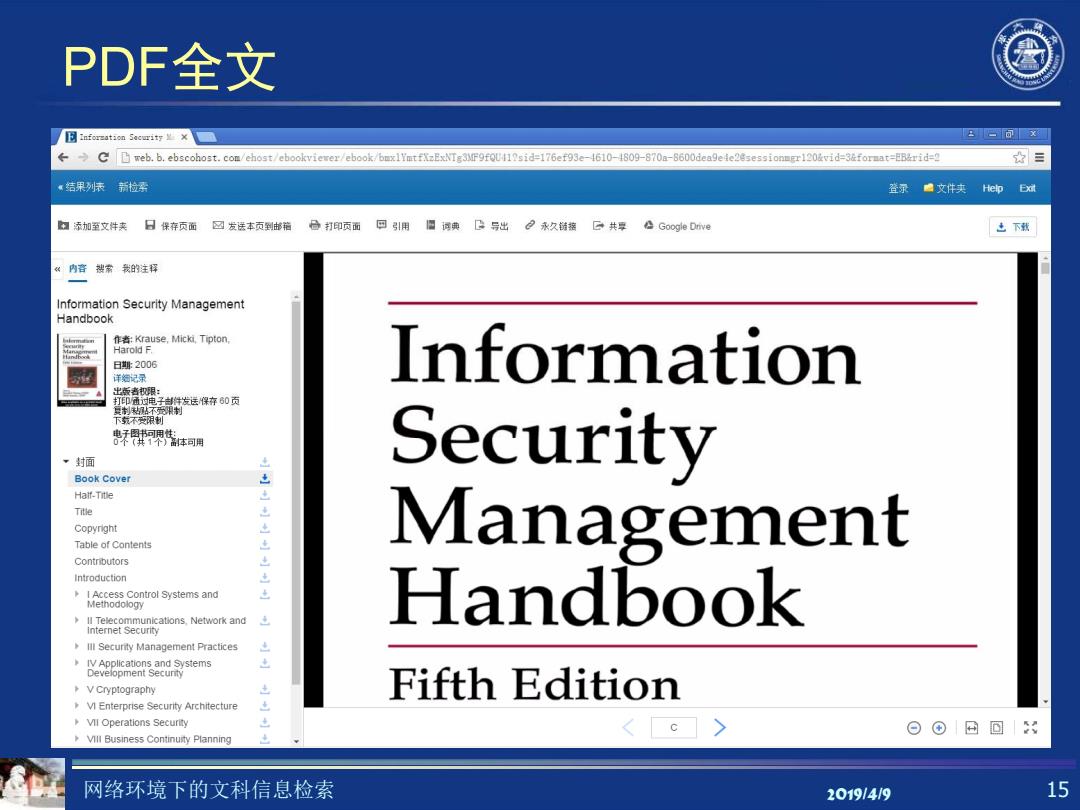
PDF全文 月Inforeation Security生X -可x eDweb.b.ebscohost.com/ehost/ebookvierer/ebook/buxlYmtfXzExNTg3MF9fQU41?sid=176ef93e-1610-1809-870a-8600dea9ele2esessionmgr120%vid=3&format=EB&rid=2 ☆三 :结果列:新检柔 登录赠文件夹Hep Exit 幻添加至文件夹 日保存页面 ☑发送本页到邮箱 合打印页面回引用圆词典上导出2永久铺接G共平公Go0 gle Drive 志下载 《内容费常我的注择 Information Security Management Handbook 作者:Krause,Micki.Tipton, Harold F. 日身:2006 详始记录 Information 出点者初限: 打印通过电子甘件发送保存60页 莫制材不西明制 下统不受限利 智生体可用 ·封面 Security Book Cover 点 Half-Title Title Copyright Table of Contents Management Contributors Introduction I Access Control Systems and Methodology Handbook ll Telecommunications,Network and internet Security Ill Security Management Practices IV Applications and Systems Development Secunty VCryptography Fifth Edition VI Enterprise Security Architecture VIl Operations Security c> ⊙⊙©回 VIll Business Continuity Planning 网络环境下的文科信息检索 201914/9 15
网络环境下的文科信息检索 2019/4/9 15 PDF全文
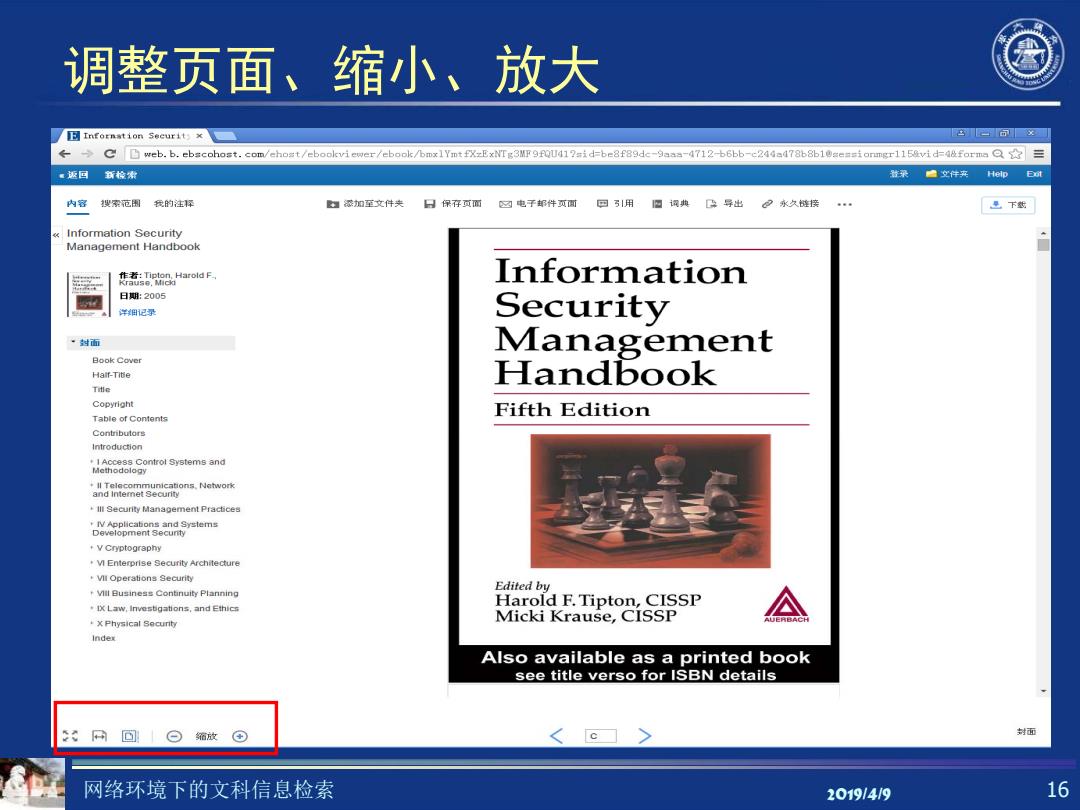
h 调整页面、缩小、放大 目Infornation Seeur1t)× x ←→ CDweb.b.ebscohost.com/ehost/eboolcviewer/ebookc/bmxlYmt fXzExNTg3MF9fQU41?sid=be8f89dc-9aas-4712-b6bb-c244a478b8b1@sessionmgr1158vid=4&forma 返回 新检索 登录。文件平Hep 内容搜索范围我的注释 添加至文件失 日保存页面☒电千邮件页面回引用。