
信号举例:异常 前面讲过,异常也是通过信号来实现的。 ?当程序发生除0错误或是有非法指令时,将引起一 个内核态的trap。 冬内核trap处理程序识别出这个异常并发送合适的信 号到当前进程。 1958 当trap处理程序将要返回到用户态时,会检查并发 现信号,进程可能就会被终止。 Cience and Tecn 嵌入式系统实验室 2023/7/14 Linux OS analysis 12158 EMBEDDED SYSTEM LABORATORY SUZHOU INSTITUTE FON ADVANCED STUDY OF USTC
2023/7/14 Linux OS analysis 12/58 信号举例:异常 ❖前面讲过,异常也是通过信号来实现的。 ❖当程序发生除0错误或是有非法指令时,将引起一 个内核态的trap。 ❖内核trap处理程序识别出这个异常并发送合适的信 号到当前进程。 ❖当trap处理程序将要返回到用户态时,会检查并发 现信号,进程可能就会被终止
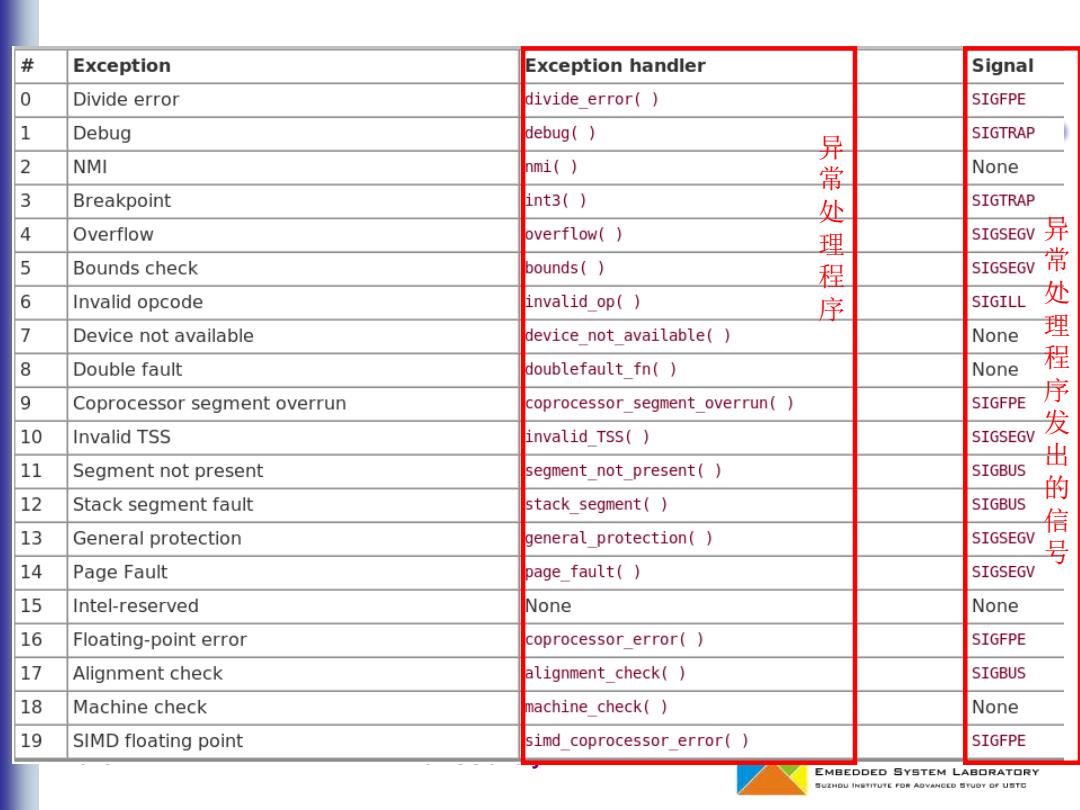
# Exception Exception handler Signal 0 Divide error divide error() SIGFPE 1 Debug debug( SIGTRAP 2 NMI nmi() 3 Breakpoint int3() 4 Overflow overflow( 异常处理程序 None SIGTRAP SIGSEGV 异 5 Bounds check bounds( SIGSEGV 6 Invalid opcode invalid op( SIGILL 处 7 Device not available device not available() None 8 Double fault doublefault fn() None 程 9 Coprocessor segment overrun coprocessor segment overrun() SIGFPE 序 10 Invalid TSS invalid TSS( SIGSEGV 发 出 11 Segment not present segment not present() SIGBUS 12 Stack segment fault stack segment( SIGBUS 信 13 General protection general protection() SIGSEGV 14 Page Fault page fault( SIGSEGV 15 Intel-reserved None None 16 Floating-point error coprocessor error( SIGFPE 17 Alignment check alignment check( SIGBUS 18 Machine check machine check() None 19 SIMD floating point simd coprocessor error() SIGFPE EMBEDDED SYSTEM LABORATORY SUZHDU INSTITUTE FOR AOVANCED SFUOY OF USTC
2023/7/14 Linux OS analysis 13/58 异常处理程序 异常处理程序发出的信号
