
Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Design Example Sender max.transmission rate of 200Mbps Router capacity is 16Mbps Application generates data in burst of 8Mb,with a burst length of 40ms,once every second. ☑ Application Router 200Mbps Leaky-Bucket 16Mbps 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.6
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.6 - Sender max. transmission rate of 200Mbps - Router capacity is 16Mbps - Application generates data in burst of 8Mb, with a burst length of 40ms, once every second. Application Leaky-Bucket Router 200Mbps 16Mbps Design Example

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Design Example First make sure the router can possibly handle the traffic: Average data rate generated by application is: Total 8Mb/1s 8Mbps router's capacity (16Mbps) Then determines Cfor the leaky bucket: 200Mbps →16Mbps Let A be arrival rate,and Tbe burst length (in seconds),then C>max{(total received in time f)-(total tx in time )Vf =A*t-*t=(A-0t =(200-16)*0.04 =7.36Mbor0.92MB 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.7
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.7 Design Example • First make sure the router can possibly handle the traffic: • Then determines C for the leaky bucket: Average data rate generated by application is: Total = 8Mb/1s = 8Mbps < router’s capacity (16Mbps) 200Mbps 16Mbps C Let A be arrival rate, and T be burst length (in seconds), then C max{(total received in time t)-(total tx in time t)|"t} = A*t - r*t = (A-r)t = (200-16)*0.04 = 7.36Mb or 0.92MB
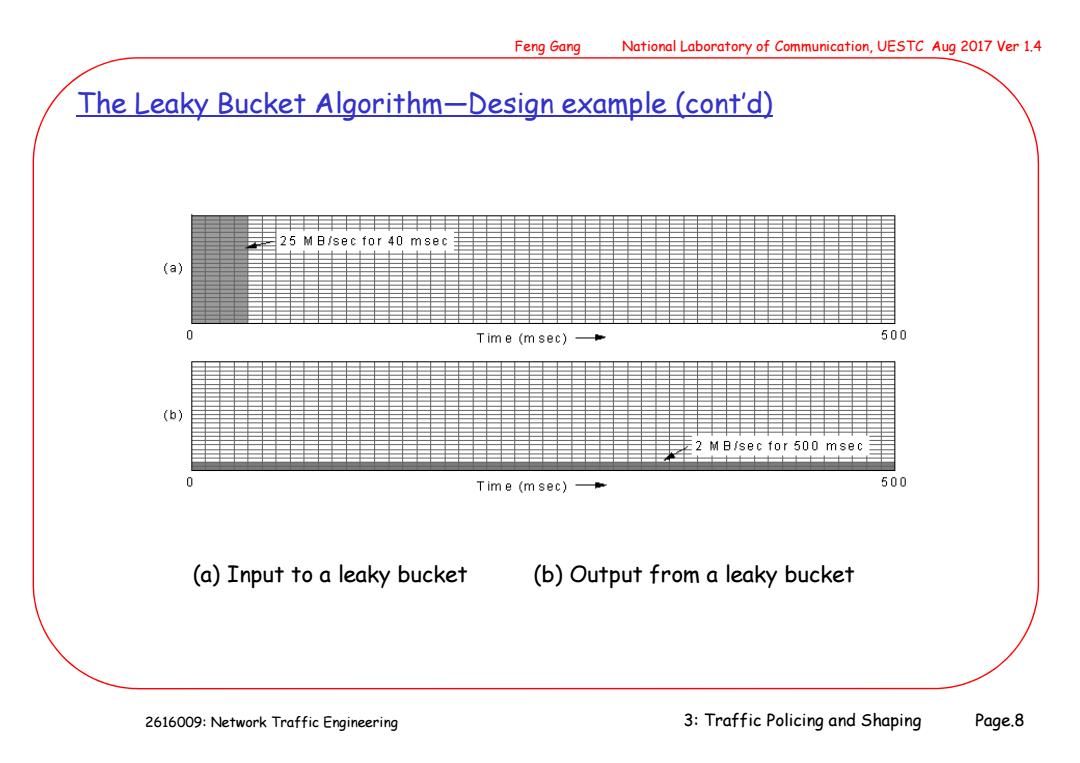
Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 The Leaky Bucket Algorithm-Design example (cont'd) 目 25M日/sec for40msec (a】 Tim e (m sec)- 500 (b) 2M日sec for500msec Tim e (m sec) 500 (a)Input to a leaky bucket (b)Output from a leaky bucket 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.8
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.8 The Leaky Bucket Algorithm—Design example (cont’d) (a) Input to a leaky bucket (b) Output from a leaky bucket