陋词典导出2水久链接· 是下数 Information Security Management Handbook 作煮e88,Harold F.. Information 日:2005 详细记录 Security ·过面 Management Book Cover Haif-Tite Handbook Title Copyright Fifth Edition Table of Contents Contributors Introduction I Access Control Systems and Methodology +ll Telecommunications,Network and Intemet Security .lll Security Management Practices I Applicabons and Systems Development Secunty v Cryptography .V Enterprise Security Architecture VIl Operations Security Vll Business Continuity Planning Edited by ·以Law,Invesbgations,and Ethics Harold F.Tipton,CISSP X Physical Security Micki Krause,CISSP Index Also available as a printed book see title verso for ISBN details :同回⊙缩放⊙ c 封面 网络环境下的文科信息检索 20191419 16
网络环境下的文科信息检索 2019/4/9 16 调整页面、缩小、放大
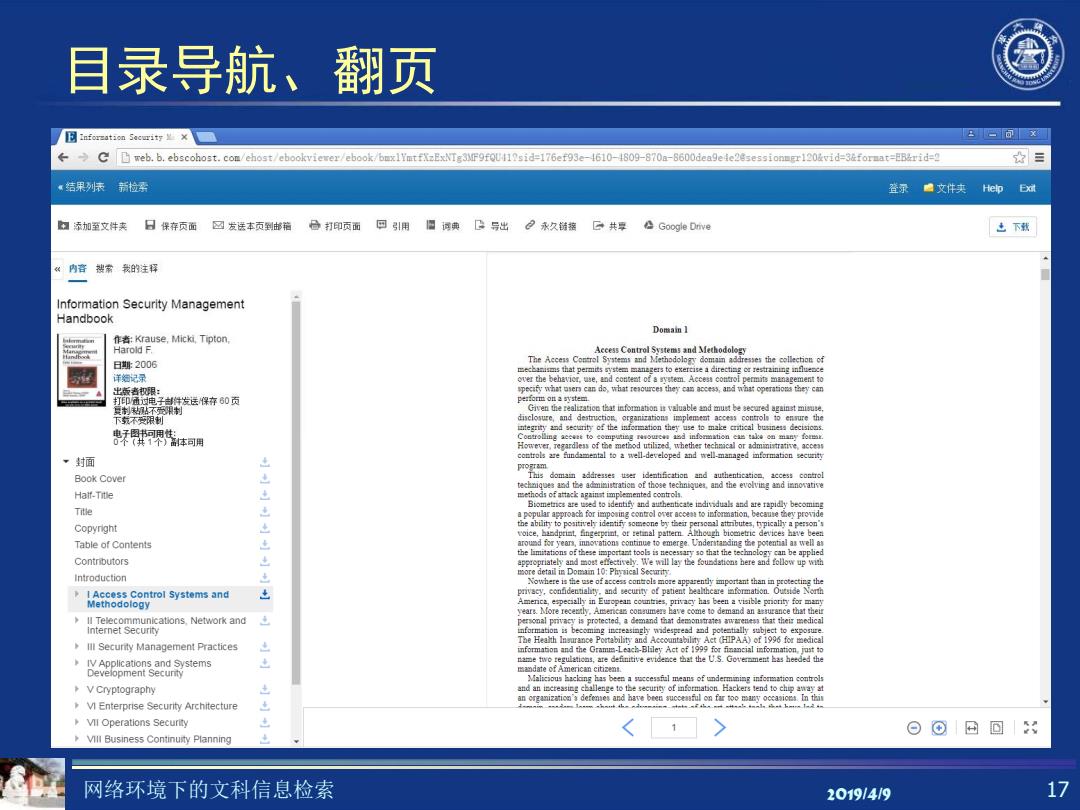
目录导航、翻页 月Inforzation Security¥X -可x eDweb.b.ebscohost.com/ehost/ebookvierer/ebook/buxlYmtfXzExNTg3MF9fQU11?sid=176ef93e-1610-1809-870a-8600dea9ede2esessionmgr120%vid=3&format=EB&rid=2 ☆三 ,结果列表新检季 登录赠文件夹 Help 中添加至文件夹 日保存页面回发送本页到邮箱合打印页面回引用日词典B号出2永久销接G共草公G00 gle Drive 志下载 保内音被常我的注择 Information Security Management Handbook Domain】 作者:Krause,Micki.Tipton, Harold F. 日期:2006 mechanisms that permits system managers to exertise a directing or restraining influence 详始记录 over the behavier,use,and content of a svetem.Access control permits management to 出板者限: 打印通过电子甘件发送保存60页 P流t26,r6rhy6c制69n的6cm 复荆材私不西制 下载不受限制 iscloure,md destruc中og0 rganizations implement acce特controls to ens四etht integrity and sectarity of the information they use to make critical business decisions. 