Access Control Systems and Methodology The Access Control Systems and Methodology domain addresses the collection of aysrlqnd mechanisms that permits system managers to exercise a directing or restraining influence over the behavior,use.arem.Access control permits management to specify what users can dc shirtcry can access,and what operations they can 器 perform on a system .0-4 Given the realization that information is valuable and must be secured against misuse, disclosure,and destruction,organizations implement access controls to ensure the integrity and security of the information they use to make critical business decisions. Controlling access to computing resources and information can take on many forms. However,regardless of the method utilized,whether technical or administrative,access controls are fundamental to a well-developed and well-managed information security program. This domain addresses user identification and authentication,access control 言 techniques and the administration of those techniques,and the evolving and innovative methods of attack against implemented controls. Biometrics are used to identify and authenticate individuals and are rapidly becoming a popular approach for imposing control over access to information,because they provide 网络环境下的文科信息检索 201914/9 22
网络环境下的文科信息检索 2019/4/9 22 保存的PDF文件(已加密)
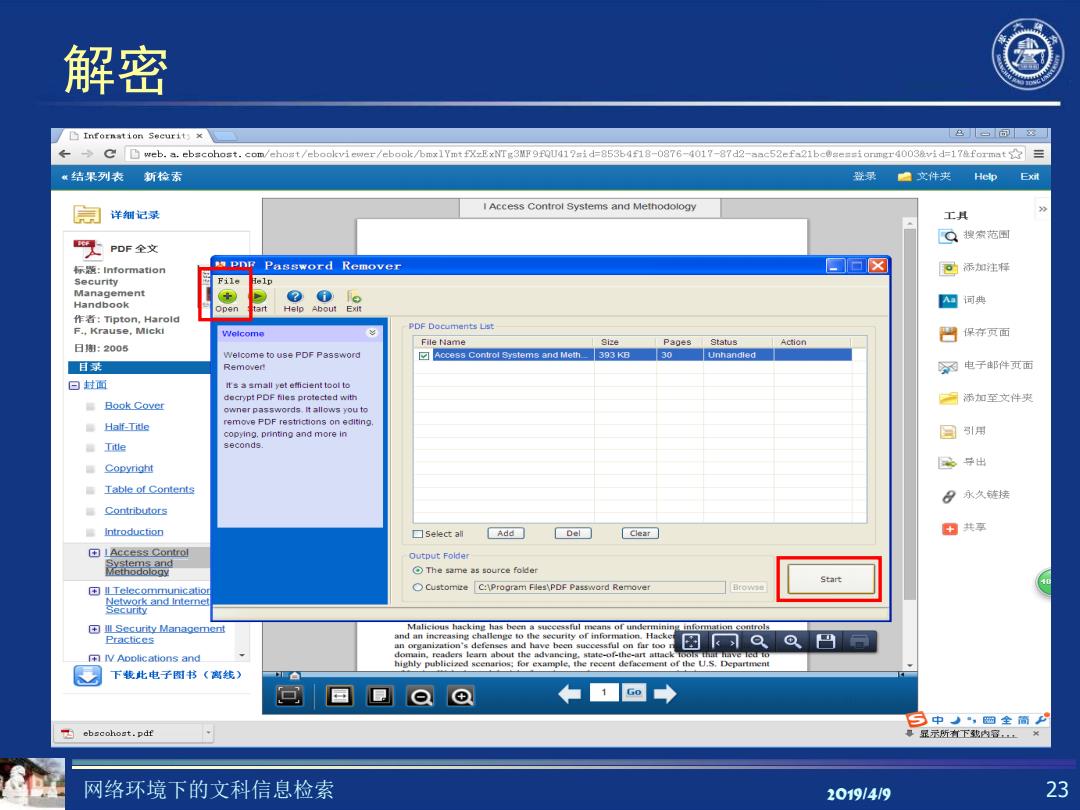
解密 ☐Infornation50Cur1t)× 一可 eweb.a.ebscohost.com/ehost/ebookcviewer/ebook/bmxlYmt fXzExNTg3MF9fQU41?sid=853b4f18-0876-4017-87d2-aac52efa21bc@sessionmgr40038vid=17&format 《结果列表 新检素 登录偏文件夹 Help Exit 寻 I Access Control Systems and Methodology 详细记录 工具 Q搜索范国 PDF全文 标题:Inform3uon pnr Password Remover 一▣☒ 可添加注释 Security File elp Management Handbook Open Help About Exit 词典 作者:Tipton,Harold F.,Krause,Micki PDF Documents List File Name Pages Status Action 智保存页面 日图:2005 Welcome to use PDF Password Access Control Systems and Meth 393K 30 ■目球 Remover! 