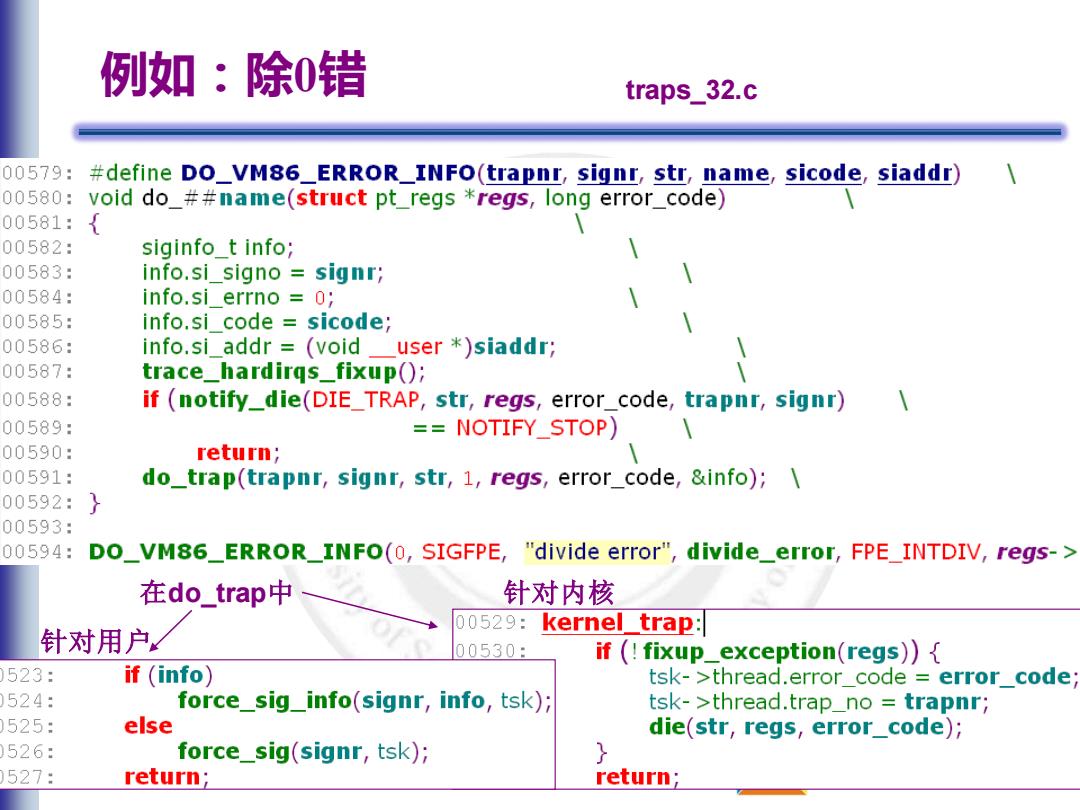
例如:除0错 traps_32.c 00579: #define DO_VM86_ERROR_INFO(trapnr,signr,str,name,sicode,siaddr) 00580: void do_##name(struct pt_regs *regs,long error_code) 00581: 00582: siginfo t info; 00583: info.si_signo signr; 00584: info.si errno =0; 00585: info.si_code sicode; 00586: info.si_addr =(void user *)siaddr; 00587: trace_hardirqs_fixup(); 00588: if (notify_die(DIE_TRAP,str,regs,error_code,trapnr,signr) 00589: =NOTIFY_STOP) 00590: return; 00591: do_trap(trapnr,signr,str,1,regs,error_code,&info);\ 00592: 00593: 00594: DO_VM86_ERROR_INFO(0,SIGFPE,"divide error",divide_error,FPE_INTDIV,regs-> 在do_trap中 针对内核 00529: kernel 针对用户 trap: 00530: if (fixup_exception(regs)){ 523: if (info) tsk->thread.error_code error_code 524: force_sig_info(signr,info,tsk); tsk->thread.trap_no trapnr; 525: else die(str,regs,error_code); 526: force_sig(signr,tsk); 527: return; return
2023/7/14 Linux OS analysis 14/58 例如:除0错 traps_32.c 在do_trap中 针对内核 针对用户
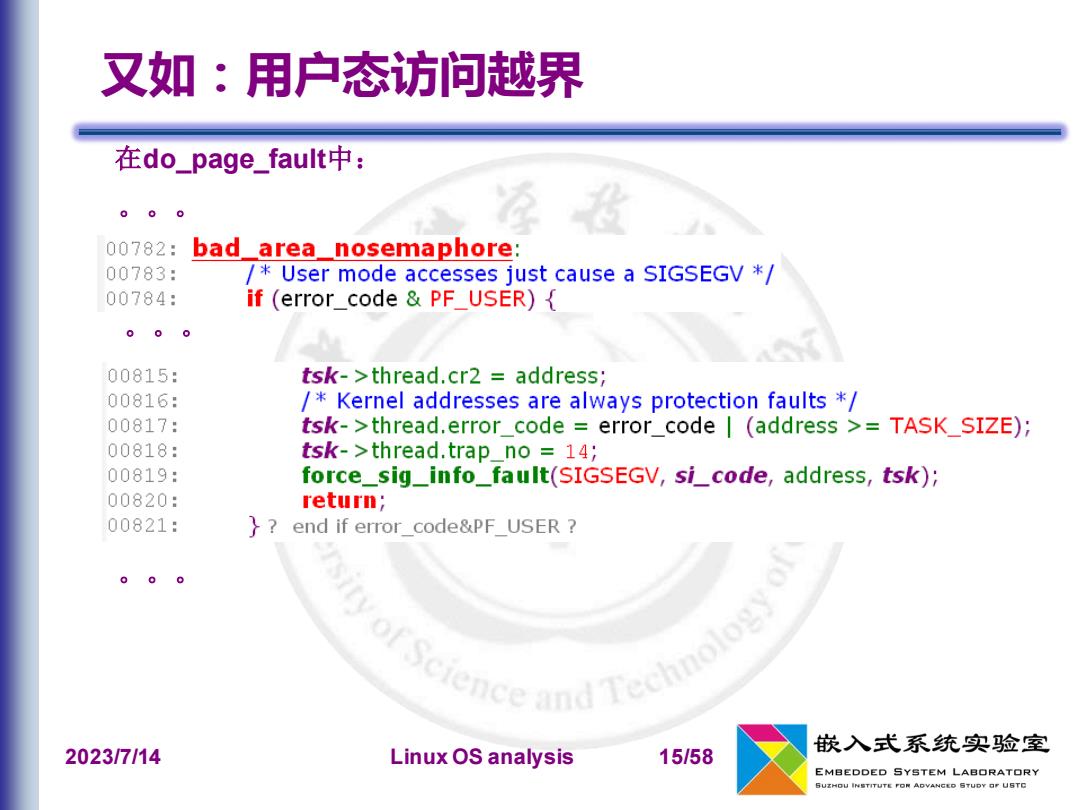