智生体可用 Controlling aceese to computi2 NSSUCH1 inforation ean t:ae如mh时fee山h. However,regardleas of the metbod utilized,whether technical or administrative.acceas ·封面 controls are fundamental to a wvell-developed and well-managed iformation security program Book Cover This doma边2ds5esH1 dentification and authem山caticn,2 ccess co女rol techniques and the admimistration of those techniques.and the evolving and imnovative Halt-Title ethods of again时mpg mented controls. Title Copyright 753ep9 voice,hamdprint,fingerpeint.or retinal pattern.Alhough bicmetric devices have been Table of Contents yrvi tomerge Undertadingtenaw Contributors can be apph We will lay the oud here Introduction reda国D0mam10:PcS0度. Nowhere is the use of access controls more apparently important than in protecting the I Access Control Systems and Methodology aeae的dmd如r lI Telecommunications,Network and p0mpa择protecte4 a demand色时d四n4r2W2 eness that their me1ica internet Security nfarmation is becoming increasingly widesptead and potemttally subject to exposure. The Health Insurance Portability and Accountability Act (HIPAA)of 1996 for medical lll Security Management Practices IV Applications and Systems 出g Development Secunty mandate of American citizent. Malicious hacking has been a successfial means of undermining information controls ,V Cryp1 ography and an increasing challenge to the security of information.Hackers tend to chip away at VI Enterprise Security Architecture VII Operations Security 1 ⊙©©回 VIll Business Continuity Planning 网络环境下的文科信息检索 201914/9 17
