
Windows NT Security Components 4 Security User 1 Logon Process Account Accounts Manager (SAM) Database Security Policy Win32 Database Application 2 Local Security Authority Audit Win32 Log Subsystem User Mode Security Policy Audit Messages Kernel Mode NT Executive Services Security Reference Monitor From: http://www.windowsecurity.com/whitepapers/Netwo rk_Strategy_Report_Windows_NT_Security.html
12/90 Windows NT Security Components From: http://www.windowsecurity.com/whitepapers/Netwo rk_Strategy_Report_Windows_NT_Security.html 1 2 4

Vindows NT的安全模型 Windows NT的安全模型包括5个主要部分 >登录(WinLogon) >本地安全认证子系统(LSA) >msv1 0 >安全帐户管理器(SAM) >NT LAN Manager(NTLM) 。 嵌入式系统实验室 13/90 EMBEDDED SYSTEM LABORATORY SUZHOU INSTITUTE FON ADVANCED STUDY OF USTC
13/90 Windows NT的安全模型 ❖Windows NT的安全模型包括5个主要部分 ➢登录(WinLogon) ➢本地安全认证子系统(LSA) ➢msv1_0 ➢安全帐户管理器(SAM) ➢NT LAN Manager(NTLM)
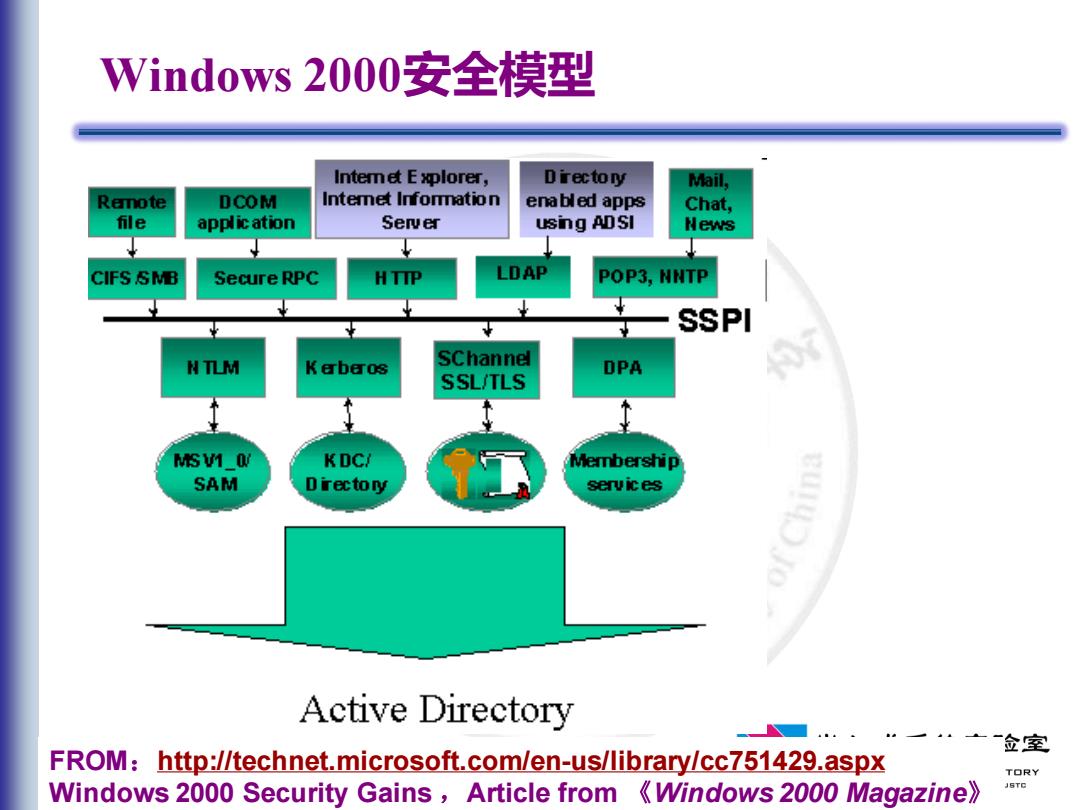
Vindows2000安全模型 Intemet E xplorer, Directory Mail, Remote DCOM Intemet Infommation enabled apps Chat, file applic ation Server using ADSI News CIFS SMB Secure RPC HTIP LDAP POP3,NNTP SSPI NTLM K erberos SChannel DPA SSL/TLS MSV1 0/ KDC/ Membership SAM Directory services Active Directory FROM:http://technet.microsoft.com/en-us/library/cc751429.aspx TORY Windows 2000 Security Gains Article from Windows 2000 Magazine) JSTC
