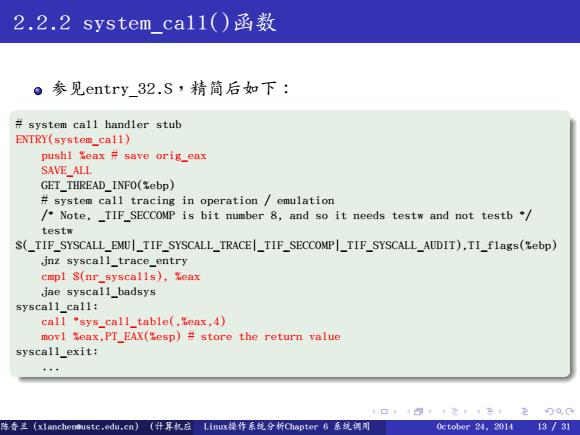
2.2.2 system_ca11()函数 ●参见entry32.S,精简后如下: #system call handler stub ENTRY(system_cal1) pushl Seax save orig_eax SAVE_ALL GET_THREAD_INFO(%ebp) #system call tracing in operation emulation /Note,_TIF_SECCOMP is bit number 8,and so it needs testw and not testb testw S(_TIF_SYSCALL_EMUI_TIF_SYSCALL_TRACE_TIF_SECCOMPI_TIF_SYSCALL_AUDIT),TI_flags(%ebp) jnz syscall_trace_entry cmpl S(nr_syscalls),Seax jae syscall_badsys syscall_call: call 'sys_call_table(,%eax,4) movl Seax,PT_EAX(%esp)#store the return value syscall_exit: 4口4四1是14P刀00 陈香兰(x1 anchenoustc,edu,cn)(计算丸应Linux操作系统分折Chapter书系统码用 0 ctober24.201413/31
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2.2.2 system_call()函数 参见entry_32.S,精简后如下: . . # system call handler stub ENTRY(system_call) pushl %eax # save orig_eax SAVE_ALL GET_THREAD_INFO(%ebp) # system call tracing in operation / emulation /* Note, _TIF_SECCOMP is bit number 8, and so it needs testw and not testb */ testw $(_TIF_SYSCALL_EMU|_TIF_SYSCALL_TRACE|_TIF_SECCOMP|_TIF_SYSCALL_AUDIT),TI_flags(%ebp) jnz syscall_trace_entry cmpl $(nr_syscalls), %eax jae syscall_badsys syscall_call: call *sys_call_table(,%eax,4) movl %eax,PT_EAX(%esp) # store the return value syscall_exit: ... 陈香兰(xlanchen@ustc.edu.cn) (计算机应用教研室 Linux操作系统分析Chapter 6 系统调用 @计算机学院嵌入式系统实验室@苏州研究院中国科学技术大学Fall 2014) October 24, 2014 13 / 31
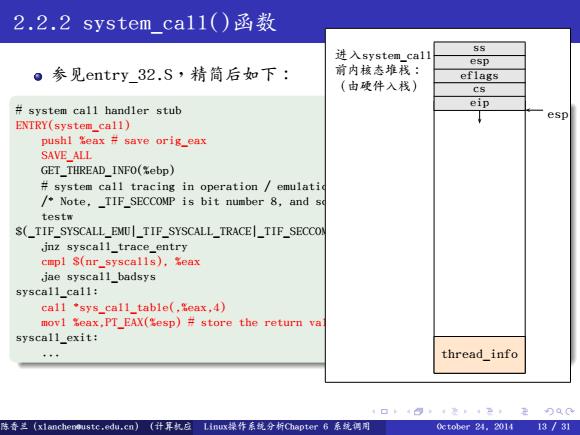
2.2.2 system ca11()函数 进入system_ca11 55 ●参见entry32.S,精简后如下: 前内核态堆栈: esp eflags (由硬件入栈) cs system call handler stub eip esp ENTRY(system_call) pushl Seax save orig_eax SAVE_ALL GET_THREAD_INFO(%ebp) system call tracing in operation emulatic /Note,_TIF_SECCOMP is bit number 8,and s testw S(TIF_SYSCALL_EMUITIF_SYSCALL_TRACETIF_SECCON jnz syscall_trace_entry cmpl $(nr_syscalls),%eax jae syscall_badsys syscall_call: call "sys_call_table(,%eax,4) movl Seax,PT_EAX(Sesp)#store the return va syscall_exit: thread_info 1口t4四,¥是42,在)QC 陈香兰(x1 anchenoustc,edu,cn)(计界丸应【inx操作系统分析Chapter书系统码用 (ctober 24.2014 13/31
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2.2.2 system_call()函数 参见entry_32.S,精简后如下: . . # system call handler stub ENTRY(system_call) pushl %eax # save orig_eax SAVE_ALL GET_THREAD_INFO(%ebp) # system call tracing in operation / emulation /* Note, _TIF_SECCOMP is bit number 8, and so it needs testw and not testb */ testw $(_TIF_SYSCALL_EMU|_TIF_SYSCALL_TRACE|_TIF_SECCOMP|_TIF_SYSCALL_AUDIT),TI_flags(%ebp) jnz syscall_trace_entry cmpl $(nr_syscalls), %eax jae syscall_badsys syscall_call: call *sys_call_table(,%eax,4) movl %eax,PT_EAX(%esp) # store the return value syscall_exit: ... 进入system_call 前内核态堆栈: (由硬件入栈) ss esp eflags cs eip thread_info esp 陈香兰(xlanchen@ustc.edu.cn) (计算机应用教研室 Linux操作系统分析Chapter 6 系统调用 @计算机学院嵌入式系统实验室@苏州研究院中国科学技术大学Fall 2014) October 24, 2014 13 / 31