网络环境下的文科信息检索 2019/4/9 17 目录导航、翻页
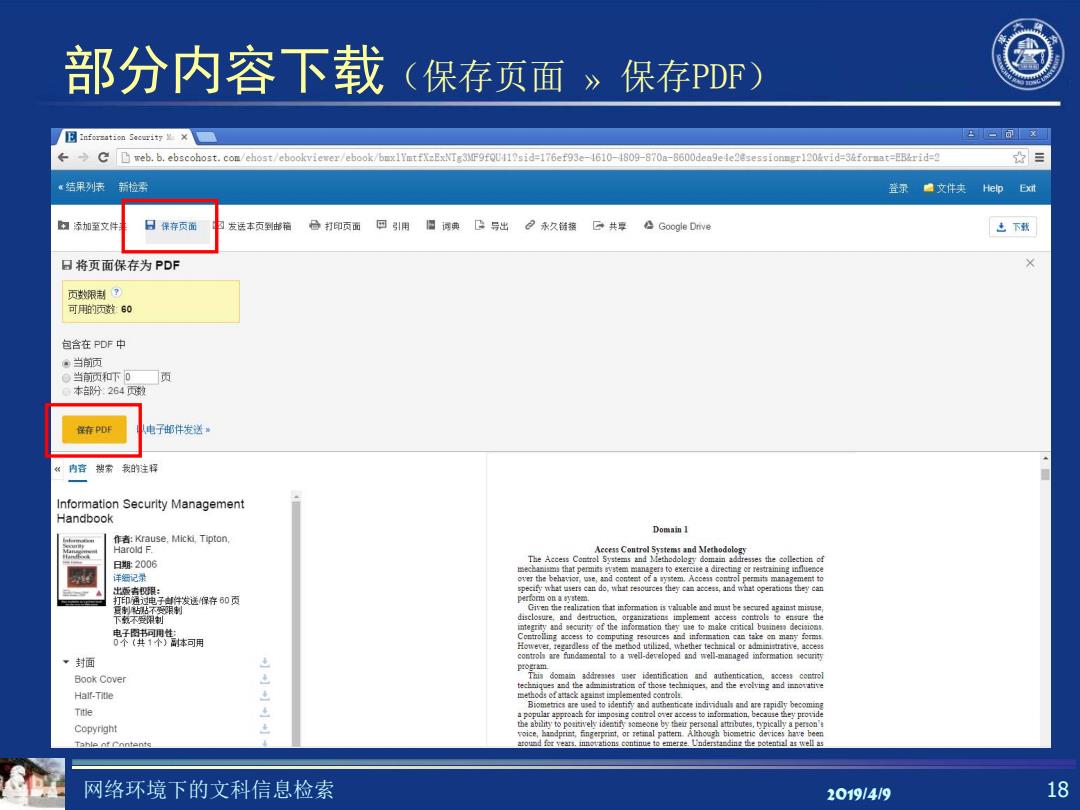
部分内容下载(保存页面 》保存PDF) Inforeation Security x -可x eDweb.b.ebscohost.com/ehost/ebookvierer/ebook/buxlYmtfXzExNTg3MF9fQU11?sid=176ef93e-1610-1809-870a-8600dea9ede2esessionmgr120%vid=3&format=EB&rid=2 ☆三 结果列表 新检柔 登录赠文件夹Hep Exit 中添加至文件 日保存页面 发送本页到邮箱合打印页面回引用日词典上号出2永久链接G共草公G00 gle Drive 志下载 日将页面保存为PDF 页数限制? 可用的列数:60 包含在PDF中 。当页 ⊙当质和下D页 本分264页数 保车PDF 电子邮件发送 内容搜我的注择 Information Security Management Handbook Domain I 作者:Krause,Micki,Tipton, Harold F. Access Control Systems and Methodology 日期2006 The Access Control Systems and Methodology domai addresses the collection of mechamisms that permits gvatem managers to exercite a directing or restraining influence 详细记录 出版者限: 打印通过电子件发送你存60页 Pion出on a yiter. Given the realization that information is valuable and must be secred against miause 下颗不受闲钊 disclosure.and destruction.organizations implement access controls to ensure the 电子图书同用性: 0个(共1个)体可用 、封面 controla are fundamental to a well-developed and well-managed iformation secunty Book Cover Half-Title 巴ethods ofattsck against implemented co如ic. Biometrics are ued to identify and authenticate individual and are rapidly becoming Title Copyright Tahle ot Contents. around for vears.innovations continue to emerge.Understanding the potential as well as 网络环境下的文科信息检索 20191419 18