又如:用户态访问越界 在do_page_fault中: 00782: bad area nosemaphore: 00783: /User mode accesses just cause a SIGSEGV * 00784: if (error_code PF_USER) 0 00815: tsk->thread.cr2 address; 00816: /Kernel addresses are always protection faults * 00817: tsk->thread.error code error code (address >TASK_SIZE) 00818: tsk->thread.trap no 14; 00819: force_sig_info_fault(SIGSEGV,si_code,address,tsk); 00820: return; 00821: }? end if error code&PF USER F Science and Techno10入 嵌入式系统实验室 2023/7/14 Linux OS analysis 15/58 EMBEDDED SYSTEM LABORATORY SUZHOU INSTITUTE FON ADVANCED STUDY OF USTC
2023/7/14 Linux OS analysis 15/58 又如:用户态访问越界 在do_page_fault中: 。。。 。。。

与信号相关的系统调用 System call Description kill( Send a signal to a thread group tkill() Send a signal to a process tgkill()) Send a signal to a process in a specific thread group sigaction() Change the action associated with a signal signal() Similar to sigaction() sigpending() Check whether there are pending signals sigprocmask() Modify the set of blocked signals sigsuspend() Wait for a signal rt sigaction() Change the action associated with a real-time signal rt_sigpending() Check whether there are pending real-time signals rt sigprocmask( Modify the set of blocked real-time signals rt sigqueueinfo( Send a real-time signal to a thread group rt sigsuspend() Wait for a real-time signal rt sigtimedwait( Similar to rt sigsuspend( 嵌入式系统实验室 2023/7/14 Linux OS analysis 16/58 EMBEDDED SYSTEM LABORATORY SUZHOU INSTITUTE FON ADVANCED STUDY OF USTC
2023/7/14 Linux OS analysis 16/58 与信号相关的系统调用