14/90 Windows 2000安全模型 FROM:http://technet.microsoft.com/en-us/library/cc751429.aspx Windows 2000 Security Gains ,Article from 《Windows 2000 Magazine》

Vindows安全性组件 安全引用监视器,SRM ”本地安全认证 ·LSA策略数据库 大 ?安全帐号管理器服务 ·SAM数据库 1958 必默认身份认证包 冬登录进程 必网络登录服务 Science and Technolooyof china 嵌入式系统实验室 15/90 EMBEDDED SYSTEM LABORATORY SUZHOU INSTITUTE FON ADVANCED STUDY OF USTC
15/90 Windows安全性组件 ❖安全引用监视器,SRM ❖本地安全认证 ❖LSA策略数据库 ❖安全帐号管理器服务 ❖SAM数据库 ❖默认身份认证包 ❖登录进程 ❖网络登录服务
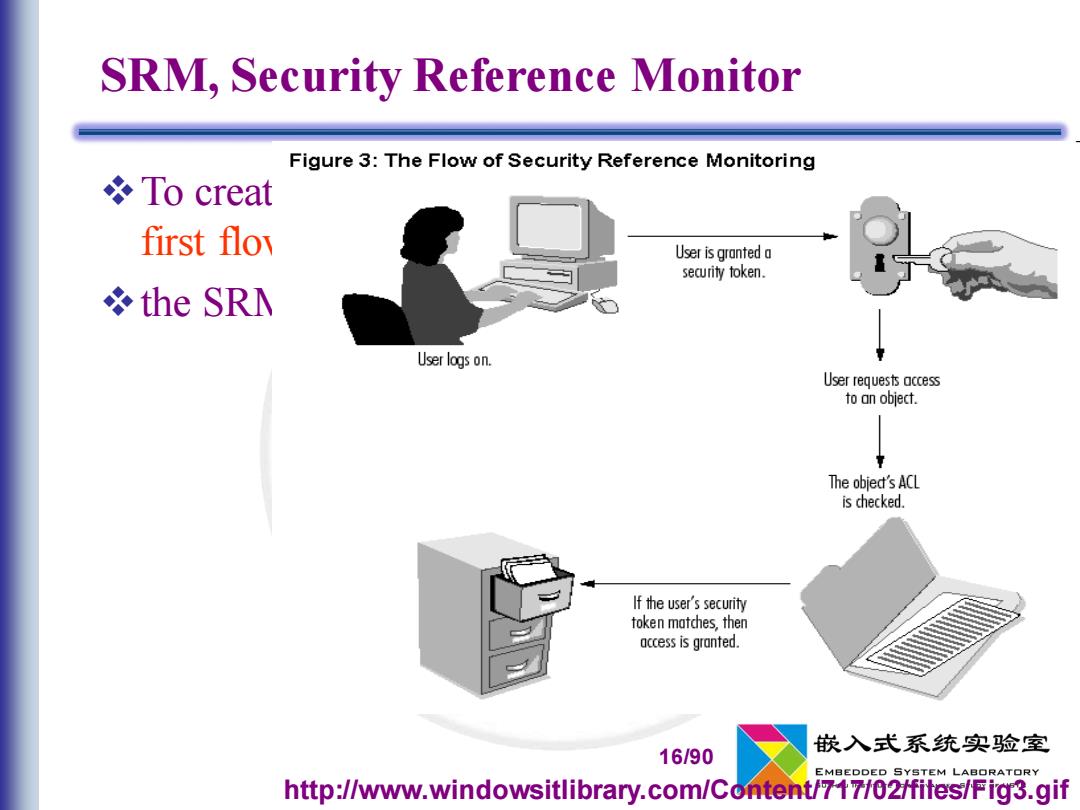
SRM,Security Reference Monitor Figure 3:The Flow of Security Reference Monitoring To creat first flov User is granted a security token. *the SRM User logs on. User requests access to an object. The objedt's ACL is checked. If the user's security token matches,then access is granted. 嵌入式系统实验室 16/90 EMBEDDED SYSTEM LABORATORY http://www.windowsitlibrary.com/Content/717/02/fites/Fig3.gif
16/90 SRM, Security Reference Monitor ❖To create or gain access to an object, a request must first flow through the SRM ❖the SRM operates in both kernel and user modes http://www.windowsitlibrary.com/Content/717/02/files/Fig3.gif