网络环境下的文科信息检索 2019/4/9 18 部分内容下载(保存页面 » 保存PDF)
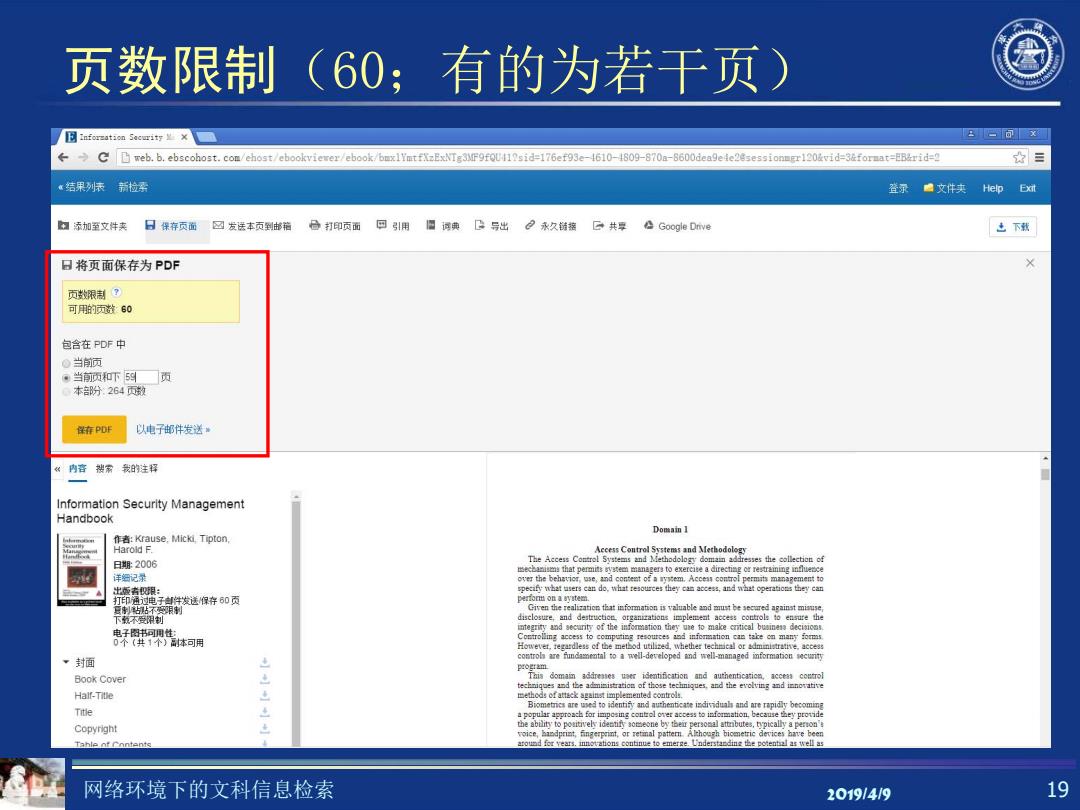
页数限制(60;有的为若干页) 月Inforzation Security¥X -可x eweb.b.ebscohost.com/ehost/ebookvierer/ebook/buxlYmtfXzExNTg3MF9fQU11?sid=176ef93e-1610-1809-870a-8600deagele2esessionmgr120%vid=3&format=EB&rid=2 ☆三 《结果列表新检季 登录赠文件夹Hep Exit 日添加至文件夹日保存页面回发送本页到邯箱合打印页面回引用圆词典B号出2永久销接G共平公G00 gle Drive 志下载 日将页面保存为PDF 页数限制? 可用的页数60 包含在PDF中 。当领 。当顶和下59页 6本部盼264面数 车PDF 以电子邮件发送。 内容搜常我的注择 Information Security Management Handbook Domain I 作者:Krause,Micki,Tipton, Harold F. Access Control Systems and Methodology 日期2006 The Access Control Systems and Methodology domai addresses the collection of mechamisms that permits gvatem managers to exercite a directing or restraining influence 详细记录 出版者限: 打印通过电子件发送你存60页 不限 Given the realizaticn that information is valuable and must be ecred against misuse 下颗不受闲钊 disclosure.and destruction.organizations implement access controls to ensure the 电子图书同用性: omaecmticealbwsimanc1iat 0个(共1个)体可用 、封面 controla are fundamental to a well-developed and well-managed iformation secunty Book Cover Half-Title methods of attsck against implemented controls. Biometrics are ued to identify and authenticate individual and are rapidly becoming Title Copyright 9e Tahle ot Contents. around for vears.innovations continue to emerge.Understanding the potential as well as 网络环境下的文科信息检索 20191419 19
网络环境下的文科信息检索 2019/4/9 19 页数限制(60;有的为若干页)