剂电子邮件页面 回封面 It's a small yet efficient tool to decrypt PDF hles protected with 每 日ook Cover 添加至文件夹 owner passwords It allows you to Half-Title remove PDF restrictions on editing. copying.printing and more in 国引用 Iitle seconds. Copyright 居中出 Table of Contents 日永久链接 Contributors Introduction □Select al Add Del [clear] 中共享 田LAcces8 Contro Output Folder ⊙The same as source fok址e Start 雨Telecommunicatio Custome C:\Program Fles\PDF Password Remover and intem 田业Sec1 rity Manageme过 Practices and an in 图QQ巴同 highly publicized scenarios;for example,the recent defacement of the U.S.Department 下钱比电子图书(离线) 1@→ 中",画全商 ebscohost.pdf 显示所有下我容,× 网络环境下的文科信息检索 201914/9 23
网络环境下的文科信息检索 2019/4/9 23 解密
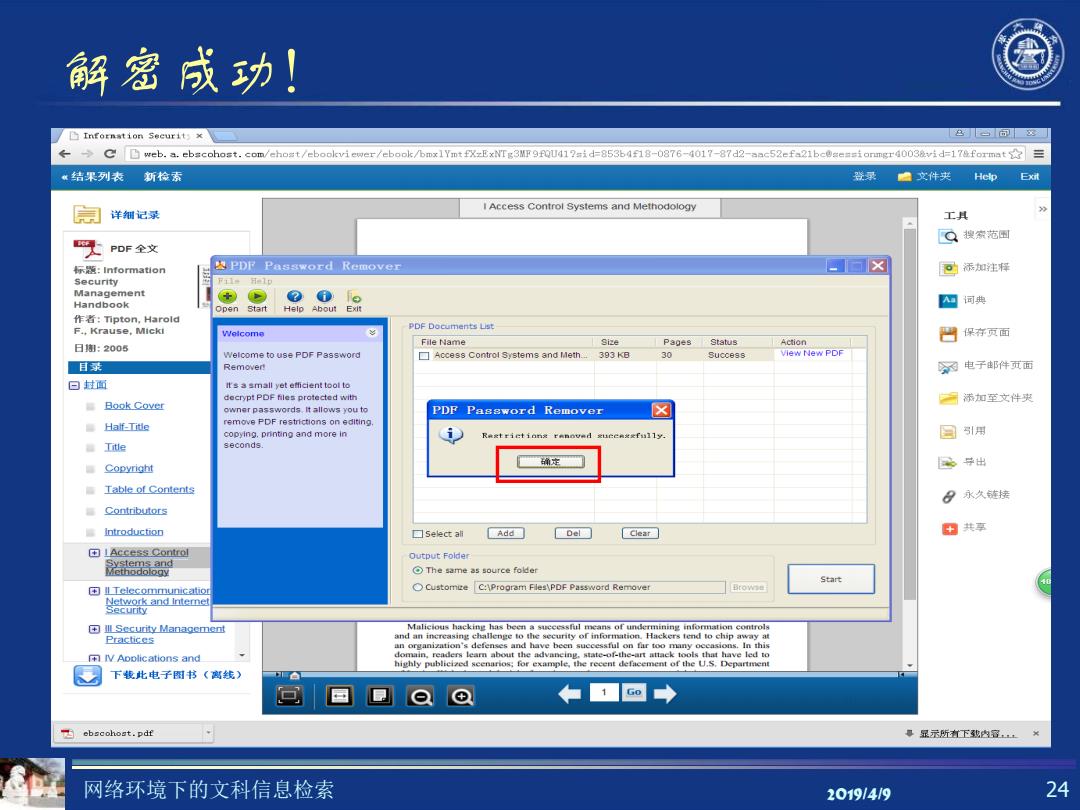
解密成功! ☐Infornat1 on Secur1t)× 一可 eweb.a.ebscohost.com/ehost/eboolcviewer/ebook/bmxlYmt fXzExNTg3MF9fQU41?sid=853b4f18-0876-4017-87d2-aac52efa21bc@sessionmgr40038vid=17&format 《结果列表 新检素 登录偏文件夹 Help Exit 寻 I Access Control Systems and Methodology 详细记录 工具 Q搜索范国 PDF全文 标题:Inform3uon PDF Password Remover 回X 可添加注释 Security 月1D Management Handbook Open Start Help About Exit 词典 作者:Tipton,Harold F.,Krause,Micki PDF Documents List 智保存页面 日图:2005 File Name Size Pages Status Action Welcome to use PDF Password Access Control Systems and Meth. 393KB 30 Success View New PDF 目菜 Remover! 了电子邮件页面 回封面 It's a small yet efficient tool to decrypt PDF hles protected with 每 Book Cover 添加至文件夹 owner passwords It allows you to PDF Password Remover X☒ Half-Title remove PDF restrictions on editing. copying.printing and more in i Raxtrict ians ranoved xuceaxfully. 国引用 Iitle seconds. Copyright 居中出 Table of Contents 日永久链接 Contributors Introduction □Select all Add Del Clear 中共享 田LAcces8 Contro Output Folder ⊙The same as source fok址e Start 雨Telecommunicatio Custome C:\Program Fles\PDF Password Remover 田业Sec1 rity Manageme过 Malicious hacking has been a successful means of undermining information controls and an in asing challe on.Hacke Practices tend to chip aw an organizat on tar too many ave led te highly publicized seenarios;for example,the recent defacement of the U.S.Department 下钱比电子图书(离线) 1→ ebscohost.pdf 显示所有下载皮容, 网络环境下的文科信息检索 201914/9 24
网络环境下的文科信息检索 2019/4/9 24 解密成功!